5 Chapter 5
Gaming in the Age of Cyber Threats: A User-Centric Approach
Yashwanth Putluru
Anjana Goodavalli Vaishnava
Deekshith Koripalli
Abhigna Srikara Goodavalli
Executive Summary
This study considers the cyber-attacks prevailing in the gaming industry, scrutinising the threats faced by both the users and game providers. With the high-speed internet service and growth of online or digital gaming over multiple platforms like smartphones, PC, and consoles, individual players and gaming companies must endure a highly sophisticated threat landscape. Key risks involve phishing, malware, account hijacking, data breaches, and DDoS attacks; all these impose serious financial, reputational, and organisational consequences.
The study incorporated real world case studies and current industry realities. Additionally, quantitative data on the users was collected by conducting an online survey with 119 valid responses, aged 18 – 45 and above, and insights on cyber security awareness and gaming behaviours. The survey provided crucial insights on the user side vulnerabilities, Moreover, 19% of the participants admitted to downloading malware through unofficial game cheats or mods, and 14% of the participants accounts were hijacked or takeover.
Risk registers and prioritisations matrices are developed to assess the likelihood and severity of the threats. This study also suggests mitigation strategies for key risks and proactive measures to protect users and game providers.
1. Introduction
1.1 Background
The gaming industry has evolved into a vibrant ecosystem offering immersive experiences and platforms where players can interact, exchange data and make transactions. However, this vibrant environment has become an alluring target for cybercriminals escalating concerns over cybersecurity in the gaming industry. For instance, Game Freak experienced sensitive data leak in 2024, where the attackers targeted the employee using phishing and social engineering attack to leak Pokémon Legends game development files and user account data impacting players personal information to be compromised (Carpenter, 2024). Similarly, Itch.io had a phishing incident in 2024, where the platform was falsely flagged for phishing report generated using AI, leading the platform to be taken offline. This incident shows that attackers can target the automated system to hamper platforms and cause gamers to lose access to game developer content (Warren, 2024). Another concerning issue is the continuous evolution of cybercrime in the gaming community. A 2024 case where gamers how are exposed to hacking tools escalate their activities into organised cybercrime. These hackers were able to launch DDoS attacks on their game rival and win (McMillan, 2024).
1.2 Objectives
This study provides in-depth analysis on cyber threats faced by gamers, developers, and game platforms and provide mitigation measures to improve cybersecurity in gaming. The risk Identification segregates the threats faced and emphasise them using real world cases. The analysis examines various losses along with impacts faced by gaming platforms and players.
1.3 Scope
The study reviews various combat strategies and controls that gaming platforms and players can implement to mitigate these cyber-attacks. The strategies are categorised as Preventive measures, Detective measures, Corrective actions, Incident Response, and Residual Risk, Risk acceptance, and Transfer.
1.4 Approach
This study adopts a structured approach that includes data collection, mitigation strategies, and implementation plans. Data on cyber-attacks faced by the gaming industry are gathered through a survey conducted on game uses for collecting quantitative data on cybersecurity practices, threat experiences, and awareness levels combined with research on real-world case studies along with the industry reports that support threat identification.
2. Risk Identification
2.1 Asset Identification
The gaming industry heavily relies on a huge range of assets to deliver a seamless experience to its users. These assets are of material value encompassing physical, digital and advanced technological infrastructure. By understanding them, risks can be managed in an efficient way, ensuring industry’s continuous growth. Below are some of the most important assets in the gaming industry.
- User Accounts and Personal Data: Large amount of sensitive information such as usernames, email addresses, payment details, and gameplay history is stored by gaming platforms. These are highly valuable assets for hackers, their motive is to steal credentials for identity theft, and financial fraud. This kind of breaches lead to reputational damage and legal consequences for gaming industries (O’Connor, 2024).
- Virtual Currencies and In-Game items: Gaining virtual currencies in game consumes lot of time and efforts. Players invest money into buying skins and other collectibles. These currencies, skins, and collectibles are targeted by hackers by exploiting vulnerabilities. Such thefts are for financial gain these also can harm the virtual economy of games and erode player’s trust.
- Gaming Platforms and Servers: The infrastructure hosting online games, includes servers and cloud systems these play a crucial role in operations. They also contain user data and responsible for maintaining uninterrupted gameplay. A compromised server can result in account takeovers of thousands of people. Therefore, server security is essential for safeguarding user data.
- Intellectual Property (IP): IP theft in gaming industry includes, stealing game source codes, unreleased content, and developer tools with this the hacker can develop advanced cheats, creating an unfair environment. This impacts user by compromising security, fairness and overall gaming experience. Furthermore, continuous cheating and exploits caused by leaked code can degrade the multiplayer gaming experience, pushing away the legitimate player (Wikipedia, 2025).
2.2 Threat Identification
The gaming landscape faces a changing threat vector that impacts both users and organisations. Based on the survey results and online resources, the most faced threats are listed below.
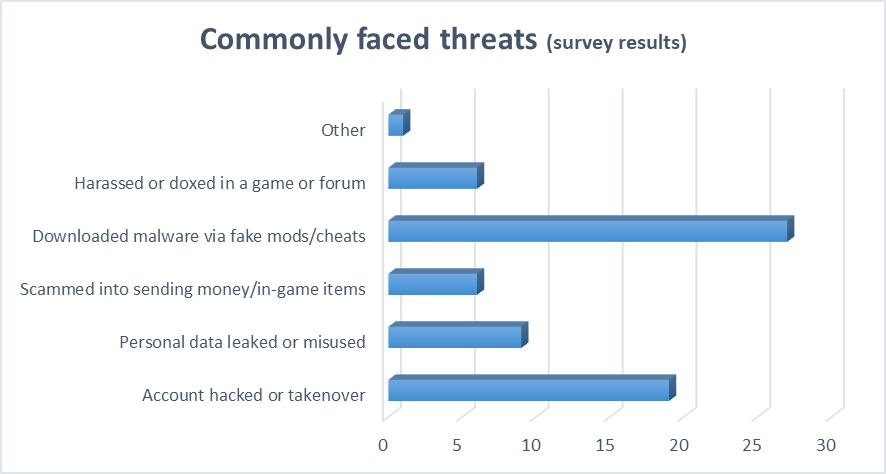
- Ransomware and Malware: This is the mode widely faced threat among the players (19%). Mods in games attract users, as few modifications could enhance game graphics, obtain game characters or additional resources without spending game currencies. Games with those third-party mods or plugins, become entry points for malware which can include spyware, keyloggers or other malware that can compromise user device (www.kaspersky.com, 2023). This can cause theft of financial information or can encrypt user’s files demanding ransom to restore access.
- Credential Stuffing and Account Takeover: Credential stuffing occurs when attacker uses stolen credential information (obtained from data breaching) to access gaming accounts. By accessing these accounts hackers steal virtual assets like in-game currencies, characters, and skins, which will be sold on black market for profit. The attacker can also commit fraud using linked payment methods by making unauthorised purchases (PhotonIQ, n.d.). Moreover, according to the survey conducted results, 14% report that their gaming accounts have been hacked and taken over and 6% say their personal data have been leaked or misused.
- Phishing and Social Engineering: Users are tricked to reveal sensitive details such as login credentials, credit card numbers, or security answers by phishing, it involves crafting fake emails, messages, or websites that mimic legitimate gaming platforms or support teams (Hendrickson, 2025). The conducted survey also says that 6% of the participants have previously been victims of social engineering attacks. Social engineering strategies are attackers posing as friends, teammates, and trusted community members to manipulate users into sharing private information. Sometimes by pretending as support team that helps regarding account recovery but instead steal user data. According to Verizon’s report, “74% of data breaches involve the human element, highlighting the significant role of social engineering in cybersecurity threats” (Verizon, n.d.).
- DDoS (Distributed Denial-of-Service) Attacks: In DDoS attack, the game server is flooded with excessive traffic to disrupt its operations. This affects the user to access the platform, leading to an unfair advantage due to latency issues for the players in multiplayer games. It causes the user to raise reliability and security issues on platform (Hadji-Vasilev and Chapman, 2022). This happened with Apex Legends legitimate player whose game was crashed multiple times while about to win, but after reconnecting to the server was found knocked down by a similar duo all the time, who used DDoS attack to overwhelm the game server with flooding requests and preventing legitimate players from accessing the services (Kent, 2021).
2.3 Vulnerability Assessment
Assessing vulnerabilities helps in analysing the weaknesses and gaps within the system and processes that can be exploited by the threats mentioned above. Below are the key vulnerabilities associated with the threats listed above:
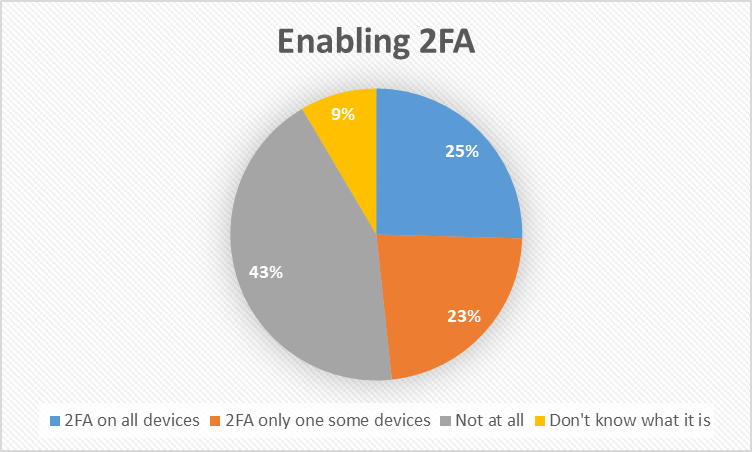
- Weak Passwords and Poor Authentication: As most of the users play multiple games, to memorise passwords for multiple accounts they use weak passwords or sometimes reuse the same passwords across multiple platforms. And according to the survey, 31% of the players reuse their passwords for multiple accounts and 26% are not even sure about it. According to Dashlane, 51% of passwords are reused, and nearly 20% are compromised. Hackers use brute-force techniques which are automated tools to guess passwords exploiting common patterns such as simple words, dates, or repeated characters. Additionally, poor authentication practices by the gaming platforms, such as absence of two-factor authentication (2FA), increases vulnerability. It is clearly seen that only a bare minimum of 25% of the players enable 2FA on all their gaming accounts. For instance, Epic Games has incentivised 2FA adoption by offering free in-game content to users who enable it. However, despite its proven benefits, 2FA adoption remains low across various platforms (Crichton, Lee and Li, n.d.).

- Unpatched Software: Unpatched software refers to applications or systems that have not been updated to fix known vulnerabilities. The gaming platforms release patches to resolve security flaws, but most of the users ignore these updates leaving themselves vulnerable. Hackers take advantage from these vulnerabilities to install malware. To avoid risk users should avoid using outdated devices or unsupported systems.
- Lack of User Awareness: Many gamers underestimate the risk of clicking on suspicious links and downloading unofficial content, which makes them vulnerable for cybersecurity threats. For an instance, in March 2025, google identified a surge in cyber-espionage attacks exploiting a zero-day vulnerability in chrome, triggered by users clicking on malicious email links (Kato, 2025). Installing games and modifications from unofficial sources often bypass strict security measures present in original app stores, which increases the risk of malware infections. These unauthorised downloads can introduce harmful software capable of data breaches, identity theft, and unauthorised access to personal information (TOI Tech Desk, 2024).
2.4 Risk Scenarios
We focus on these four risks because of their high relevance, frequency, and impact in the gaming industry. These scenarios demonstrate the most critical and diverse threats identified in the previous sections.
- Data Breach of a Major Platform: Data breaches in online gaming industry have exposed sensitive user information, leading to security and privacy concerns. In 2019, Zynga, the developer behind popular games like “World with Friends”, experienced a breach where hackers accessed data from approximately 218 million accounts, including names, email addresses, and hashed passwords (Asif, 2019). Similarly, in 2021, Electronic Arts (EA) suffered a cyberattack which caused theft of 780 GB of data, that consisted of game source code, development tools (Coker, 2021). An American gaming industry Roblox Corporation was attacked in July 2022, led to exposure of 4GB of sensitive data, including internal documents and personal information of employees and content creators (SOCRadar Research, 2022). These incidents highlight the insufficient data protection measures and poor authentication practices by gaming industries, such breaches give rise to potential threat to user privacy, trust and regulatory compliance.
- Harassment and Doxing: Attackers target high profile gamers, including streamers and professional players. One of the major risks is stalking and harassment, as seen in the case of Evan Baltierra, was sentenced to two years imprisonment for cyberstalking a professional gamer, using fake accounts to send threats and manipulate police to investigate in wrong direction (McEvoy, 2023). It is found that approximately 50% of Black adult gamers reported experiencing harassment due to their race. In U.S approximately 83 millions of online multiplayer gamers were exposed to hate and harassment when playing video games (Center of technology and society, 2024). These incidents in recent times are increased due to social engineering tactics and openness of gaming communities.
- Exploitation of Microtransaction Systems: Microtransactions refer to small in game purchases by users such as virtual goods, character upgrades within the gaming platform environment. But these microtransactions generate billions in revenue with a rapid growth from $77.8 billion in 2024 to $86.51 billion in 2025 at a compound annual growth rate (CAGR) of 11.2% (The Business Research Company, 2025). Microtransaction systems have been exploited for illicit activities, including money laundering. In 2019, reports indicated that Fortnite’s game currencies was used to launder money from stolen credit cards. Criminals purchased in-game currency with stolen cards and resold it, converting illicit funds into legitimate assets (ACAMS Today, 2023). Exploitation of Microtransactions takes place by credential stuffing, account takeovers, where the attacker by using stolen credentials misuse in-game currencies for financial gain.
- Installing Pirated Games: Users tend to install pirated games to avoid high costs, use cheats or mods in game, and gain access to premium features. These activities can lead to security and privacy risks. Few cracked games require users to disable their antivirus software before installation, to avoid interference with cracked features. Most of the users do this without hesitation, due to lack of awareness. Attackers implant Remote Access Trojan (RAT), using techniques like Crypters to hide signatures and Binders to combine malware with legitimate software (spyboy, 2024). With an intent to save money, every 1 among 10 gamers have downloaded pirated copy of game (Advanced-television.com, 2022).
3. Risk Assessment
3.1 Risk Register and Analysis
The tables below depict the potential risks alongside threats, vulnerabilities and impacts associated with the users and gaming companies in the gaming industry. The likelihood of each risk and their risk-rating is show below. The likelihood is classified into three levels: low representing the risk with least probability to occur, medium representing the risks with moderate possibility, and high representing the risks that requires immediate action.
The severity is also assessed across four categories: A risk rated as a low/tolerable risk causes less damage, whereas the risk with moderate risk rating can be managed using proper mitigation strategies. The high risk risks are severe and can disrupt with the operations and user experience. The severe/intolerable risk ones are the most impactful and deal a lot of damage than other risks. They pose disastrous consequences financially, reputationally and require urgent attention.
Table 1. Risks associated with users
|
Risk Identifiers |
Potential Threats |
Key Vulnerabilities |
Likelihood |
Impacts Analysis |
Risk severity rating |
Evaluation methodology |
|
Loss of sensitive and personal information |
Phishing & social engineering |
Using weak passwords, lack of user awareness and sharing personal information in online platforms |
High |
Critical: can lead to identity theft and financial loses |
Severe |
Analysed survey responses and reviewed online resources |
|
Account compromises and financial loss |
Malware and ransomware |
Lack of updated antivirus, downloading unverified game mods and clicking on malicious links |
High |
Critical: results in unauthorised transactions and loss of game assets |
Severe |
Analysed survey responses and reviewed online resources
|
|
Theft of in-game currency and using compromised accounts |
Account takeovers |
Lack of multifactor authentication and use of weak and guessable passwords |
High |
High: impact on both personal identity and financial assets. |
High |
Analysed survey responses and reviewed online resources
|
|
Account hijacking including most of the risks mentioned |
Scams and fraud |
Not using secure payment methods and falling for less priced accounts |
High |
Critical: results in complete loss of control over the accounts |
Severe |
Analysed survey responses and reviewed online resources
|
|
Financial fraud and using personal data for broader malicious activities |
Identity theft |
Using unsecured networks for gaming and sharing personal details online |
High |
Critical: leads to reputational damage and legal issues |
Severe |
Reviewed online resources |
|
Cyberbullying and erosion of trust |
Harassment and Doxxing |
Lack of anonymity in gaming profiles |
High |
Medium: mental health issues and hostility towards gaming communities. |
Moderate |
Reviewed online resources
|
|
Underage gambling and exposure to inappropriate content |
Access by minors |
Not having a proper age verification process and lack of parental controls |
Medium to High |
High: behavioural issues and developmental impacts. |
High |
Reviewed online resources
|
|
Addiction to gaming and potential health problems |
Overuse of games and technology |
In-game elements that encourage to play for more hours |
High |
Medium: social isolation and long-term health effects. |
Moderate |
Reviewed online resources
|
Table 2. Risks associated with gaming companies
|
Risk Identifiers |
Potential Threats |
Key Vulnerabilities |
Likelihood |
Impacts Analysis |
Risk severity rating |
Evaluation methodology |
|
Service disruption causing downtime |
DDoS attacks |
Insufficient network security and relying on single servers |
High |
Critical: reputation and revenue losses. |
Severe |
Reviewed online resources |
|
Loss of user trust and intellectual property (IP) theft |
Data breaches |
Lack of encryption and adequate authentication tolls |
High |
Critical: reputational damages and loss of user trust. |
Severe |
Reviewed online resources
|
|
Damaged gameplay integrity |
API exploits and cheat software |
Lack of authentication for API requests, and code security |
High |
High: can lead to cheat scandals and low game popularity |
High |
Reviewed online resources
|
|
Being subject to fines and increased scrutiny |
Regulatory non-compliance |
Lack of updated compliance documents |
Medium to High |
High: operational disruption and legal fines. |
High |
Reviewed online resources
|
3.2 Risk Prioritisation
Risk prioritisation is a procedure in which the risks associated to a particular industry or change are analysed to determine which of the risks needs to be mitigated first (Chatterton, 2024). Based on the analysis, these risks can also be accepted or transferred rather than bearing the costs of mitigating them.
There are many methods and ways in which the priority of each of the above risks can be assessed. The simplest way is to prioritise them according to their impact, probability of occurrence and severity (Aptien, 2024). Rather than prioritising the risks based on the costs, the most critical and high-probable risks are addressed first. In this context, the risks with high likelihood and critical impacts are addresses first, then moving onto the risks with medium likelihood and moderate impacts:
- Priority 1 (Severe/intolerable risks): Loss and theft of personal information due to account compromises and account hijacking and financial frauds must be addressed first as the damage done by them cannot be reverted so easily. For example, unauthorised transactions, financial loses, reputational damages and legal penalties.
- Priority 2 (High risks): Stealing of in-game currency and underage gambling and exposure to inappropriate content should be the ones to address next. Although these risks do not do direct financial damages, they still can do more damage to the player. For example, in children who are still learning financial knowledge, this plays a major role in transition from playing using in-game currency to real-money (Ineqe Safeguarding Group, n.d.).
- Priority 3 (Moderate risks): Cyberbullying and game addiction should be targeted next. The impacts of these risks may extend beyond the game space leading to mental health issues like depression, anxiety, insomnia, aggression, loss of relationship and low self-esteem particularly in case in young children (Vibha, 2023; Grinspoon, 2020).
On the other hand, the game companies should also prioritise their risks in a similar way. They may also choose to prioritise them based on costs, regulatory requirements, resource availability or by manageability (Chatterton, 2024).
3.3 Risk Matrix
The risk matrix was developed based on two factors: Likelihood and Impact. Likelihood is the probability of that risk occurring, whereas the impact is the potential consequences when the risk is exploited. This matrix classifies the risks into three categories: severe, high, and moderate risks.
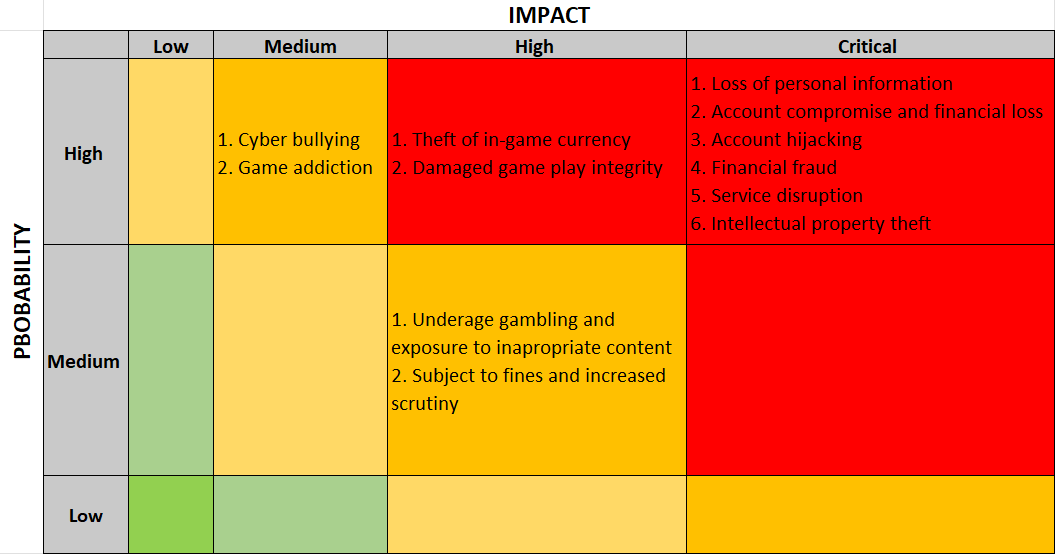
The severe risks, shown in red, may need immediate mitigation or prevention measures as they present a threat to both the players and game designing companies. They often affect their financial security, sensitive data and the gaming experience. Risks like account hijacking, identity theft and financial fraud must be addressed immediately from both the companies and players. They can be prevented by enabling multi-factor authentication, data encryption and account recovery methods. Users must also be educated on strong password management, safe gaming practices and to avoid social engineering scams.
Player awareness and education is much needed to address the high risks, also shown in red. The gaming companies should watch out for any suspicious in-game purchases and bring in new tools for monitoring to prevent stealing of game currencies. They also need to implement strong licensing agreements and copyrights. If not done properly, they may face revenue losses and competitive disadvantages due to stolen codes, pirated copies and unauthorised mods and cheats.
The moderate risks, also shown in red, may require preventive measure and more constant monitoring of the systems and practices. Although they do not pose severe risks, they may still cause huge consequences if left unattended. Issues like bullying, game addiction and exposure to explicit content at very young ages directly impacts the mental health of players. Preventing such risks require proper parental controls and better age verification. Furthermore, companies must also introduce policies to limit the access to gambling features for underage players. They should also create safe portals for reporting such shady behaviours and set screen-time limits to prevent excessive gaming.
4. Risk Mitigation Strategies & Controls
Cybersecurity is a shared responsibility of both users and companies to stay safe in the cyber world. Taking strong preventive and detective measures helps in battling against malicious and bad actors. This section explores the key practises, strategies and controls to be considered by the users and companies.
4.1 Preventive Measures
Below are some of the controls that the users and gaming companies can take to prevent the identified risks from occurring:
- 2-Factor Authentication (2FA): 2FA helps in avoiding the first breaching point of any cyber-attack. Usually, it is recommended that users should opt for authentication method such as 2FA before logging into their respective gaming sessions, as this prevents any unauthorised intrusions in gaming accounts of the users. Companies like Steam and Epic games encourage and guide their users for setting up and using 2FA for their accounts (Steam Support, n.d; Epicgames.com, 2024).
Use of Strong Passwords: One of the simplest forms of preventing cyber-attack is having a strongly configured password for a user account. Gamers tend to create multiple user accounts for multiple games respectively (example: Activision account for Call of duty, Rockstar account for Grand theft Auto). In this hassle, user often tends to create a weak and similar password for multiple accounts for convenience. This creates an opportunity for the bad actors to crack the passwords and breach into user account. To prevent this from happening, creating strong passwords and selecting a reliable password manager to store the passwords is a solution.
Patch and Updates: Users often tend to ignore the updates rolled out by the companies for multiple reasons such as storage constraints or concerns about potential performance issues. The updates rolled out by the companies aim to fix the issues and vulnerabilities, these updates are integrated with security patches which ensure the user’s account safety (Lark Editorial Team, 2024).
Avoid Oversharing: Gaming sessions in general tend to have long durations and during these sessions, gamers have communication platform such as in-game chat or internal game communication. Many of the gamers tend to share personal and sensitive information without knowing the consequences. These information leaks create opportunities for attackers to initiate cyber-attacks and in some cases these information leaks can lead to physical threat as well (McQuiggan, 2023).
Web Application Firewalls (WAFs): Company’ websites deal with high traffic, and it becomes extremely difficult to differentiate between the normal and malicious traffic due to the vast volume of the traffic. To counter this issue, it is recommended for the companies to employ WAFs (Web Application Firewalls) as they add firewall as protective measure for the website. One such reliable option is the Cloudflare WAF (https://www.cloudflare.com/en-gb/application-services/products/waf/).
Endpoint Security Solutions: Gaming companies should take the responsibility of protecting their users against cyber-attacks. To implement this companies should consider the option of Endpoint security solutions. Endpoint security solutions aim to protect the user’s systems as these systems are mostly targeted by the bad actors (SentinelOne, 2024). Gaming companies employing ESS tend to create a safe environment for its users.
In-built Security features: Some games come within built security features for enhancing the safety of the users. As these features are optional, they are disabled by default, it is user’s responsibility to be aware of these features and enable them. Some of these features include account recovery, device management and login notifications.
4.2 Detective Measures
The users and companies can take the below steps to detect to the risks as they occur:
- Account Activity Logs: While gaming the users should employ a monitoring service or enable in-game monitoring service to observe the account activities. This helps in identifying any unusual or malicious activity happening with the account which further helps in taking a corrective measure immediately.
- Anti-Cheat Software for Players: Users must look for anti-cheat software provided by reliable company as this ensures an extra layer of defence against cyber-attacks. This software helps in identifying the malicious software and cheats in advance and ensuring integrity on gaming platforms (Riot Games Support, 2024).
- Appropriate Supervision: A significant percentage of gaming community are teenagers who lack the awareness of cyber threats in gaming industry. Also, the majority of teenagers lack the knowledge of safe cyber practises as in user’s perspective in gaming industry. So, it is very essential as parent/guardian to supervise the gaming activities of these users and enforce essential safety practises to ensure the safety of these users.
- Intrusion Detection Systems (IDS) & Firewalls: Gaming Companies must deploy IDS (Intrusion Detection Systems) (Cisco, n.d.) for real-time monitoring and detect potential malicious activities in advance, key examples for these attacks are DDoS attacks or data breaches. These IDS are well equipped with tools to assist identify and respond to cyber threats quickly.
- DDoS Attack Monitoring: DDoS attack has been major issue for many gaming companies since a long time. Even big companies like Activision Blizzard, Minecraft and Epic Games have been victim to DDoS attacks. To counter this, Game companies should use services such as Cloudflare and Akamai (https://www.akamai.com/solutions/security/ddos-protection) to detect and mitigate DDoS attacks that can disrupt gaming services.
- Bug Bounty Programs: Sometimes it is just not possible to monitor and secure all the services and points for a company which may lead to unaddressed vulnerabilities. To counter this gaming companies should run bug bounty programs to encourage users and ethical hackers to find and report vulnerabilities (Riot Games, 2024).
4.3 Corrective Actions & Incidence Response
Once the risk has been realised, there are some corrective actions the users can take to reduce the impacts of the risks:
- Password Reset: In the event of suspected account compromise or cyber-attack, it is the responsibility of the users to immediately reset their passwords and other credentials to prevent any further damage. And next immediate step would be to enable 2FA to prevent same mishappening occur again in future.
- Reporting Suspicious Behaviour: Cybersecurity and integrity are shared responsibilities of both users and companies. If any user while gaming finds any suspicious activities, such as phishing attempts, cyber-bullying or harassment, they should immediately report on the provided support platform of the game.
- Isolating and securing gaming accounts: After confirming the incident or a breach, the player should disconnect all the devices from the network and try to log out of all gaming platforms and accounts. It is also suggested they reset their passwords and revoke all permissions to any linked accounts.
4.4 Residual Risk, Risk acceptance & Transfer
Despite implementing the right strategies for mitigating the risks, there may be a chance of residual risks depending on the severity. These are the risks that remain even after all possible mitigation strategies have been implemented. For example, a gaming company might take down a major percentage of cheat tools to ensure the cyber safety of players. However, there is still a rare portion of individuals finding a way to breach the environment. This shows a residual risk to competitive integrity. Based upon the appetite levels of each user or a company, they can opt for transferring them or accepting the residues. One option for the game companies is to transfer these residual risks to the insurance company through insurance policies. By doing so, the insurance companies can cover the costs or financial losses in the remediation process to the game developing companies (Fortinet, 2024), eventually making the risks of game companies their own. They may also choose to shift the operational responsibility to expertised third-parties. For instance, companies might consider services such as specialised DDoS protection or critical cloud security services which transfer the technical burden of mitigating these risks to third parties (StormWall, n.d.). Although the company transfers its responsibility, it is still the responsibility of the company to protect its user’s data. Another option for them is to leave it as it is. However, for the companies to opt for this option, the costs for remediation or mitigation of the risks have to be greater than the loss of accepting the risk. This also depends on the severity and the likelihood that the risk may become more vulnerable in the future.
5. Implementation and Monitoring
Avoiding cyber risks and implementing mitigation strategies is not a one step process; instead, it is a continuous effort towards a cyber safe environment in the gaming industry. This section focuses on the detailed plan for implementing mitigation strategies and ensuring their effectiveness along with monitoring strategies.
5.1 Implementation Plan
Developing a detailed implementation plan is very crucial for converting mitigation strategies into actionable steps. This plan consists of how companies can enhance their security measures against cyber risks and how users can stay protected against cyber threats in the gaming industry.
Games are not just software that an organisation can produce and sell to customers; they need continuous improvement, support, and security. Gaming companies should consider SSDLC (secure software development lifecycle) in their game development process. SSDLC provides a robust framework that implements security from the outset. This ensures that the vulnerabilities and inherent risks that could pose threat to users and organisation are eliminated at an early stage (Patten, 2024).
Key elements of implementation plan for game companies include:
- Phased Rollout: A procedure to be considered by gaming companies to implement mitigation strategies in phased intervals. This process involves addressing critical issues and vulnerabilities based on prioritisation. Progress must be defined for a timeline and must be under surveillance consisting of both long-term and short-term goals.
- Minimise Attack Surface: Companies should build their gaming applications and servers to reduce possible interaction points by removing non-essential codes, services, and processes. Minimising ASA (attack surface area) helps in restricting the adversary from further exploiting the application/network. For example, Rockstar club is a client application for a user to login to GTA (Game application). If an adversary breaches the game session of the user, they should not be able to access the Rockstar club application as this particular application contains credentials and other sensitive data of the user (Biam, 2024).
- DDoS Planning: This involves developing a step-by-step roadmap for implementing infrastructure level defences along with the integration of anti-DDoS services and a continuous surveillance system. This plan consists of secure communication systems, ensuring players’ IP addresses are protected, using multiple IPs to avoid single point of failure. Moreover, as UDP protocols are more prone to threats, considering TCP over UDP wherever possible would be one of the key implementations.
Key elements of implementation plan for users include:
- Strengthening Account security: The primary responsibility of the user is to secure their account against cyber threats. This process involves enabling Multifactor authentication, use of strong and unique passwords for their accounts along with employing a secure password manager (Kaspersky, 2020).
- Keeping the Systems secure: Ensuring the system protection becomes a key aspect for the user as machines are an asset for the user in cyberspace. This process involves regular software updates, use of reliable antivirus software and activating built-in security features in gaming platforms.
- Practising safe online transactions and interactions: Securing online presence for a user in gaming ecosystem is very important. This process involves enabling biometric verification for online transactions (S.Akash, 2023), verifying the authenticity of links or messages before interacting with them, and avoid oversharing of information on untrusted platforms.
5.2 Monitoring and Review
Continuous monitoring and reviewing are very critical to measure the effectiveness of implemented mitigation strategies and to make changes accordingly in the evolving cyber threat landscape. Below are the key considerations for both the users and game companies.
Real time monitoring tools enable us to monitor and track any suspicious activities such as unusual login attempts or data transfers related to our accounts. Tools like these ensure real-time network visibility for users. Additionally, users must regularly check for effectiveness of implemented security measures which include regular scanning of the machine and networks, reviewing the measures taken by the gaming company to protect its users and its policies. They must also act quickly according to the situation such as changing the credentials, isolating the account from the machine and reporting the incident to the support team.
On the other hand, game companies should also watch out for cheat tools and pirated copies of their game software. These are most commonly used methods by attackers to deliver malware to user’s system and exploit them. Gaming companies should consider AI automated tools that continuously monitor these cheat tools and pirated copies which can further help in quick fixes (Irdeto, 2025). In addition to these, they should regularly test the effectiveness of their security measures and mitigation strategies against DDoS which would involve stress testing their systems and simulating DDoS attacks on their systems to identify any unknown vulnerabilities and fixing them in advance. This is an important practice as attack types and games infrastructure are dynamic in nature (Gcore, 2025).
5.3 Continuous Improvement
A Continuous improvement approach ensures that risk mitigation strategies evolve with time as response to constantly evolving and changing cyber threats in the gaming industry.
Game players can stay informed and vigilant of the threats and risks by participating in cyber awareness programs, especially the ones that address the issues in gaming industry. Following up with the latest trends in cyber threat landscape and staying updated on emerging threats will help them avoid these threats. Sometimes, these programs also provide a great opportunity to both users and companies to collaborate and identify any vulnerabilities or potential threats in advance. It is also suggested that companies actively organise bug bounty programs, that help identifying in any potential issues or vulnerabilities in the existing systems or networks.
Feedback mechanisms are another way for companies to establish formal communication that enables feedback from customers or employees if they find any issues or vulnerabilities. This process must involve a security team, incident response team and other authorities to improves the process of remediating the problems identified. The companies may also choose to use AI assisted dynamic security strategies that will help in identifying the static defence mechanisms that will eventually become ineffective against the evolving cyber threats (SentinelOne, 2025). Human AI collaboration is another thing that can be considered as one of the most effective continuous strategies to fight against cyber threats. Combining quantitative models (AI) with qualitative intelligence (Humans) can help in building robust defensive strategies (Lee, 2025).
Additionally, companies can also involve in industry level collaborative environment by sharing knowledge on cyber threats, leveraging on shared expertise and industry peers to share knowledge on effective defensive strategies to fight against cyber threats. Such collaborations can help in avoiding common threats such as ransomware (companies like Rockstar games and Capcom have been victims of Ransomware) (SecuritySenses, 2025).
6. Conclusion and Recommendations
Today’s gaming industry offers an immense experience along with increasing vulnerability to cyber threats because of its highly valued digital assets, massive user community, real-time data flow, and communications. This research has identified significant risks for both users and gaming platforms.
6.1 Summary
This study concentrated on the identification, analysis, and mitigation of the significant risks associated with the use and the companies within the gaming industry. It is evident from the risk register and prioritisation matrix that both user level and organisational level threats are evolving rapidly into highly impactful attacks, especially due to the growth of digital engagement.
For users, critical risks include loss of sensitive and personal information, account compromises, Identity theft, and financial fraud, mainly caused by, phishing, social engineering, malware, and insecure user behaviour. These risks are exacerbated by weak authentication practices, unverified third-party content, and lack of cybersecurity awareness.
For gaming companies, most critical threats involve service disruptions from DDoS attacks, data breaches, and regulatory non-compliance. Ultimately resulting in reputational damage, financial loss along with threat to long term trust and retention of users.
Mitigation strategies involve implementing Web Application Firewalls (WAFs), Endpoint Security, Intrusion detection systems, DDoS mitigation services, and user side security features such as multi-factor authentication and account activity monitoring. Additionally, conducting bug bounty programs, considering cyber insurance for residual risks, is essential for building a gaming ecosystem.
6.2 Recommendations
Game providers should implement user end security measures such as multi-factor authentication, Web Application Firewalls (WAFs), and DDoS protection to protect user data and service availability. User education is essential for young players to prevent from phishing and scams. Regular audits and bug bounty programs help in identifying and fixing vulnerabilities. Since game companies deal with minors, companies must improve age verification and percental controls to protect minors. Also, companies need to develop strategies and invest in AI-powered monitoring to counter emerging threats such as AI-driven scams and cyberbullying within gaming communities.
6.3 Future Work
Additional research that could enhance this risk management study includes interviewing cybersecurity professionals in the gaming industry to obtain deeper insights on the threats faced in the real world and their mitigations. Further research could also include cost comparisons of various security strategies.
The future landscape involves rapid development of cyber risk such as AI generated phishing, deepfake scams, and much more sophisticated DDoS attacks. These developments may require futuristic strategies to address the newly arising vulnerabilities.
This current risk management exercise is dependent on secondary sources and lack of access to internal security data from gaming companies.
References
ACAMS Today. (2023). The Potential Perils of Online Gaming. [online] Available at: https://www.acamstoday.org/the-potential-perils-of-online-gaming/ [Accessed 14 Mar. 2025].
Advanced-television.com. (2022). Survey: Video game piracy set to rise. [online] Available at: https://www.advanced-television.com/2022/10/11/survey-video-game-piracy-set-to-rise/ [Accessed 30 Apr. 2025].
Aptien (2024). How to prioritize risks | Risk management | Aptien. [online] aptien.com. Available at: https://aptien.com/en/kb/articles/how-to-prioritize-risks [Accessed 17 Mar. 2025].
Asif, S. (2019). Gaming giant Zynga data breach: 218 million records stolen. [online] Hackread. Available at: https://hackread.com/gaming-giant-zynga-data-breach-218-million-records-stolen/ [Accessed 11 Mar. 2025].
Biam, L. (2024). 7 Principles of Secure Design in Software Development. [online] Jit. Available at: https://www.jit.io/resources/app-security/secure-design-principles [Accessed 21 Apr. 2025].
Carpenter, N. (2024). How do video game companies like Game Freak keep getting hacked? [online] Polygon. Available at: https://www.polygon.com/analysis/465967/pokemon-game-freak-nintendo-hack-leak.
Center of technology and society (2024). Hate is No Game: Hate and Harassment in Online Games 2023. [online] www.adl.org. Available at: https://www.adl.org/resources/report/hate-no-game-hate-and-harassment-online-games-2023 [Accessed 28 May 2025].
Chatterton, C. (2024). The Ultimate Guide to Risk Prioritization. [online] Hyperproof. Available at: https://hyperproof.io/resource/the-ultimate-guide-to-risk-prioritization/ [Accessed 17 Mar. 2025].
Cisco. (n.d.). Cisco Next-Generation Intrusion Prevention System (NGIPS). [online] Available at: https://www.cisco.com/c/en_ca/products/security/ngips/index.html [Accessed 21 Mar. 2025].
Coker, J. (2021). Gaming Giant EA Suffers Major Data Breach. [online] Infosecurity Magazine. Available at: https://www.infosecurity-magazine.com/news/gaming-ea-suffers-data-breach [Accessed 12 Mar. 2025].
Crichton, K., Lee, J. and Li, M. (n.d.). Incentives for Enabling Two-Factor Authentication in Online Gaming. [online] Available at: https://krcrichton.com/incentives-for-two-factor-authentication-in-gaming.pdf [Accessed 10 Mar. 2025].
Epicgames.com. (2024). Two-factor authentication (2FA) and how to enable it – Account Support. [online] Available at: https://www.epicgames.com/help/en-US/c-Category_EpicAccount/c-AccountSecurity/two-factor-authentication-2fa-and-how-to-enable-it-a000084651 [Accessed 20 Mar. 2025].
Fortinet (2024). What Is Cyber Insurance? Why is it important? [online] Fortinet. Available at: https://www.fortinet.com/resources/cyberglossary/cyber-insurance [Accessed 24 Mar. 2025].
Gcore (2025). The rise of DDoS attacks on Minecraft and gaming | Gcore. [online] Gcore.com. Available at: https://gcore.com/blog/the-rise-of-ddos-attacks-on-minecraft-and-gaming [Accessed 16 May 2025].
Grinspoon, P. (2020). The health effects of too much gaming. [online] Harvard Health. Available at: https://www.health.harvard.edu/blog/the-health-effects-of-too-much-gaming-2020122221645 [Accessed 15 Apr. 2025].
Hadji-Vasilev, A. and Chapman, S. (2022). What Is DDoS in Gaming? [Cyber Attacks on Gamers in 2022 ]. [online] Cloudwards. Available at: https://www.cloudwards.net/what-is-ddos-in-gaming/ [Accessed 10 Mar. 2025].
Hendrickson, L. (2025). Cybersecurity Challenges in the Gaming Industry. [online] Identity.com. Available at: https://www.identity.com/cybersecurity-challenges-in-the-gaming-industry/ [Accessed 10 Mar. 2025].
Ineqe Safeguarding Group. (n.d.). Young People & Gambling in Gaming. [online] Available at: https://ineqe.com/2022/04/01/gambling-in-gaming/ [Accessed 15 Apr. 2025].
Irdeto (2025). Game developers vs. cyber threats: How to stay ahead. [online] Irdeto.com. Available at: https://irdeto.com/blog/game-developers-vs-cyber-threats-how-to-stay-ahead [Accessed 16 May 2025].
Kato, B. (2025). Google confirms cyber ‘espionage’ attacks on Chrome users from ‘highly sophisticated malware’. [online] New York Post. Available at: https://nypost.com/2025/03/26/tech/google-chrome-confirms-cyber-espionage-attacks-from-highly-sophisticated-malware/.
Kent, E. (2021). Top Apex Legends players banned for using DDoS attack to win ranked game. Eurogamer.net. [online] 26 Mar. Available at: https://www.eurogamer.net/top-ranked-apex-legends-players-banned-for-using-ddos-attacks-to-win-games [Accessed 30 Apr. 2025].
Lark Editorial Team (2024). Patch Management. [online] Larksuite.com. Available at: https://www.larksuite.com/en_us/topics/gaming-glossary/patch-management [Accessed 20 Mar. 2025].
Lee, S. (2025). A Deep Dive into Security Games and Game Theory. [online] Numberanalytics.com. Available at: https://www.numberanalytics.com/blog/deep-dive-security-games-game-theory [Accessed 17 May 2025].
McEvoy, C. (2023). Orange County Man Sentenced to 2 Years in Federal Prison for Stalking and Harassment Campaign Against Online Gamer. [online] Justice.gov. Available at: https://www.justice.gov/usao-cdca/pr/orange-county-man-sentenced-2-years-federal-prison-stalking-and-harassment-campaign [Accessed 12 Mar. 2025].
McMillan, R. (2024). Getting Cheated in a Videogame Led Him to a World of Online Crime. [online] Msn.com. Available at: https://www.msn.com/en-us/money/other/getting-cheated-in-a-videogame-led-him-to-a-world-of-online-crime/ar-AA1wKLJY [Accessed 9 Mar. 2025].
McQuiggan, J. (2023). Gaming Security Tips for Parents. [online] Spiceworks Inc. Available at: https://www.spiceworks.com/it-security/cyber-risk-management/guest-article/gaming-security-tips-parents/ [Accessed 20 Mar. 2025].
O’Connor, H. (2024). Online Gaming Fraud Detection | Gaming Fraud Prevention Solutions. [online] Pasabi.com. Available at: https://www.pasabi.com/insights/online-gaming-fraud-detection [Accessed 10 Mar. 2025].
Patten, D. (2024). Secure Software Development Lifecycle (SSDLC) – Dave Patten – Medium. [online] Medium. Available at: https://medium.com/@dave-patten/secure-software-development-lifecycle-ssdlc-8ad9273b395b [Accessed 20 Apr. 2025].
PhotonIQ. (n.d.). Credential Stuffing: The Gaming Industry’s Silent Bot Threat. [online] Available at: https://photoniq.macrometa.com/articles/credential-stuffing-the-gaming-industrys-silent-bot-threat [Accessed 10 Mar. 2025].
Riot Games Support. (2024). What is Vanguard? [online] Available at: https://support-valorant.riotgames.com/hc/en-us/articles/360046160933-What-is-Vanguard [Accessed 21 Mar. 2025].
Riot Games. (2024). Reporting A Security Vulnerability. [online] Available at: https://www.riotgames.com/en/reporting-a-security-vulnerability [Accessed 21 Mar. 2025].
S.Akash (2023). Cybersecurity in Gaming: Protecting from Threats and Attacks. [online] IndustryWired. Available at: https://industrywired.com/cybersecurity-in-gaming-protecting-from-threats-and-attacks/ [Accessed 15 May 2025].
SecuritySenses (2025). Game Development Security Trends in 2025. [online] SecuritySenses. Available at: https://securitysenses.com/posts/game-development-security-trends-2025 [Accessed 17 May 2025].
SentinelOne (2024). Business Endpoint Protection: Key Features & Examples. [online] SentinelOne. Available at: https://www.sentinelone.com/cybersecurity-101/endpoint-security/business-endpoint-protection/ [Accessed 20 Mar. 2025].
SentinelOne (2025). Cyber Security Best Practices for 2024. [online] SentinelOne. Available at: https://www.sentinelone.com/cybersecurity-101/cybersecurity/cyber-security-best-practices/ [Accessed 27 May 2025].
SOCRadar Research (2022). Increasing Cyberattacks Targeting the Gaming Industry in 2022. [online] SOCRadar® Cyber Intelligence Inc. Available at: https://socradar.io/increasing-cyberattacks-targeting-the-gaming-industry-in-2022/ [Accessed 11 Mar. 2025].
spyboy (2024). The Dangers of Downloading Pirated Apps and Games. [online] Spyboy blog. Available at: https://spyboy.blog/2024/11/15/the-dangers-of-downloading-pirated-apps-and-games/ [Accessed 27 Apr. 2025].
Steam Support (n.d.). Steam Guard: How to set up a Steam Guard Mobile Authenticator. [online] help.steampowered.com. Available at: https://help.steampowered.com/en/faqs/view/6891-E071-C9D9-0134 [Accessed 20 Mar. 2025].
StormWall. (n.d.). How to protect gaming services against DDoS attacks. [online] Available at: https://stormwall.network/resources/blog/game-server-ddos-protection [Accessed 18 May 2025].
The Business Research Company. (2025). Online Microtransaction Global Market Report 2025. [online] Available at: https://www.thebusinessresearchcompany.com/report/online-microtransaction-global-market-report [Accessed 12 Mar. 2025].
TOI Tech Desk (2024). Why downloading apps from unofficial sources on the internet can be dangerous. [online] The Times of India. Available at: https://timesofindia.indiatimes.com/technology/tech-tips/why-downloading-apps-from-unofficial-sources-on-the-internet-can-be-dangerous/articleshow/110217576.cms [Accessed 25 Mar. 2025].
Verizon (n.d.). 2025 Data Breach Investigations Report. [online] Verizon Business. Available at: https://www.verizon.com/business/resources/reports/dbir/ [Accessed 10 Mar. 2025].
Vibha (2023). How Video Game Bullying is Threatening the Future of the Industry. [online] Checkstep. Available at: https://www.checkstep.com/how-video-game-bullying-is-threatening-the-future-of-the-industry/ [Accessed 15 Apr. 2025].
Warren, T. (2024). Itch.io went offline due to a ‘trash AI-powered’ phishing report. [online] The Verge. Available at: https://www.theverge.com/2024/12/9/24316882/itch-io-offline-domain-registration-funko-report.
Wikipedia. (2025). Video game clone. [online] Available at: https://en.wikipedia.org/wiki/Video_game_clone [Accessed 20 Mar. 2025].
www.kaspersky.com. (2023). Ransomware hacks on gaming computers. [online] Available at: https://www.kaspersky.com/resource-center/threats/gaming-ransomware [Accessed 10 Mar. 2025].
Appendices
- EY – Gaming industry survey 2022: https://www.ey.com/content/dam/ey-unified-site/ey-com/en-us/insights/media-entertainment/images/what-s-possible-for-the-gaming-industry-in-the-next-dimension/documents/ey-tmt-gaming-metaverse-report-final.pdf
- KPMG – The state of risk in gaming industry: https://kpmg.com/kpmg-us/content/dam/kpmg/pdf/gated/2024/gaming-risk-brochure-secured.pdf
- Zscaler – Ransomware attacks on gaming industry: Ransomware Attacks on the Gaming Industry | Brief | Zscaler
- IoSentrix – Top cyber threats in gaming industry and solutions: https://www.iosentrix.com/blog/cyber-threats-in-gaming-industry-and-their-solution
- Kaspersky: https://usa.kaspersky.com/about/press-releases/kaspersky-more-than-4-million-cyberattacks-targeted-gamers-in-2023?srsltid=AfmBOoqNjZDl7bsyLvRzKekAkycoqIJG7EIt3dOBz2pGtjoLKpvUqMJ8&utm
- DBIR – 2023 Data breach investigation report: https://inquest.net/wp-content/uploads/2023-data-breach-investigations-report-dbir.pdf