2 Chapter 2
Defending your Inbox, One Layer at a Time
Parshva Doshi
Darsh Patel
Megha Deshmukh
Aniruddha Panchwagh
EmailAlexis is a cybersecurity solution focused on defending email inboxes against phishing attacks. The study focuses on the effectiveness of its phishing detection and mitigation strategies.
Reasons for Selection
Email remains a primary vector for cyberattacks, and phishing poses a significant threat to organisations. EmailAlexis offers an opportunity to evaluate innovative approaches to email security and contribute to the field of cybersecurity risk management.
Executive Summary
EmailAlexis is an email security solution to safeguard organisations against phishing attacks, one of the most serious email threats. This study evaluates its state-of-the-art detection, and prevention features to enhance organisational email security and prevent losses. EmailAlexis is a next-generation server-level solution utilising email authentication, blacklisted IP addresses, machine learning content analysis, and URL scanning to risk-classify emails. The study encompasses risk management, EU regulation compliance, and performance metrics. Recommendations are training, protocol review, and AI. Sharing threat intelligence and broader platform support will be covered in future work. EmailAlexis aims to enhance cyber resilience against phishing.
1. Introduction
This study aims to revolutionise how organisations defend against phishing attacks that are transmitted through email- the most prevalent and insidious cyber threat today. Its purpose is to filter out attempts at phishing and thus defend valuable data, decrease the risk of financial loss and avoid any damage to your company’s reputation. Researchers have built an innovative tool named EmailAlexis to spot and block phishing emails before they reach organisations. This innovative process protects data and ensures accurate communication, while also keeping companies safe from new types of cyber threats by dealing with risks upfront.
1.1 Background
Cybersecurity is a necessity due to the increasing demand for technology. With new technology and updates across domains, cybersecurity has been a necessity for organisations to operate smoothly. Organisations rely primarily on digital mediums to communicate, store data and carry out financial tasks. This elevates the organisation’s risk to cyber-attacks. Cybersecurity helps to ensure the confidentiality, integrity and availability of data stored in the organisations, thus increasing trust and safeguarding the privacy of users. Cybersecurity also prevents an organisation’s reputation from being damaged by protecting important assets from attacks.
Phishing attacks are still one of the most dangerous and regular threats online. In January 2021, over two million phishing sites were found, affecting both older and younger people and people of all social backgrounds by fraudulent means (Thomopoulos, Lyras and Fidas, 2024).
The aim of this study is to strengthen the methods used to detect malicious emails in organisations. Blacklisting is a security option where any email sender or IP listed as dangerous is permanently blocked to help avoid phishing actions. Combining different ways of detecting threats, the study aims to strengthen organisational email systems and cut down on the possibility of cyberattacks.
1.2 Objectives
Through phishing attacks cyber criminals trick people for giving away sensitive information and assets by creating deceptive messages that appear authentic. Attackers aim to trick users into revealing their sensitive information including passwords, PIN codes along with credit card details (Thomopoulos, Lyras and Fidas, 2024). In 2020, the IC3 received 791,790 complaints, including 241,342 phishing scams, 19,369 BEC cases, and 2,474 ransomware incidents through phishing attacks (American Hospital Association, 2021).
Attackers who exploit trust can gain unauthorised access to personal data through which victims experience financial losses or suffer other types of damage. The purpose of this study is to deal with phishing attacks through emails at the server level. It aims to design and implement EmailAlexis, an advanced email security solution aimed at detecting and mitigating phishing attacks before they reach users. This initiative seeks to enhance cybersecurity posture by implementing a multi-layered, risk management approach. As we aim to make our email services more secure, we analysed the email system carefully to spot possible areas attackers might use. To respond to these issues, we put filters on our servers that stop phishing emails from reaching users (Sahoo, Liu and C, 2017).
In addition, our system divided emails into phishing, legitimate and suspicious areas to ensure that the right response was taken for every situation. We further raised our defences by adding a hidden phishing approach that allowed us to track attackers through their IP addresses and where they were located. In addition to our technical steps, we underlined the importance of being security aware by training our colleagues on a regular basis and conducting regular risk checks of our cyber security protocols.
1.3 Scope
The study focuses on addressing phishing attacks, particularly those delivered via email in an organisation. It aims to improve cybersecurity by detecting and preventing phishing attempts before they reach users to protect sensitive information and reduce organisational financial loss and reputational damage. The research will examine methods to enhance data protection together with secure communication integrity and ensure security of sensitive user information by developing an innovative solution called “EmailAlexis”, a proactive, dynamic approach to detect and mitigate phishing emails. It addresses key cybersecurity risk management strategies by addressing vulnerabilities in emails, which is considered as a primary attack vector (Alsharnouby, Alaca and Chiasson, 2015).
The specific aspects of cybersecurity risk addressed in the study are detecting phishing attempts prior to user delivery while validating email authenticity to prevent spoofing (Rose et al., 2019) and constructing an IP address database to combat recurring phishing attempts (Sahoo, Liu and C, 2017). It also includes proactive measures for real-time detection, continuous monitoring and automated responses to phishing threats to improve overall security.
We looked for malicious emails at the outset, preventing threats from getting to the inboxes of our users. To enhance our security, we used email checks and verification to ensure no fake or unauthorised emails were stealing network access by checking email headers (Rose et al., 2019). Besides, we implemented threat intelligence by always having and updating a list of known harmful IP addresses which prevented many phishing emails. Proactive cybersecurity involves identifying threats as they happen, close observation in our systems and automated answers to safeguard our defence from phishing attacks.
2. Risk Identification
2.1 Asset Identification & Risk Register
Asset Identification is essential for risk management as it helps to understand security vulnerabilities, prioritise security measures, ensure regulatory compliance, and perform risk assessments (NIST, 2012). All organisational resources including hardware equipment, software systems and human assets serve as potential targets for attackers making identification crucial for mitigating risks.
The security of physical assets that includes servers and firewalls protecting emails requires robust access control systems to stop Illegitimate access. Furthermore, digital assets such as phishing detection models, machine learning models, and blacklisted IP repositories must be regularly updated and should be protected to avoid exploitation (Sahoo, Liu and C, 2017). Security training which is mandatory for human assets including security analysts, IT administrators and end users helps to reduce human errors while preventing outside threats.
A risk register helps organisations to manage and track assets, threats, vulnerability that results in better security compliance and protection. For instance, attack vulnerability occurs when SPF, DMARC and DKIM records are misconfigured thus servers become susceptible to attacks and need strict policy implementation. Data poisoning is always present because it represents a primary target of social engineering attacks, which is why organisations must provide ongoing security training to their employees. Regular security patches and updates help proactively mitigate phishing threats and enhance security (Rose et al., 2019).
2.2 Threat Identification
In EmailAlexis threat identification plays a vital role in blocking security threats aimed at email security. EmailAlexis faces four main threats which include phishing attacks and malware infections along with insider cyber-attacks and insecure user behaviour patterns. Phishing emails detect user vulnerabilities through weak filters to obtain sensitive information thus requiring advanced detection approaches. The security team identifies malware inside attachment files and malicious links using complete scanning together with sandboxing and antivirus defence protocols (Fishbein, 2023). The system named EmailAlexis protects users against phishing by performing email authenticity checks while engaging in content analysis to find malicious attempts.
Malware threats that exist within email attachments and links are thoroughly evaluated before EmailAlexis lets the content into its system. The company controls insider threats with strict security protocols to monitor employee behaviour while also implementing protocols to manage mistakes and phishing attacks. Security training and additional verification processes resolve the issues caused by weak security practices including substandard passwords and insufficient phishing detection abilities. The security method implemented in EmailAlexis promotes maximum effectiveness against its particular email security risks (SpamTitan Email Security, 2024).
2.3 Vulnerability Assessment
Phishing attacks have become the leading cyber threat by taking advantage of both human vulnerabilities and technical system weaknesses to steal sensitive information. Theft attacks target people’s emotions to trick them into sharing important personal data or finances. A person starts phishing when they send deceptive emails or messages pretending to be a trusted company leader or trustworthy institution. Thefts of personal data through these attacks cause people to lose money and expose their private details.
In 2024 research found that 64% of companies faced Business Email Compromise attack problems. When fraudsters pretend to be senior staff members their victims believe them and take damaging business actions like funds relocation or leaking sensitive data. The newest spying tricks of cybercriminals focus directly on workers who control money and handle vital corporate information (Baker and Cartier, 2024).
The phishing attack depends only on human behaviour. Attackers take advantage of human reaction and fear when they need personal information from their targets. When cyber attackers use phishing emails, they create a sense of urgency that pushes people to respond quickly before an account can get suspended. Stress from a sense of urgency makes the victim act without thinking which puts them at greater risk for the scam. Scammers use phishing to manipulate authority-based behaviour to gain victims’ trust. Effective phishing attacks often work by making an emotional impact that weakens defence mechanisms (Shloman, 2024).
2.4 Risk Scenarios
A realistic threat simulation takes place when an attacker pretends to be the CEO and sends a phishing email to the finance department. A fake domain is often built by adding a letter or extra word to the real domain name (for example, @fintrvst.com instead of @fintrust.com) to make the attack more successful. The message inside the email instructs the finance officer to immediately send a major amount of money into the account of a new vendor.
The attack is being done with Business Email Compromise (BEC) tactics
Vulnerability Exploited: Issues not detected through lack of domain checks and social engineering built into attacks using pressure and official titles. The focus of the attack in this threat is on email spoofing and phishing (Ic3.gov, 2022).
Response by EmailAlexis
Because the sender’s domain is nearly identical to the official company site, EmailAlexis marks it as suspicious. It compares the sender IP to its ongoing threat intelligence database and finds the IP address on the blocklist (Cisco, n.d.). The code for JavaScript is put into isolation before it arrives at the user’s computer. A notice is issued, and it is delivered to the cybersecurity team for more analysis. The finance workers are reminded during training to focus on marking emails that seem risky.
Because of EmailAlexis, the organisation was able to safely implement its key security principles of confidentiality, integrity and availability. Those attempting the phishing email did not get any sensitive material because the email was stopped in time. Because the suspicious email was blocked at the start, the integrity of the company’s financial systems was maintained without unauthorised access. Emails could be sent and received the whole time, allowing for the company’s smooth operations and smooth communication throughout the crisis (Baker and Cartier, 2024).
Outcome
Before any harm could happen, EmailAlexis identified and prevented the phishing email. The case demonstrated how well multi-layer phishing detection and domain verification works.
3. Risk Assessment
3.1 Risk Register & Analysis
Phishing involves deceptive emails designed to trick individuals into revealing sensitive information including login credentials, financial data like credit card details and personal details. Phishing emails can contain malicious links or attachments which can lead to malware installation. The main phishing vulnerabilities stem from human error due to lack of awareness or training, unauthenticated or unencrypted email communication and inadequate spam or phishing filtering in email systems. Additionally, a lack of or poorly enforced Multi-Factor Authentication (MFA) can lead to increased likelihood of account compromise (Day, 2024; Gallo et al., 2023).
The potential impacts of a phishing attack can be devastating. A data breach caused by phishing would reveal crucial information of both business and individual which poses threats to all assets. The organisations could lose financial assets through fraudulent transactions, wire transfers or ransom payments. Phishing can severely damage the organisation reputation which can cause losing customers’ trust and possibly triggering legal penalties. Business operations could be disrupted, particularly when important accounts are compromised because this leads to significant downtime and critical data loss. Moreover, A phishing attack can cause important business ideas and secret data theft which negatively affects the company’s future success. Lawsuits because of unprotected sensitive information could harm the organisation both legally and financially. Phishing attacks might open the door to more cyberattacks like ransomware or malware injection, leaving the company vulnerable for a long time.
3.2 Risk Evaluation
Phishing attacks are highly significant in the context of the organisation’s objective because protection of sensitive data and securing continuous operations and maintaining a positive reputation remain vital goals. Successful phishing attacks lead to both financial and legal problems that create harmful disruptions which compromise the organisation’s performance of its business tasks. Due to Widespread occurrence and growing complexity of phishing attacks the organisation has a low tolerance for this risk. The organisation recognises these security threats as unacceptable since they lack suitable preventive measures. The organisation’s ability to protect customer trust, intellectual property and operational efficiency stand as the direct focus of the organisation.
Phishing incidents need to be positioned as critical priorities because they are common attacks that create severe impacts. Phishing attacks maintain their position as a leading gateway for cyberattacks which leads to increased probabilities that such incidents will occur inside the organisation. Due to its high probability of occurrence and the potentially devastating impacts, phishing must be considered as a top priority inside the organisation to minimise the threats.
4. Risk Mitigation Strategies & Controls
4.1 Preventative Measures
As email threats continue to rise, EmailAlexis uses a full set of security steps to make it easier to detect, block and deal with cyberattacks in emails. The main function of the system is to validate email messages and stop fake messages from getting through.
EmailAlexis automatically applies the important email authentication rules known as SPF, DKIM and DMARC. Only though SPF does the email system allow approved IP addresses to send out messages under the domain, making it less likely that spammers can create fake messages. DKIM checks emails by adding a signature to make sure the message is authentic. DMARC uses SPF and DKIM as foundations, allowing the company to quarantine or reject unverified messages and then produce reports on how their email system has handled them (Rescorla and Dierks, 2008).
By default, email messages are protected in transit with Transport Layer Security (TLS) encryption. Thanks to TLS, email messages are shielded from interception and from being changed by attackers during their trip between servers (Rescorla and Dierks, 2008).
Advanced Threat Detection with MaliceSpotter
EmailAlexis includes its own threat detection tool, MaliceSpotter which is designed to find dangerous links hidden in received emails. To analyse emails, MaliceSpotter passes the URL through a four-step process, with the URL going through three different algorithms each picking up unique aspects of phishing. After all, the results are compared, and the final classifier assigns a phishing score to indicate if the URL should be trusted or avoided. This way, advanced phishing emails are detected automatically and handled before anyone opens the email.
Access Control and Endpoint Protection
All email logins with EmailAlexis require Multi-Factor Authentication (MFA) which helps secure your account even in case your password is exposed. Moreover, protecting all organisational devices and using antivirus software regularly helps reduce phishing attacks.
Network Monitoring and Firewalls
Emails and networks in EmailAlexis are kept safe by firewalls that detect abnormal traffic patterns that might mean an active phishing attack. They are designed to stop potentially dangerous traffic and prevent viruses from travelling across the network.
Policy, Awareness, and Simulation
The company has written rules outlining how suspicious emails should be managed. Employees learn what to watch for which includes suspicious emails from unfamiliar addresses, messages that seem too rushed or any file that is unexpected. Regular training and testing are used to monitor an organisation’s team’s preparedness. For instance, fake phishing attempts help spot those staff members who need further training on how to respond to scams by email (Wilson and Hash, 2003).
4.2 Detective Measures
Phishing is a form of a cyber-attack which is based on social engineering. It involves manipulating human emotions more as compared to technical aspects. Phishing involves clicking on a malicious link which compromises the entire system and allows the attacker to bypass any control. We can detect phishing attacks by verifying the legitimacy of the email and emphasise on a layered approach. A layered approach involves installing security protocols for all devices, network and endpoints in the existing system (NIST, 2020).
Another useful detection method which can be used to detect if any user’s account has been compromised. The principle of least privilege ensures only relevant access has been granted to the user based on the task. This makes sure that even in case of a breach the attacker cannot gain full access to the system.
Regularly update the system and ensure all the devices are also compatible with that particular update. This makes sure that the evolving phishing attacks are detected by the system and filtered out.
4.3 Corrective Actions & Incident Response
Once phishing has been realised, an organisation needs to follow a proactive approach and follow the steps below:
Identification:
Identify which user has been compromised and how they have been compromised. Find out the major source of incoming traffic to the organisation which have caused the attack to occur.
Did the phishing lead to credential theft, malware execution, or data exfiltration?
Classify the incident severity (Low/Medium/High/Critical).
Containment:
This stage involves disconnecting the affected system and disabling the compromised accounts. Remove the phishing email from the inbox by making use of email gateway tools. Also, the IP address from which the email was received needs to be blocked to prevent any further phishing emails.
Eradication:
This is the stage where the following tasks are to be performed:
Conduct full malware scans on affected endpoints.
Delete malicious files or payloads.
Revoke stolen credentials and reset passwords (preferably with MFA enforcement).
Review and remove any unauthorised account changes (forwarding rules, permissions).
Apply security patches and close exploited vulnerabilities. (NIST, 2020)
Recovery:
Restore systems and operations to a secure and normal state. Restore clean backups, if required (in case of malware infection). Re-enable user accounts after verifying systems are clean. Monitor affected systems for a defined period to detect any unauthorised activity. Resume business operations with executive approval (Egnyte.com, 2025).
4.4 Compliance Measures
EmailAlexis is designed to fully comply with major European Union regulations that govern data protection, cybersecurity, and the responsible use of artificial intelligence. These regulations ensure that organisations handling sensitive information do so in a secure, transparent, and accountable manner, thereby protecting individuals’ privacy and maintaining trust.
General Data Protection Regulation (GDPR):
The General Data Protection Regulations (GDPR) are new rules for data protection. The EU relies on GDPR to protect data by laying down tough rules for the collection, processing and storing of personal information. Because email communications can hold sensitive details such as names, telephone numbers, bank details and private discussions, EmailAlexis is important for GDPR support. Because phishing is a common way hackers gain unauthorised access to information, this method checks for and blocks those emails. By blocking malicious emails, EmailAlexis greatly lowers the chance of data breaches. Also, the system tracks complete records of spotted threats and how they are managed. Working with these records allows organisations to comply with the deadline for reporting a breach and makes audits by data authorities simpler (European Union, 2016).
Network and Information Security Directive (NIS2):
NIS2 is a new EU directive that expands the rules and raises the level of cybersecurity in critical areas such as energy, healthcare, transport and digital infrastructure. According to NIS2, essential or important organisations should implement effective risk management and must disclose major cybersecurity incidents right away. EmailAlexis helps you meet these responsibilities by checking your network in real time and quickly detecting any phishing or other cyber-attacks. NIS2 requires organisations to notify others about incidents within a set timeframe. With automatic alerts, reporting helps organisations achieve this and reduce likely obstacles (European Union, 2016).
Digital Operational Resilience Act (DORA):
Focusing on the financial sector, DORA requires that financial institutions are prepared for all kinds of IT disruptions and threats. The use of EmailAlexis makes it easier to meet DORA’s guidelines because it assesses risks continually and offers automatic safeguards against phishing, a leading cause of financial cybercrime. To keep financial institutions protected, the system is frequently examined and improved based on any issues. Using EmailAlexis, organisations strengthen their operations and lower the risk of large phishing-related breaches and fraud (European Union, 2016).
EU Artificial Intelligence Act:
The AI and machine learning used by EmailAlexis in phishing detection comply with the up-and-coming EU Artificial Intelligence Act. The goal of this law is to make AI applications transparent, keep them accountable and involve human oversight. EmailAlexis meets the standards by including explainable AI models that help us easily understand how it finds phishing messages. To ensure all decisions can be reviewed and validated, the system uses both audit trails and involves people in security roles. Automatic tools and practices are in place to avoid errors and biases in artificial intelligence detection which supports ethical behaviour (European Union, 2016).
5.Implementation and Monitoring
5.1 Implementation Plan
The implementation of EmailAlexis follows a structured and a multi-staged approach to detect and mitigate phishing emails at the server level. The implementation plan is designed to build the prototype in 10 weeks. The following flowchart outlines the core pipeline of EmailAlexis from start to deployment.
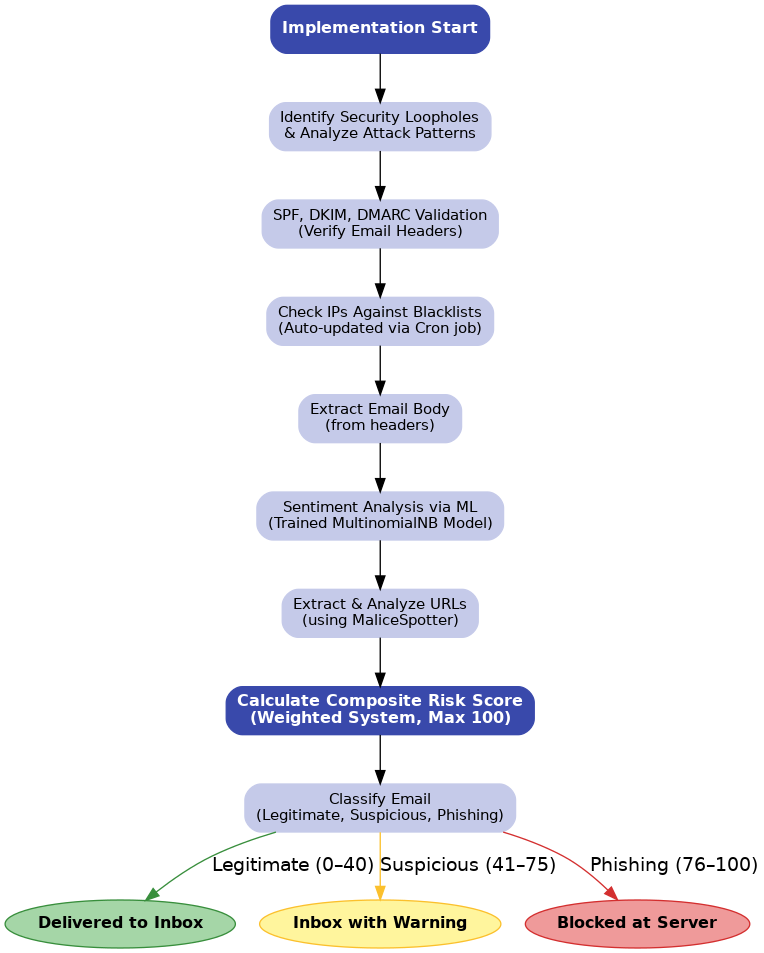
The first step of the plan is to identify the current security loopholes, and analyse phishing email attack patterns (Abdillah et al., 2022). We understand that the SSL on phishing websites is one of the attackers’ primary techniques to deceive their victims. As a result, we focus on checking the Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and the Domain-based Message Authentication, Reporting & Conformance (DMARC). This is necessary as SPF is like a guest list for emails. It helps prevent email spoofing by allowing domain owners to specify which mail servers are authorised to send emails on their behalf. DKIM is like a digital signature for your emails. It helps ensure that emails sent from your domain haven’t been tampered with during transit and verifies that they truly come from your domain. Lastly, DMARC is like a security policy for your emails. It helps domain owners decide what happens to emails that fail SPF and DKIM checks, preventing email spoofing and phishing attacks.
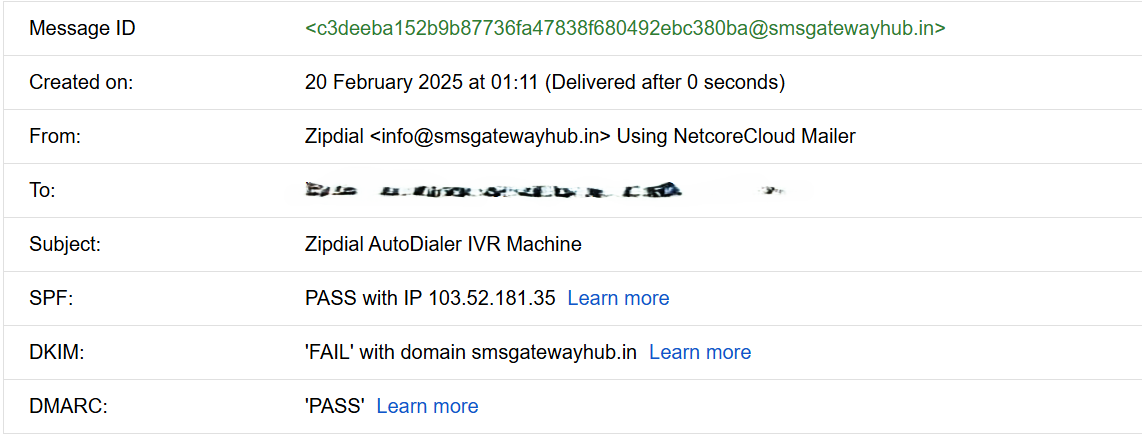
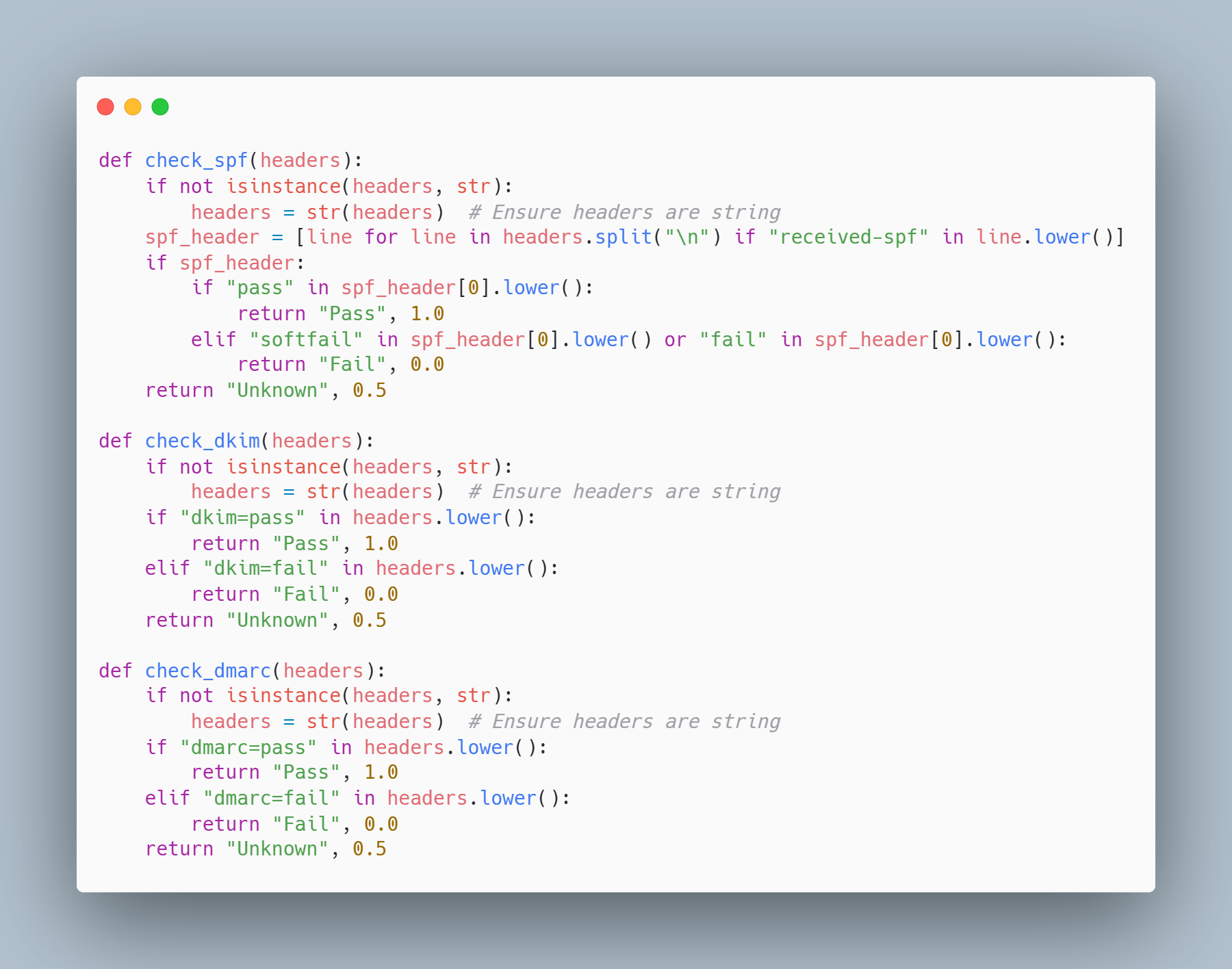
The above picture shows an example of the DKIM value being failed, which means that the message could have been tampered before it reached our inbox. Verifying these values becomes increasingly important, as they can indicate the legitimacy of an email. We do this by the following piece of code, where we specifically iterate through the obtained email headers and check their value.
The next step is to check the email for blacklisted IPs. We do this by referring to publicly available repositories of Blacklisted IPs. This can help us determine whether or not the email is coming from an already blacklisted source. Additionally, we use a Cron job on Linux to update the Blacklisted IPs after every one hour (bitwire-it, 2023).
Once the IPs are monitored, we move onto the actual email body. First, we pivot through the entire email headers and identify the email body in the headers. This is because every email service has its own dedicated email header layout. After this, we extract out the email body contents and send it to a Sentimental Analysis model based on Machine Learning.
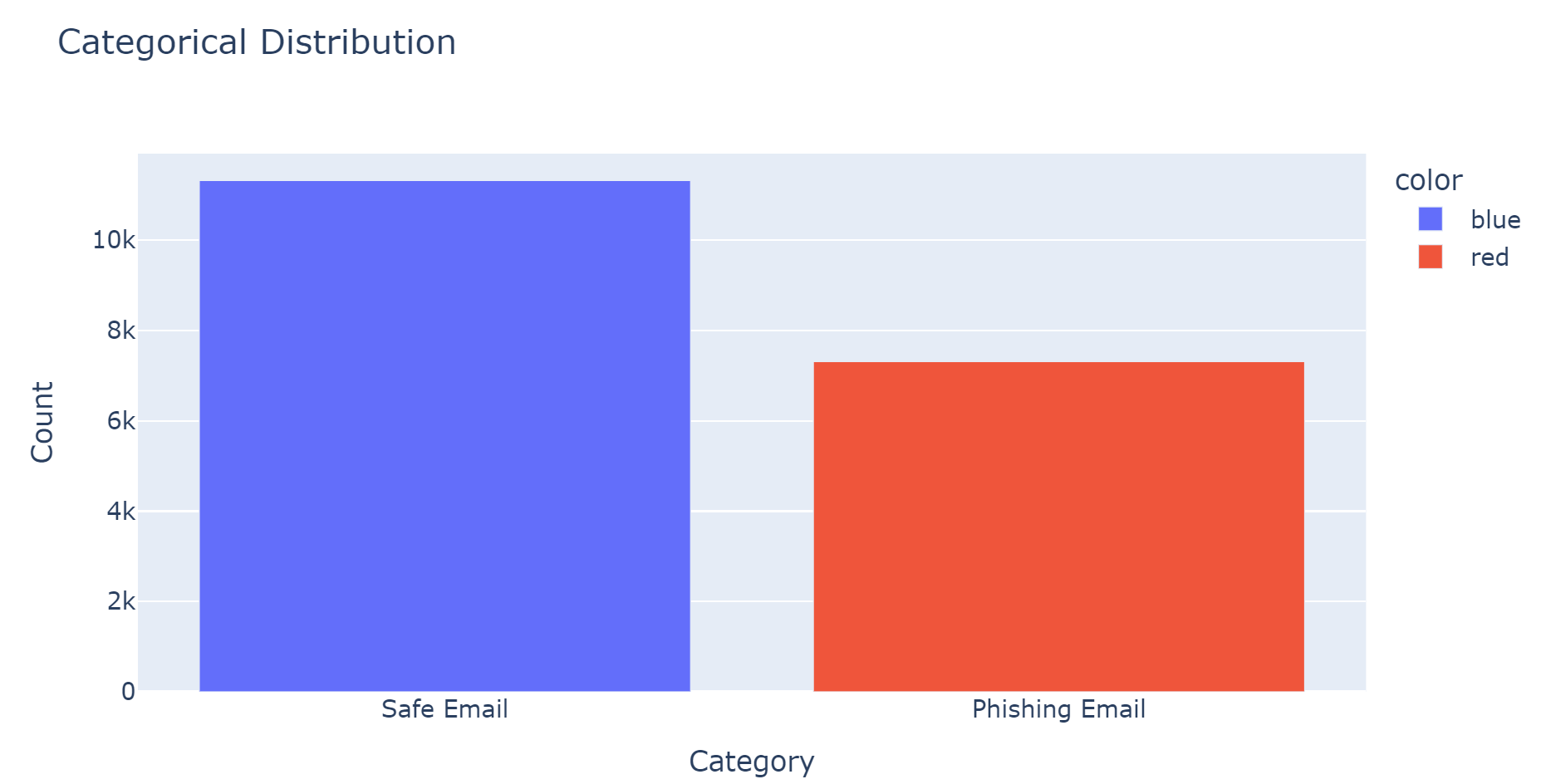
The Machine Learning model is backed by a hefty dataset that can classify the contents of an email into Safe and Phishing Email. The model is split into the two in the following manner:
Additionally, to test the quality of the dataset we proceed to check the Word Cloud of the dataset to identify the most commonly occurring words in the dataset. This also gives us a way to identify if the content in the dataset is useful. The below is the Word Cloud:

We have trained the model using MultinomialNB, which stands for Multinomial Naive Bayes, a Bayes’ Theorem-based classification algorithm for discrete data like text, models word frequency as counts using a multinomial distribution for each word. Upon training this model, we achieved an accuracy of 94.77%. This high accuracy means that any email with a malicious intent has a good chance of getting intercepted by the model.
Additionally, we also extract any URLs present in the email. URLs are the major attack medium in a phishing email. As a result, a detailed analysis for the same is necessary. To perform the detailed analysis, we leverage our inhouse project called MaliceSpotter. MaliceSpotter classifies user-entered URLs as malicious or benign by analysing 28 features. It employs Logistic Regression, Random Forest, and KNN algorithms, combining their predictions using a Voting Classifier. The project utilises a diverse dataset available on Kaggle for evaluation. Its novelty lies in the integration of multiple algorithms and the use of a Kaggle dataset (Borade, Doshi and Patel, 2024).
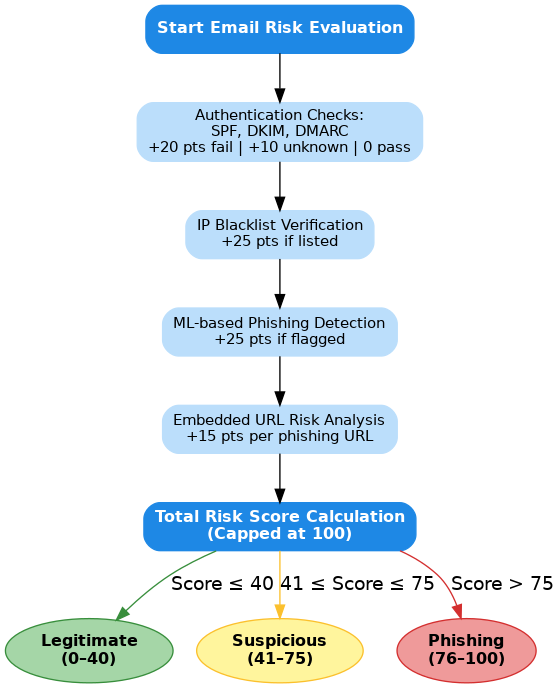
Once all individual checks are complete, the EmailAlexis system calculates a composite risk score to classify the email’s intent using a weighted scoring mechanism. The detailed scoring mechanism is explained below:
The total email risk score is derived from a weighted rule-based system that assesses specific indicators of authenticity and threat. Each indicator adds a predetermined number of points to the score, depending on the outcome. The cumulative score is capped at 100. The initial indicators include SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance). These protocols validate different aspects of sender identity. If any of these checks fail, 20 points are added per failure. An unknown result contributes 10 points, while a successful check adds none (Rose et al., 2019).
Next, the sender’s IP addresses are checked against known blacklists. If any match is found, 25 points are added. If no blacklist is triggered, no points are applied. The system then analyses the email’s content using a machine learning model trained to detect phishing. If the model flags the message as phishing, 25 points are added; if marked safe, the score remains unchanged. Finally, each embedded URL is assessed. For every URL identified as phishing, 15 points are added. Safe URLs have no impact on the score (Borade, Doshi and Patel, 2024). After processing all indicators, the final score is tallied and capped at 100. Based on this score, emails are categorised into three levels: 0–40 as ‘Legitimate,’ 41–75 as ‘Suspicious,’ and above 75 as ‘Phishing.’ This multi-layered approach provides a transparent, interpretable evaluation of email security, combining authentication, origin analysis, machine learning, and URL scanning into one comprehensive metric.
A visual explanation for the above risk scoring model is explained in the below image:
5.2 Results and Risk Matrix
Upon integrating all the modules together, we have a strong, resilient system that can easily scan and detect any malicious emails in just a few seconds. The final classification of an email is presented through a user-friendly interface. The interface visually distinguishes between legitimate, suspicious, and phishing emails based on the cumulative risk score calculated. Below are representative screenshots demonstrating how each classification is displayed:
- Safe Emails:
For this example, we will be using an Email that came in from the popular online shopping store called Notino. Below are the email headers from that email.
Upon sending these headers, through our system we quickly can identify the legitimacy of the email.
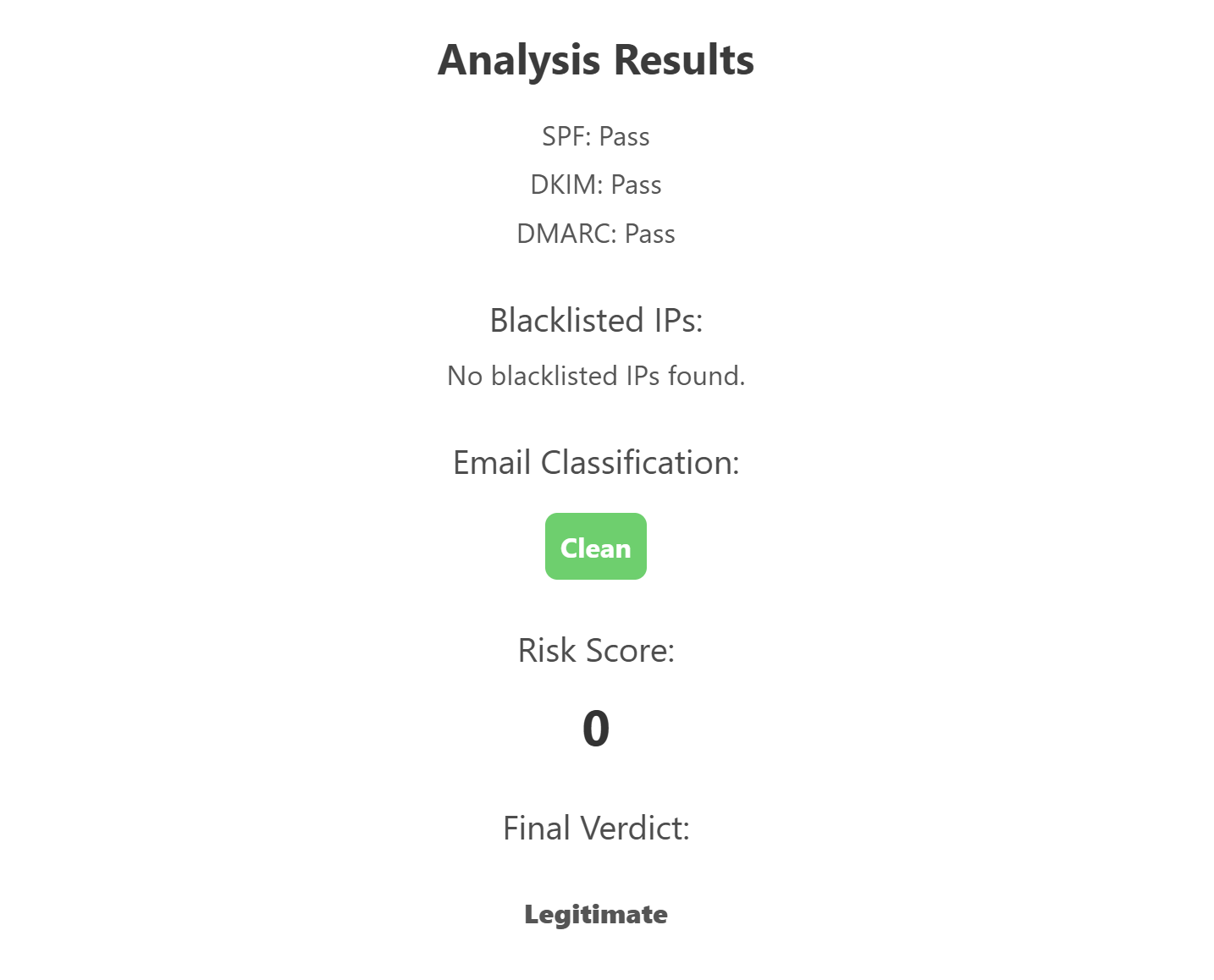
Additionally, every email analysed has a detailed risk register attached to it in the results. This risk register can help to classify the risks based on their severity and additionally also help to identify the portions that carry a risk in the email.
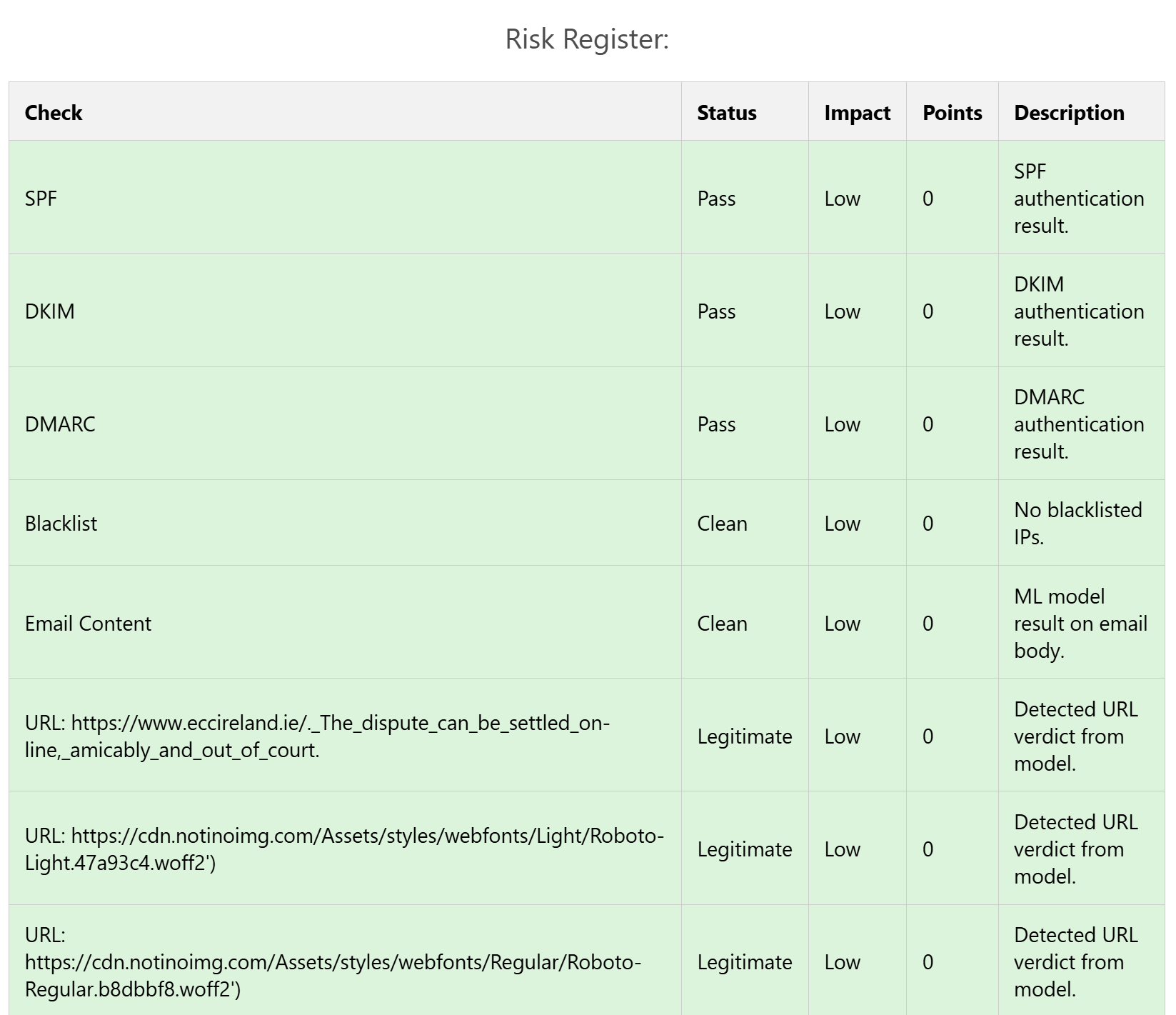
- Suspicious Emails:
This category contains emails that have few parameters flagged as Phishing or Suspicious, these emails need to be monitored, and the user should avail extreme caution when dealing with such emails.
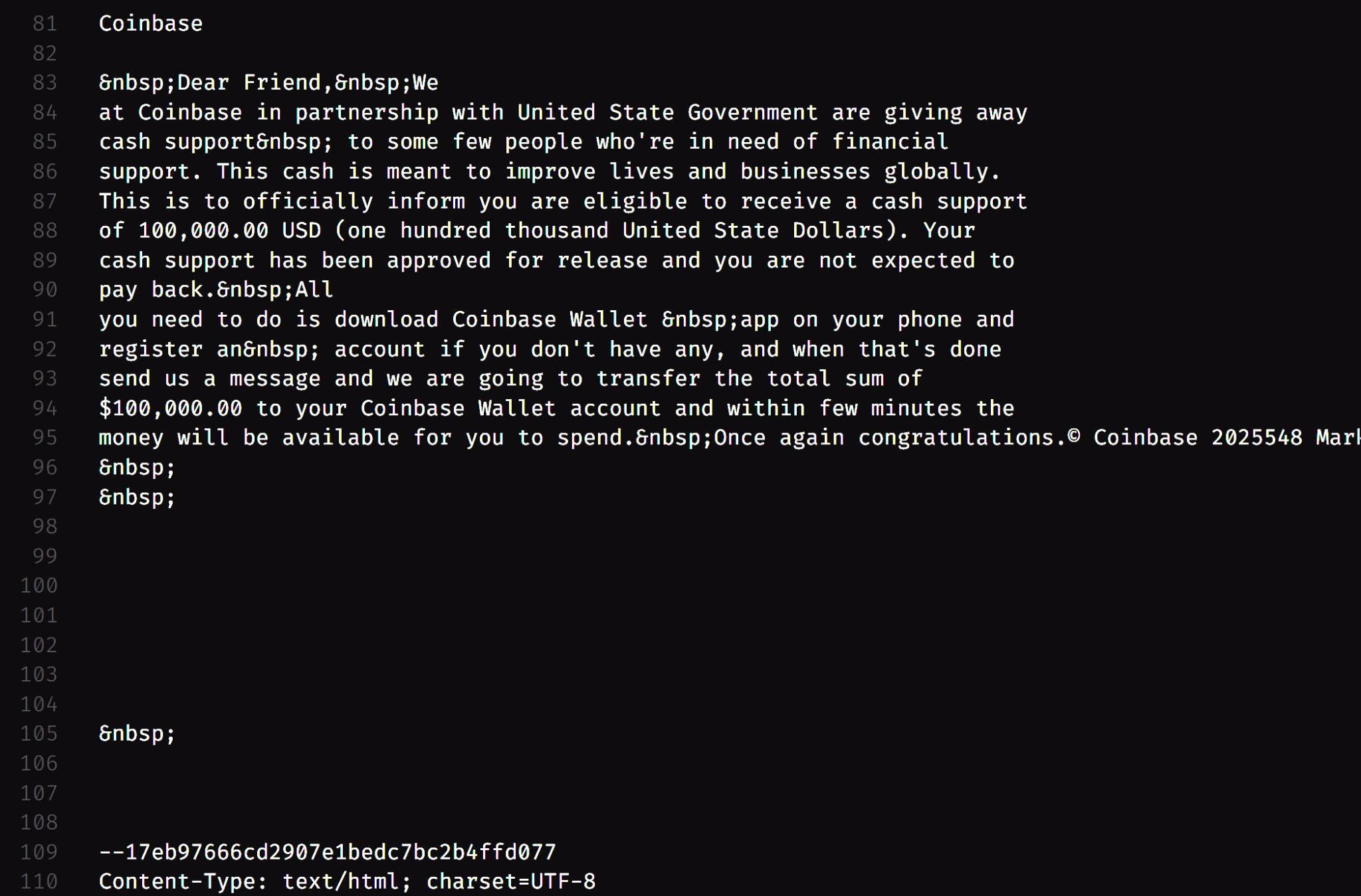
Now, again we send the email headers through our system to determine the legitimacy of this email. As we can see, the verdict is Suspicious. If we go through the risk register, we can identify the exact attack vector present in the email.
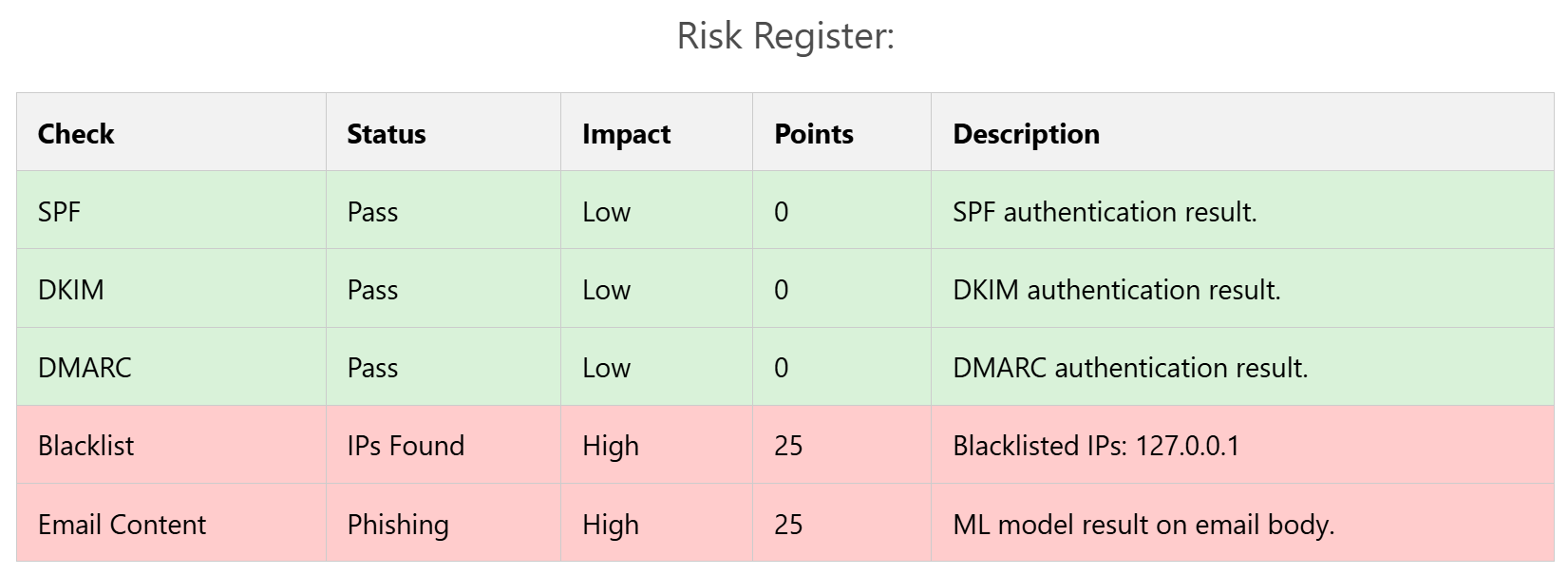
This email didn’t contain any URLs in it, as a result, it primarily focuses on the SPF, DKIM and DMARC records followed by the Blacklisted IPs and Email Content.
- Phishing Emails:
Lastly, we go through the Phishing Emails and check their analysis. This Phishing Email contains multiple links as shown in the email headers below.
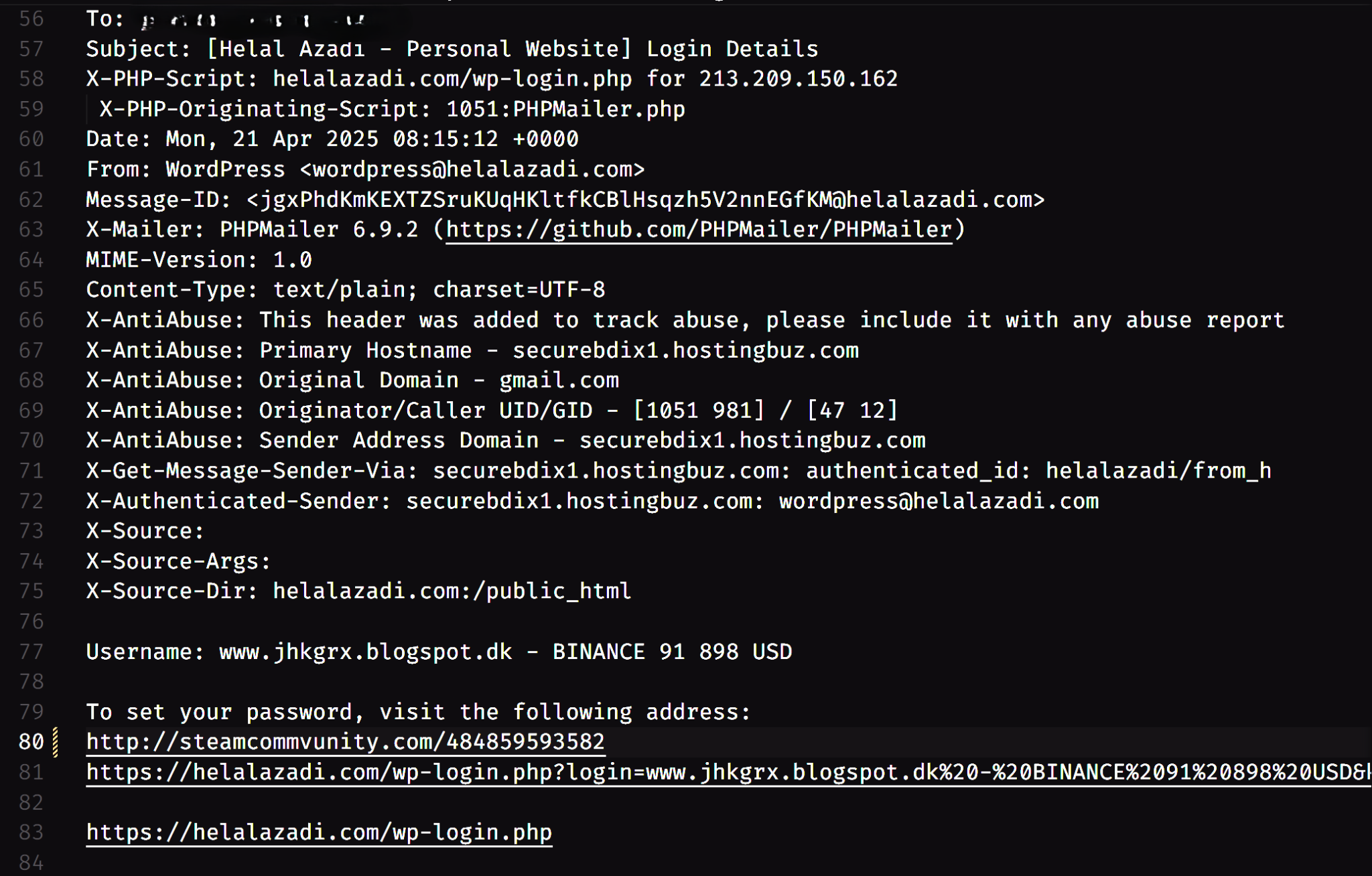
Now, we run this email through our model to check the analysis of the email. This will help us identify if all the URLs are malicious.
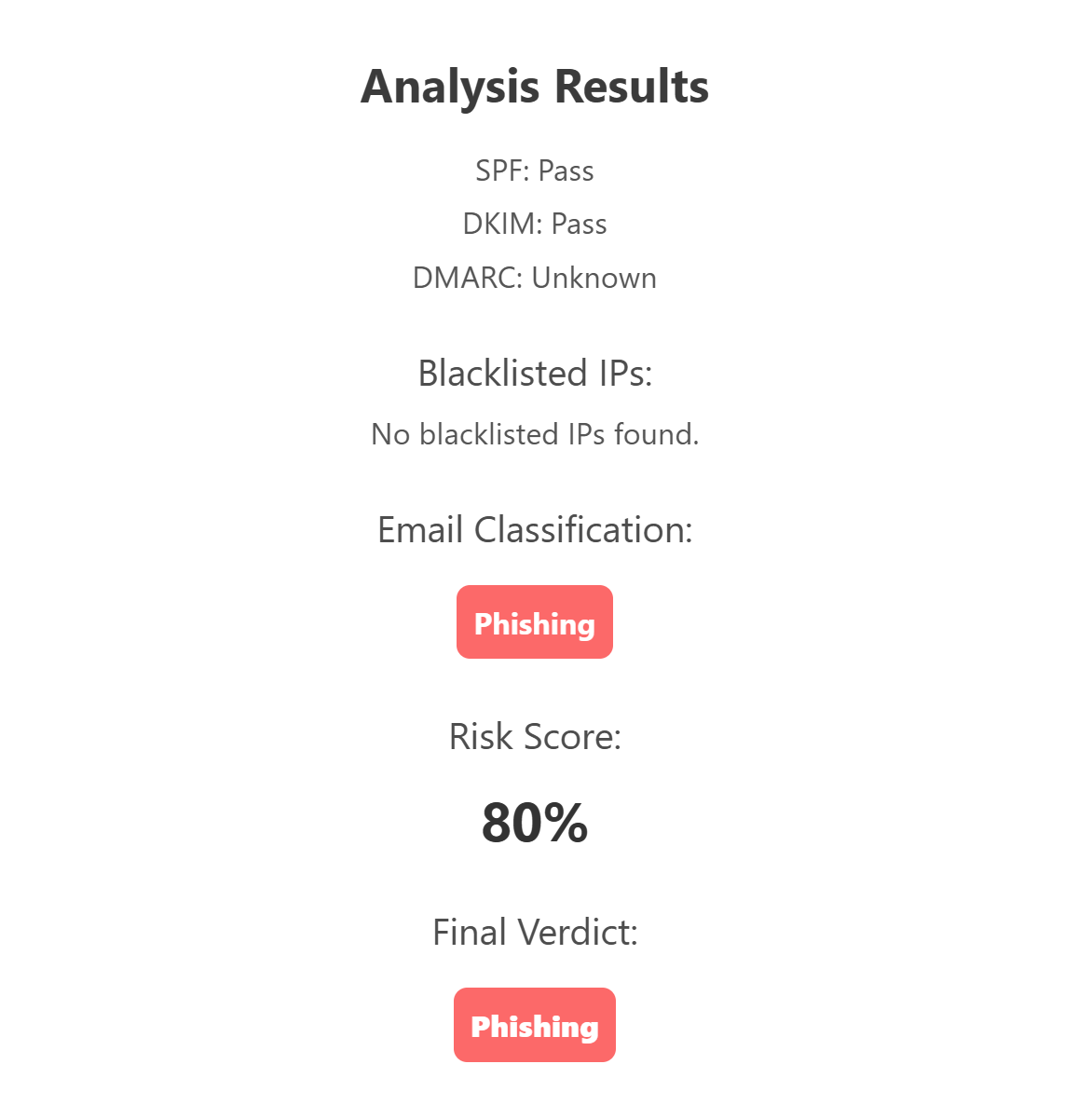
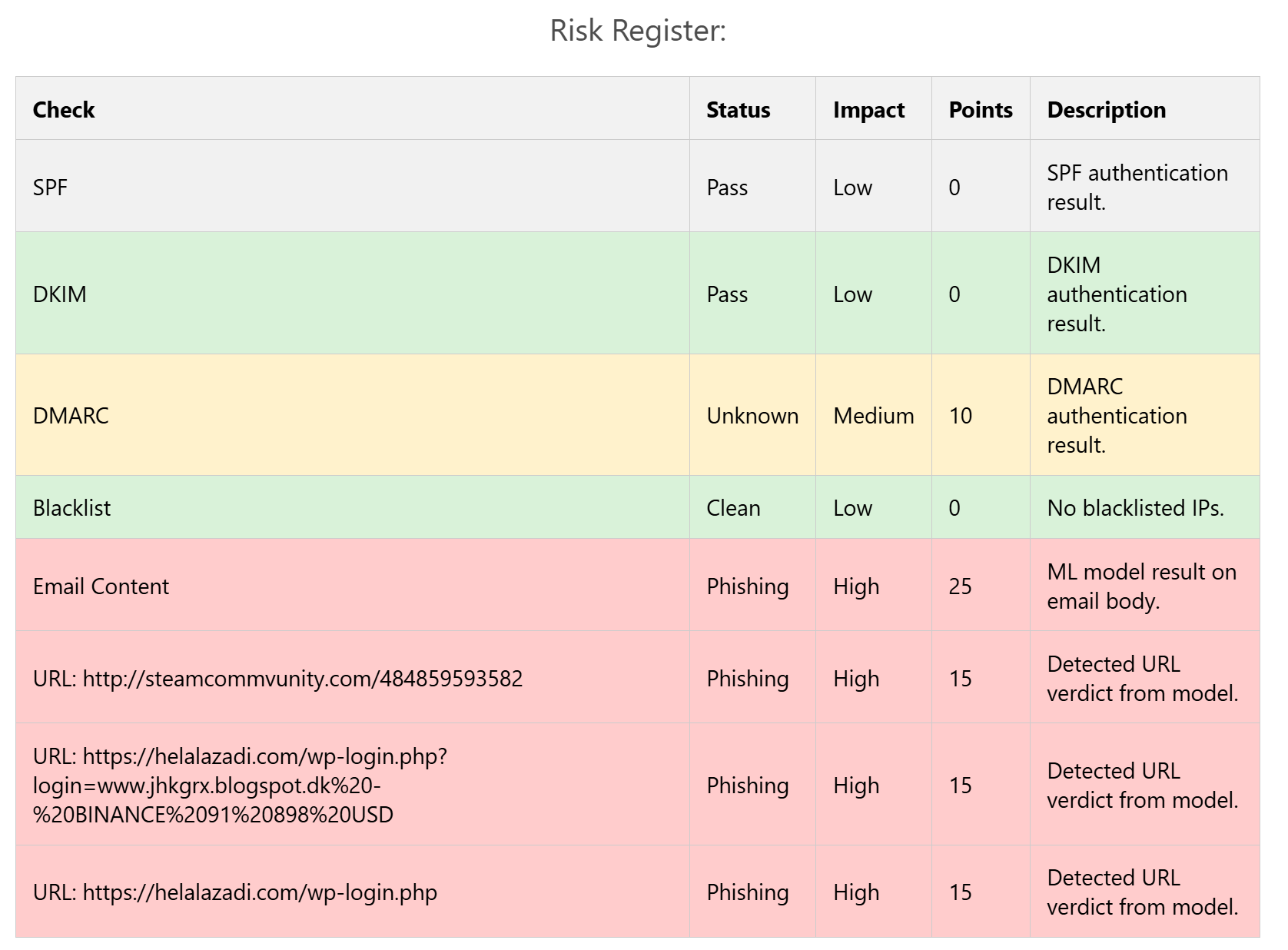
Lastly, the Risk Register clearly shows that there were three URLs present in the email body and all three of them were malicious in nature.
5.3 Monitoring and Review
To maintain the effectiveness and relevance of EmailAlexis, a structured monitoring and review process is proposed. This framework combines automated and manual methods to continually assess system performance and accuracy. For each processed email, detailed classification logs are generated. These logs capture the results of SPF, DKIM, and DMARC checks, blacklisted IP detection, ML-based content classification, URL analysis, and the final risk score with its corresponding classification. These records help in auditing and understanding trends in the emails.
A weekly manual review of flagged emails would be conducted by the security team, focusing on false positives and false negatives. This process helps identify misclassifications, enhancing the model’s reliability in real time. Blacklisted IP lists are refreshed hourly via a scheduled cron job, integrating the latest threat intelligence into the scoring system. SPF, DKIM, and DMARC policies are also periodically revalidated against popular domains to accommodate any updates from email senders (Rose et al., 2019).
All modifications to the system’s logic and detection pipeline are managed through GitHub, ensuring that changes are documented, traceable and maintain accountability.
5.4 Metrics and Reporting
The performance of the EmailAlexis system is determined by a defined set of performance metrics that prioritises accuracy, responsiveness, and detection. These metrics are subject to continuous monitoring and are subsequently translated into standardised, periodic reports.
Critical KPIs utilised for measurement include:
Email Classification Accuracy: Is used to measure the percentage of correctly classified emails as Legitimate, Phishing and Suspicious.
False Positive Rate: It helps in measurement of how often legitimate emails are accidentally flagged as phishing.
False Negative Rate: Helps in measuring the rate at which phishing emails go undetected.
Detection Rate: Determines the effectiveness of the system in the identification of actual phishing attacks.
Blacklist Hits: Determines the count of emails with blacklisted IPs.
SPF/DKIM/DMARC Failures: Tracks the frequency at which email authentication systems fail and gives insight into the emerging trends of spoofing (Rose et al., 2019).
5.5 Continuous Improvement
EmailAlexis constantly improves by being adaptive, open to suggestions, and encouraging innovative security. It is built in a way to accommodate the ever-changing nature of phishing tactics and advanced email threats; the solution dynamically adjusts to remain effective against emerging threats.
A dynamic feedback system is built into the classification phase so that both the users and security officers can report and flag emails which are classified incorrectly. These user inputs are collected and reviewed periodically and utilised as beneficial feedback to retrain the model. Retraining occurs on a monthly basis, or sooner if important performance metrics report that the effectiveness has decreased. This procedure then injects newer phishing samples, fresh linguistic patterns, and fresh URL patterns into the system to ensure that the model remains up to date with the latest threats.
Data augmentation and noise reduction techniques are also used during training to ensure that the model remains strong and reliable. External threat intelligence feeds such as VirusTotal and PhishTank are also checked and used in the system. These real-time updates improve the detection of malicious emails and also provide external validation of model outputs (Borade, Doshi and Patel, 2024).
EmailAlexis also uses a Zero Trust Policy, this means that any email before analysis is treated as malicious to ensure that the email threats don’t go under the radar. This is combined with regular cybersecurity awareness training, which is intended to improve the employees’ knowledge to recognise and avoid phishing attacks. Through this multi-staged approach, EmailAlexis serves not just as a technical solution but also as a foundation of organisational cyber resilience.
6. Conclusion and Recommendations
EmailAlexis is a study focused on developing a tool to combat phishing attacks delivered via email. It aims to protect sensitive data and reduce financial and reputational risks by detecting and blocking phishing emails before they reach users. The study includes identifying vulnerabilities, implementing filters, categorising emails, and tracking attackers. Key aspects include risk management strategies such as identification, assessment, and mitigation, as well as a 10-week implementation plan, continuous monitoring, and compliance measures. The study seeks to enhance data protection, secure communication integrity, and improve organisational defence against cyber threats, with a focus on real-time detection and automated responses.
6.2 Recommendations
One of the top ways for organisations to fight phishing is to ensure they constantly train their employees to avoid making mistakes. Organisations should use and review SPF, DKIM and DMARC frequently to stop email spoofing. If we use AI to analyse content and detect user behaviour in EmailAlexis, it will better protect against email threats. In addition, organisations should improve their watch over insider risks and create automated protocols to manage incidents briskly. Making sure to update your risk assessments and take in relevant threat intelligence helps your organisation remain up to date on new phishing scams. AI-driven phishing messages, fake videos and problems related to remote working require organisations to be proactive. What this research reveals are that cybersecurity is important for companies, their image and the general public to help prevent financial fraud and data breaches.
6.3 Future Work
Future research focuses on expanding EmailAlexis’s capabilities through real-time threat intelligence sharing and improving phishing detection across other platforms like SMS and social media. Improving how easily the system can handle increasing amounts of data and refining how language models function will make it more useful for a variety of industries. Long-term investigations should monitor how the system is used and keep an eye on new styles of phishing attempts. Major issues are that real-world attack data is scarce and that it is hard to keep up with rapidly changing threats. Given that phishing is developing with easier to use AI and phishing-as-a-service, systems must be updated to keep cybersecurity defences strong. In future, all incoming emails will be routed through an email filter at the SMTP server level, enabling automatic detection and blocking of phishing emails before they reach users. This server-level filtering enhances security by preventing malicious content from entering the internal network. Previously, this capability was not implemented due to resource constraints; however, with planned improvements, it will be introduced soon to strengthen the organisation’s email security posture.
References
R. Abdillah, Z. Shukur, M. Mohd and T. M. Z. Murah, “Phishing Classification Techniques: A Systematic Literature Review,” in IEEE Access, vol. 10, pp. 41574-41591, 2022, doi: 10.1109/ACCESS.2022.3166474.
Barreiro Herrera, D.A. & Camargo Mendoza, J.E., 2022. A Systematic Review on Phishing Detection: A Perspective Beyond a High Accuracy in Phishing Detection. Applied Informatics (ICAI 2022), pp.173–188.
Borade, S., Doshi, P.C. and Patel, D.B. (2024). MaliceSpotter: Revolutionizing Cyber Security with Machine Learning for Phishing Resilience. Indian Journal Of Science And Technology, 17(10), pp.870–880. doi:https://doi.org/10.17485/ijst/v17i10.148.
Thomopoulos, G.A., Lyras, D.P. and Fidas, C.A. (2024). A systematic review and research challenges on phishing cyberattacks from an electroencephalography and gaze-based perspective. Personal and ubiquitous computing. doi:https://doi.org/10.1007/s00779-024-01794-9.
American Hospital Association. (2021). FBI Internet Crime Report 2020 | AHA. [online] Available at: https://www.aha.org/other-cybersecurity-reports/2021-03-20-fbi-internet-crime-report-2020 [Accessed 10 Mar. 2025].
Rose, S., Nightingale, J.S., Garfinkel, S. and Chandramouli, R. (2019). Trustworthy email. [online] doi:https://doi.org/10.6028/nist.sp.800-177r1. (Rose et al., 2019)
Sahoo, D., Liu, C. and C, S. (2017). Malicious URL Detection using Machine Learning: A Survey. [online] arXiv.org. Available at: https://arxiv.org/abs/1701.07179.
Alsharnouby, M., Alaca, F. and Chiasson, S. (2015). Why phishing still works: User strategies for combating phishing attacks. International Journal of Human-Computer Studies, 82(82), pp.69–82. doi:https://doi.org/10.1016/j.ijhcs.2015.05.005.
NIST (2012). Guide for Conducting Risk Assessments NIST Special Publication 800-30 Revision 1 JOINT TASK FORCE TRANSFORMATION INITIATIVE. [online] NIST. NIST. Available at: https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-30r1.pdf.
Fishbein, N. (2023). Detect Phishing Emails by Inspecting Email Headers, Attachments, and URLs. [online] Intezer. Available at: https://intezer.com/blog/automate-analysis-phishing-email-files/ [Accessed 5 May 2025].
SpamTitan Email Security. (2024). What is Email Sandboxing? [online] Available at: https://www.spamtitan.com/email-sandboxing/ [Accessed 27 Mar. 2025].
Baker, E. and Cartier, M. (2024). Phishing Trends Report (Updated for 2024). [online] Hoxhunt.com. Available at: https://hoxhunt.com/guide/phishing-trends-report.
Shloman, T. (2024). The Psychology of Phishing: Unraveling the Success Behind Phishing Attacks and Effective Countermeasures. [online] www.trellix.com. Available at: https://www.trellix.com/blogs/research/understanding-phishing-psychology-effective-strategies-and-tips/.
Ic3.gov. (2022). Internet Crime Complaint Center (IC3) | Business Email Compromise: The $43 Billion Scam. [online] Available at: https://www.ic3.gov/PSA/2022/PSA220504. (Ic3.gov, 2022)
Day, B. (2024). Human Error: The Biggest Email Security Risk and How to Mitiga. [online] Guardiandigital.com. Available at: https://guardiandigital.com/resources/blog/human-error-biggest-email-security-risk-how-to-mitigate-it.
Cisco. (n.d.). Detect and Prevent Email Spoofing. [online] Available at: https://www.cisco.com/c/en/us/support/docs/security/email-security-appliance/214844-best-practices-guide-for-anti-spoofing.html.
Gallo, L., Gentile, D., Ruggiero, S., Botta, A. and Ventre, G. (2023). The human factor in phishing: collecting and analyzing user behavior when reading emails. Computers & Security, 139, pp.103671–103671. doi:https://doi.org/10.1016/j.cose.2023.103671.
Rescorla, E. and Dierks, T. (2008). The Transport Layer Security (TLS) Protocol Version 1.2. [online] IETF. Available at: https://datatracker.ietf.org/doc/html/rfc5246.
Wilson, M. and Hash, J. (2003). Building an Information Technology Security Awareness and Training Program. [online] doi:https://doi.org/10.6028/nist.sp.800-50.
NIST (2020). Security and Privacy Controls for Information Systems and Organizations. [online] csrc.nist.gov. Available at: https://csrc.nist.gov/pubs/sp/800/53/r5/upd1/final.
Cichonski, P., Millar, T., Grance, T. and Scarfone, K. (2012). Computer security incident handling guide. Computer Security Incident Handling Guide, [online] 2(2). doi:https://doi.org/10.6028/nist.sp.800-61r2.
Egnyte.com. (2025). Blocked Page. [online] Available at: https://sansorg.egnyte.com/dl/SzUc95nE0x.
European Union (2016). Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation). [online] Europa.eu. Available at: https://eur-lex.europa.eu/eli/reg/2016/679/oj.
bitwire-it (2023). GitHub – bitwire-it/ipblocklist: IP list full of bad IPs – Updated every 2H. [online] GitHub. Available at: https://github.com/bitwire-it/ipblocklist.