6 Chapter 6
A Cybersecurity Framework for Ransomware Mitigation in Supply Chains
Marywinnie Mugah
Meenakshi Adakamaranahalli Lingaiah
Kavitha Adakamaranahalli Lingaiah
Preamble
This study posits a cybersecurity framework for ransomware mitigation in supply chains, with a particular focus on Maersk, one of the leading service providers in integrated global logistics. A.P. Moller-Maersk is a Danish multinational conglomerate that provides services such as port operation, warehousing, and supply chain management. Headquartered in Copenhagen, Maersk operates in over 130 countries and employs more than 100,000 people worldwide (Maersk, 2025).
Given its core business, Maersk is a suitable subject for this study due to the critical role it plays in the global supply chain and its experience with ransomware attacks, such as the NotPetya incident (Steinberg, Stepan and Neary, 2021). As a leading global logistics company handling a significant portion of maritime container trade, its operations are vital to the international supply chain. This makes it an appropriate case for evaluating the impact of ransomware attacks and developing effective mitigation frameworks. Furthermore, the organisation’s proactive approach and commitment to cybersecurity demonstrated through practices such as comprehensive backup systems and documented response plans, offer valuable insights into enhancing cybersecurity resilience in supply chains.
Executive summary
This study presents a cybersecurity framework for the mitigating ransomware attacks within supply chain environments, with a focus on a case study on Maersk’s experience during the NotPetya ransomware incident. It highlights the raising ransomware threat actors targeting digital supply chains, primarily by exploiting the interconnectedness of digital ecosystems and the potential for cascading impacts across multiple organisations.
Using NIST Cybersecurity Framework and MITRE ATT&CK as main frameworks, this study identifies critical risks in digital assets, third-party vendor relationships, human factors, and process gaps. This study emphasises vulnerabilities like weak software update controls, inadequate network segmentation, and immature incident response capabilities, which significantly surge the likelihood and impact of ransomware attacks in digital supply chain.
The Maersk NotPetya case demonstrates how a third-party software vulnerability (M.E.Doc) created an entry point for malware, which then propagated through a flat network architecture. This resulted in $250 million financial losses and operation downtime of 10days. This shows the importance of layered cyber defence strategies which includes preventive technical controls (e.g., firewalls, RBAC, MFA, SSDLC), procedural governance (e.g., vendor risk assessments, change management), and people-focused measures (e.g., awareness training, contractual security clauses).
This study also recognises newly arising risks such as Ransomware-as-a-Service (RaaS), geopolitical tensions, and AI-driven attack vectors, which creates a huge necessity for continuous improvements and adaptive security strategies. Future work is recommended in these areas like AI-driven behavioural analytics, automated compliance using RegTech and quantitative risk modelling (e.g., FAIR) to enhance executive decision-making.
By adopting the proposed frameworks which are rooted in defence-in-depth principles, organisations can strengthen their resilience, which would reduce ransomware risk exposures across the supply chain, and align with evolving regulatory requirements such as GDPR, NIS2 and EU AI Act.
1. Introduction
1.1 Background
Cybersecurity has evolved into a crucial aspect in securing digital assets in the digital landscape. Organisations have continually invested in cybersecurity to keep up with the increasing sophistication and frequency of cyber-attacks. Moreover, cybersecurity regulations have continuously been formulated, making significant contributions to shielding digital assets such as sensitive data shared between business partners as well as maintaining the integrity of critical digital infrastructure. Effective cybersecurity measures prevent massive losses and disruptions that result from cyberattacks, while also enhancing digital security trust, which in turn fosters innovation and economic growth (Amin, 2024).
1.1.1 Definitions of key terms and concepts
The definitions below serve as a foundation for the study.
Ransomware: Malicious software that encrypts data and denies access until a ransom is paid (Datta and Acton, 2024).
Defence in Depth (DiD): A cybersecurity strategy that employs a multilayered approach to protect digital assets (Datta and Acton, 2023).
RaaS (Ransomware as service): A Cybercriminal business model in which ransomware kits are readily available in the dark web for deployment (Datta and Acton 2024).
Mean Time to Detect (MTTD): A metric that measures the average time it takes for an organisation to detect a security incident (Khan,2023).
Mean Time to Respond (MTTR): A metric that measures the average time it takes for an organisation to mitigate, contain, and recover from security incident ((Khan,2023).
Recovery Time Objective (RTO): The maximum acceptable amount of time a system can be down after an incident.
Recovery Point Objective (RPO): The maximum acceptable amount of data loss measured in time.
NIST (National Institute of Standard and Technology): A U.S. federal agency that develops standards, including cybersecurity standards.
MITRE ATT&CK: A globally recognised framework and knowledge base that outlines the techniques and tactics of adversaries across the attack lifecycle.
Incident Response Plan: A strategic plan used by an organisation to detect, respond to, and recover from an incident, minimising damage and ensuring business continuity.
1.2 Objectives
Supply chains have witnessed a surge in ransomware attacks by threat actors, primarily due to the widespread impact these attacks can have on multiple organisations and individuals. A single compromised entity can disrupt operations across numerous stakeholders, amplifying both the overall damage and potential ransom payouts (Ghanbari, Koskinen and Wei, 2024).
This study aims to address these challenges with the specific objectives of this research being:
- To develop a cybersecurity framework that effectively mitigates ransomware attacks in supply chains.
- To evaluate the risks posed by third-party vendors and establish risk management practices that enhance supply chain security.
- To analyse real world case studies of ransomware attacks in supply chains to understand their impacts and derive actionable mitigation strategies.
1.3 Scope
This study aims to mitigate ransomware attacks within supply chains by focusing on several key areas. It begins with the identification of critical digital assets within the organisation and an examination of common ransomware attack vectors targeting supply chains. Additionally, the study evaluates risk assessment frameworks to identify high-risk areas within the organisation’s operations. Moreover, it reviews relevant regulatory requirements and analyse the role of governance in enforcing robust cybersecurity measures.
1.4 Approach
To gain a deeper understanding of ransomware attack vectors and propagation mechanisms, this study involves a thorough analysis of real-world ransomware incidents using the NotPetya attack. This case serves as an example of how ransomware, initially targeting a single entity, can rapidly escalate to the larger supply chain through lateral movement (Steinberg, Stepan and Neary, 2021).
The MITRE ATT&CK framework serves as the threat taxonomy for mapping adversary tactics, techniques, and procedures (TTPs) associated with ransomware attacks, particularly within supply chain environments. Using world threat intelligence, the framework enables detailed attribution of threat actor behaviour across the threat lifecycle (Roy et al., 2023). This granular mapping will support the identification of specific techniques used by threat actors in high-profile attacks, thereby enhancing the mitigation strategies.
Overall, the study incorporates the National Institute of Standards and Technology (NIST) Cybersecurity Framework to structure and evaluate ransomware mitigation strategies. Its five core functions: Identify, Protect, Detect, Respond, and Recover (Bernroider and Walser, 2018) offers a comprehensive and scalable model for enhancing cyber resilience. Furthermore, the framework high adaptability for organisations across the supply chain ecosystem.
Risk identification is a fundamental process in Cyber Supply Chain Risk Management since organisations heavily rely on digital technologies, cloud-based services, third- party vendors, and open-source products (Hammi et al., 2023).
An organisation may build a highly secure cyber infrastructure however, threat actors who are unable to infiltrate the system directly may exploit digital supply chain products to enter the system and implant ransomware compromising the integrity, confidentiality and availability of data and business operations.
2.1 Asset identification and Risk Register.
To efficiently manage cyber risks, companies must identify, categorise, and assess their digital assets.
|
Asset Type |
Assets |
Risk (Further explained in Threat identification) |
|
Physical Assets |
|
|
|
Digital Assets |
Cloud based services, Software applications, open-source libraries, Code repositories |
|
Table 1: Key assets in the supply chain targeted by Ransomware
- People, process risk in the supply chain targeted by Ransomware discussed in table 2
|
Asset type |
Assets |
Risk (Further explained in Threat identification) |
|
Human Asset |
Third party Developers, IT Administrators, Contractors |
|
|
Process and policy |
Third party vendor weak process and policy |
|
Table 2: People, process risk in the supply chain targeted by Ransomware

Figure 1: Asset vulnerability
An organisation typically relies on at least one, if not all, of these digital supply chain assets. Since these assets are provided by third party vendors, the organisation does not have a complete control over their security and often lacks visibility into third-party dependencies. If any of these products contain a security vulnerability, attackers can exploit it to gain access to multiple organisation using the same product.
Once the attacker infiltrates the system, they can inject Ransomware and allow it to spread across multiple layers to maximum impact. The Ransomware can then be activated to encrypt data, rendering it inaccessible. Therefore, risk Identification is crucial, as it helps businesses to anticipate cyber threats and vulnerabilities and to develop effective mitigation strategies.
In the case of the Maersk ransomware attack, below mentioned the lack of proper asset management and risk identification is believed to have been a contributing factor.
|
Asset Type |
Asset |
Risk |
|
Digital Assets |
Third party software used here is M.E. Doc |
|
Table 3: Maersk’s Asset Vulnerability
2.2 Threat Identification
Cyber Supply chain threats are diverse and constantly evolving. Vulnerabilities in the supply chain can lead to multiple types of cyber-attacks, including malware, ransomware, DDoS, phishing and social engineering, insider threats, API exploits, and more. Most of these attacks exploit weak links in the Supply chain, enabling attackers to gain access to multiple companies using the same compromised products. Once vulnerabilities are identified, any type of cyberattack becomes possible.
Ransomware poses a significant threat to cyber supply chains by targeting the risk associated with supply chain assets. Unlike traditional cyberattacks, ransomware attacks in supply chains can propagate across interconnected systems, simultaneously affecting multiple organisations. In the cyber supply chain, products within the supply chain layer can have access to the organisation’s critical operations and data. Companies often rely on multiple cyber supply chain products, creating a wide spectrum where attacker can identify vulnerabilities. The threat actor does not need to penetrate the organisation’s core cybersecurity systems directly instead; they can exploit a vulnerability in any of the cyber supply chain products to gain back door access and initiate an attack.
2.3 Vulnerability Assessment
Vulnerability assessment assesses the impact of the risk identified in case it materialises.
1.Physical assets: Physical assets such as servers, data centres, networking hardware, and IoT devices are typically purchased from a third-party vendor. As discussed above, several risks are associated with supply chain physical assets.
End-of-life hardware with outdated security patches, compromised firmware such as IPMI (Intelligent Platform Management Interface, which enables BIOS-level access to servers), weak security configurations like using HTTP port over HTTPS, counterfeit IoT devices, weak data centre security can create back door entry for ransomware attackers to get an entry into organisations using these vulnerable cyber supply chain assets. In 2018, Bloomberg alleged that Chinese intelligence had inserted malicious microchips into Supermicro motherboards. These mother boards were used in U.S tech companies, including Amazon and Apple. The malicious chips allowed remote attackers to alter the operating system kernel, creating a backdoor that could be used for various malicious activities, including injecting ransomware (Barbosa & Franco, n.d.).
2.Digital Assets: Companies, recognising the cost savings and advantages of cloud computing, are increasingly migrating their workloads to cloud infrastructure services. Many companies also rely on third-party vendors for various software solutions, including finance, HR, incident management, security, backup, and disaster recovery (DR) solutions. Additionally, various software solutions are used for operations of the organisation. Moreover, organisations are now utilising open-source software. A threat actor must find a single-entry point in any of these digital assets to inject ransomware. Few of the Threats are discussed below.
- Unregulated Software usages policies: All software usage should be regulated and approved. If not, user may download and install any software, which can be malicious creating a vulnerability.
- Vulnerabilities in open-source libraries: Using 3rd party libraries which are not approved can lead to malicious code injections and other security risks.
- Unauthorised access to cloud services: Weak Security controls for accessing cloud resources can result in unauthorised access to critical resources.
- Unregularised patch management: Patch management if not in place, can lead to usage of older updates with old security patches.
For the Maersk attack, the main attack vector was a third-party software M.E.Doc which is a widely used accounting software. The software installation and parch management were not regularised. The M.E.Doc software update provided an entry point for the Notpetya malware. EternalBlue & Eternal Romance which were known vulnerabilities in the windows operating system with older patch allowed NotPetya to move across networks without human interaction, affecting multiple layers. Again, unregularised patch management creating a gateway. Once the ransomware entered the system, it rapidly propagated across the network, causing massive disruption (Greenberg, 2018).
3.Human Asset process and policies: Organisations outsource operations to third-party vendors for better cost optimisation. These outsourced vendors are often provided with access to the organisation’s critical operations and data, as vendors often require privileged access to internal systems, cloud environments, and sensitive corporate data (Hammi et al., 2023). Cyber supply chains involve software developers, IT administrators, and contractors who interact with enterprise applications, industrial control systems (ICS), and cloud platforms, creating potential entry points for cyber threats (Yeboah-Ofori et al., 2021).
Without strict access controls, background checks, and contractual security agreements, third-party vendors can become weak links, exposing organisations to insider threats, ransomware Infections, and software supply chain compromises. Also, with Cyber security policies differences exposes all the cyber risk present within the third-party vendors company possess into the main organisation (Robinson, Corcoran, & Waldo, 2022).
The Toyota Ransomware Attack (2022) is a notable example, where Konjima industries, a supplier that provides essential components for Toyota, was targeted by the LockBit ransomware, due to the attack Toyota was forced to halt production across all its domestic plants (Aggarwal, 2023).
2.4 Risk Scenarios in Cyber Supply chain Ransomware attack
Risk scenarios help organisations understand realistic cyber threats that can compromise the integrity, confidentiality and availability of critical systems and data. A ransomware attack through the cyber supply chain can lead to financial losses, operational disruptions, and reputation damage (Hammi et al., 2023; Yeboah-Ofori et al., 2021).
Below we outline examples of high impact, medium impact, and low impact scenarios.
2.4.1 High-Impact Risk Scenarios
Scenario: Ransomware Attack on a software vendor
Threat: An attacker infiltrates the organisation through a third-party software using a third-party software update and deploys ransomware. This compromised software is used across the organisation in all environments like Test, Development, Pre-Production, and production. The ransomware spreads across the entire organisation, encrypting data at different levels and causing widespread disruption.
- Impact:
- Data Unavailability: Unavailability of critical Data, Data is encrypted and cannot be accessed.
- Operational disruption: Unavailability of data leading to business down, leading to heavy financial losses.
- Data compliance lost: Data being unavailable would lead to compliance loss leading to heavy fines and reputational damage.
- Real-World Example: The Maersk NotPetya attack leading to Maersk operations down for 10 days and causing financial losses exceeding $250 million (Cartwright & Cartwright, 2023; Hammi et al., 2023; Aggarwal, 2023).
2.4.2 Medium-Impact Risk scenarios
Scenario: Ransomware infection via Compromised Vendor Endpoint
Threat: A vendor with remote access to the organisation’s network had an endpoint compromised with ransomware because of weak endpoint security. This ransomware spread to all shared drives and non-critical systems, but it was contained before reaching core production systems.
Impact:
- Data Unavailability: Some shared fields and non-critical data got encrypted leading to impact with non-critical functions.
- Operational delay: noncritical processes slow down due to data being unavailable.
- Remediation Costs: Requires cleanup, forensic analysis, and partial recovery from backups.
Real-World Example: The Kaseya VSA ransomware attack (2021) spread via compromised IT management software to MSP customers, causing localised outages but was contained before impacting critical infrastructure (Ghanbari, Koskinen and Wei, 2024).
2.4.3 Low-Impact Risk Scenarios
Scenario: Phishing Attack on a Supply Chain Employee
Threat: A Phishing email tricks on a User within the human element of the supply chain. The attacker successfully deceives the employee and installs spyware that monitors user activity and accesses confidential information.
Impact:
- Data integrity lost: User data is exposed and can be tampered.
- Confidentiality: Attackers harvest user credentials, gaining access to internal enterprise systems.
- User financial details exposed.
- IT team once identified
Real-World Example: The Target Data Breach (2013) resulted from a phishing attack on a third-party HVAC vendor, granting attackers access customer records (Yeboah-Ofori et al., 2021; Robinson, Corcoran, & Waldo, 2022).
Risk assessment plays an important role in determining the severity and the likelihood of cyber threat that impact the cyber supply chain. After risk identification, assessing the risks is the next step. This process helps organisations prioritise security efforts by evaluating the identified risks, its severity, and impact, and how they can compromise the confidentiality, integrity, and availability of critical business assets. Once categorised in terms of High Risk, medium risk and low risk threats, the risks can then be prioritised, and appropriate solutions can be implemented based on their criticality. An effective risk assessment would include a risk register, risk evaluation, and visualisation tools like risk matrix to guide mitigation strategies (Hammi et al., 2023).
3.1 Risk Register and analysis
A risk register is a structured tool used to document identified threats, vulnerabilities, potential impacts, and likelihoods. It helps decision-makers visualise the areas where the cyber supply chain is most exposed, and which areas must be prioritised. Risks associated with the assets identified during the risk identification phase are now assessed based on their potential impact, as shown below (Yeboah-Ofori et al., 2021).
|
Risk ID |
Threat |
Vulnerability |
Asset Affected |
Impact |
Likelihood |
Risk Rating |
|
R1 |
Ransomware in software updates |
Weak update validation |
Software supply chain |
High |
High |
High |
|
R2 |
Cloud API exploit |
Misconfigured cloud access |
Cloud platforms |
High |
Medium |
High |
|
R3 |
Insider threat |
Excessive privileges |
Enterprise systems |
Medium |
Medium |
Medium |
|
R4 |
Phishing/social engineering |
Untrained personnel |
Human assets |
Medium |
High |
High |
|
R5 |
Malware in open-source code |
No dependency vetting |
Application software |
Medium |
Medium |
Medium |
|
R6 |
DDoS attack on vendor system |
No redundancy or response plan |
Third-party systems |
Low |
Medium |
Low |
Table 4: Risk register
Real-World Risk Register in cyber supply chain.
|
ID |
Risk Description |
Vulnerability |
Risk origin |
Impact |
Impact Severity |
Migration Status |
|
1 |
Outdated OS |
EternalBlue & Eternal Romance (Notpetya) |
Vendor |
Org level infrastructure going down. Business down |
High |
In-Progress |
|
2 |
MFA for Vendor Login |
Non-Fully compliant login policy |
Vendor |
Unauthorised access. User level impact |
Low |
In-Progress |
|
3 |
CIFS shares Accessible to Everyone including vendor |
NTFS permissions for File shares open to Everyone |
Internal |
Unauthorised data access, Data Loss, Business Impact |
Medium |
Mitigated |
|
4 |
No Network Segregation |
All network exposed |
Internal |
Cyber-attack entire organisation can be impacted |
High |
In-Progress |
|
5 |
SSH port open for entire firewall and vendor |
Non optimal firewall |
Internal |
Unauthorised access. Possibility of Brute force attack |
High |
Mitigated |
|
6 |
Ransomware/malware identified |
Ransomware/Malware identified by intrusion detection system |
Vendor |
Several layers in infrastructure affected leading to data loss and business down |
High/Immediate |
Mitigated |
Table 5: Real World risk register
This register represents real-world type of risk register, combining observations of types of threats and their impact. Some risks like outdated OS, No Network Segregation can be associated with the Maersk attack (Yeboah-Ofori et al., 2021).
3.2 Risk Evaluation
Once the Risk have been identified, assessed, and logged in a risk register, the next step is to evaluate their significance in the context of the organisation’s objectives, business continuity, and its risk tolerance. This involves not just understanding the technical risks but also to evaluating how each threat could disrupt the data integrity, operational availability, compliance regulations and companies’ reputation. For example, Maersk, being a major player in the logistics sector, faced severe consequences from a ransomware attack such as data loss, service disruption, compliance loss and reputation loss. Implying affecting Availability should be rated to be more Critical, Confidentiality, Integrity become severe (Hammi et al., 2023).
|
ID |
Threat |
CIA |
Likely |
Impact |
Tolerance |
Priority |
|
R1 |
Ransomware in updates |
A, I |
High |
Severe |
Low |
Critical |
|
R2 |
Cloud API exploit |
C, I |
Medium |
Major |
Low |
High |
|
R3 |
Insider threat |
C |
Medium |
Moderate |
Medium |
Medium |
|
R4 |
Phishing |
C, A |
High |
Moderate |
Medium |
High |
|
R5 |
Malware in open-source code |
I |
Medium |
Moderate |
Medium |
Medium |
|
R6 |
DDoS on vendor |
A |
Medium |
Minor |
High |
Low |
Table 6: Risk Evaluation
Explanation of Evaluation Criteria:
- CIA: shows which aspect of security is at risk, Confidentiality (C), Integrity(I), or Availability (A).
- Likelihood: Based on supply chain vulnerability, shows likelihood of attack possibility.
- Impact: Measures the potential damage or impact of the Risk.
- Tolerance: Organisation ability to manage consequences.
- Risk Priority: Shows if risk needs immediate action or can be addressed later.
- (Robinson, Corcoran, & Waldo, 2022).
3.3 Risk Matrix
A risk matrix is a tool used to map and prioritise risks based on their changes of occurrence and how significant impact it can create. In our context of cyber supply chain, we can have clear overview of which risks that would be posing a bigger challenge and which must be actioned first. Below is a heat map showing the likelihood of the attack to the severity of the attack (Hammi et al., 2023).
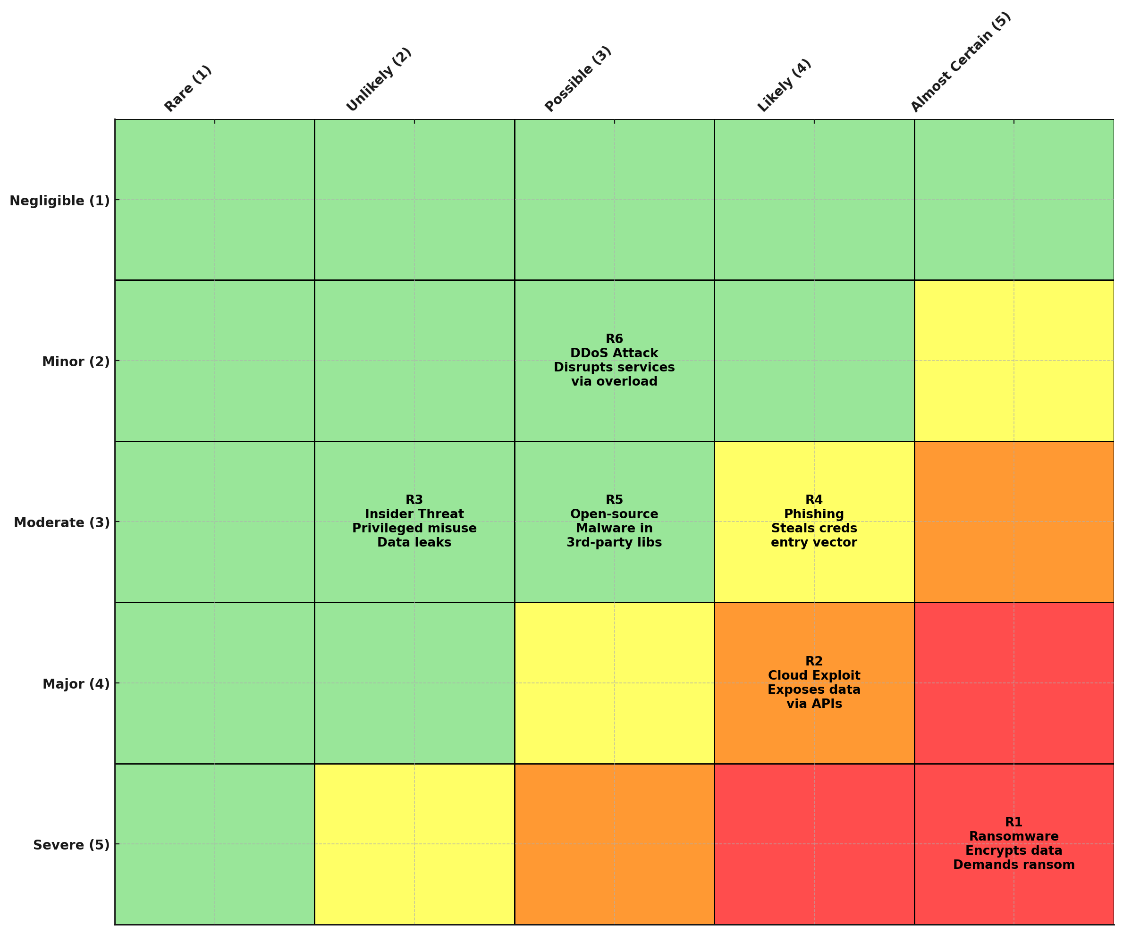
Figure 2: Risk Matrix
Implications for Risk Management
This risk matrix allows security leaders to visualise risk concentrations and find out the hot zones and target in investing to mitigate this risk as below.
- Critical and high Risks (R1, R2, R4): These should get immediate mitigation like software update integrity verification, enhanced endpoint protection, phishing awareness training, etc.
- Medium Risks (R3, R5): Which can be monitored closely and controlled steadily like security insider access reviews, role-based access control (RBAC) implementation, and zero trust architectures.
- Low Risks(R6): These may be addressed after critical and medium risks, for example, by enabling load balancing to mitigate DDoS attacks.
By aligning risks to organisational tolerance, the matrix makes sure that the high-priority threats to CIA principles receive the necessary attention and resources (Hammi et al., 2023). This would help transform complex cyber threats into a intuitive and actionable format allowing the risk management teams to focus on what matters most supporting evidence-based decision making sure the risks are systematically prioritized and addressed (Yeboah-Ofori et al., 2021; Robinson, Corcoran, & Waldo, 2022).
4. Risk Mitigation Strategies & Controls
Once the risks are identified, assessed, and evaluated, the next step would be building risk mitigating strategies. Effective risk mitigation strategies within the digital supply chain require a layer-by-layer security approach, aligned with the NIST Cybersecurity Framework (Identify, Protect, Detect, Respond, Recover) and MITRE ATT&CK tactics and techniques. This should incorporate preventive and detective controls, along with systematic security policies, and informed by adversary behaviour, would create a resilient cyber ecosystem (Kwon et al., 2023; Ahmed et al., 2022).
4.1 Preventive Measures
Preventive measures focus on building measures to reduce the chances of cyber threats infiltration and materialising. Preventing is the critical part of any risk mitigation strategy (Hammi et al., 2023).
4.1.1 Technical controls
Firewalls and Network segmentation: Deploying network segmentation and perimeter defences like firewalls would help limit lateral movement within the infrastructure. This would isolate sensitive systems, and it would minimise the blast radius in case of any compromise. This would align with MITRE mitigation like M1030, which is network segmentation, and NIST CSF PR.AC-5, making sure critical assets are separated logically and ingress and egress traffic is controlled.
Role based access controls (RBAC), zero trust policies, Multi Factor Authentication (MFA) : Implementing RBAC and enforcing Zero Trust security principles will help in ensuring the users have only limited access necessary. MFA Authentications would help in securing from attacks like brute force password attacks, phishing attacks etc. MFA adds an extra layer of validation, making it significantly harder for attackers to gain unauthorised entry (Ahmed et al., 2022).
Secure software Development and management Lifecycle (SSDLC): Adopting SSDLC practices like static/dynamic analysis, peer reviews, secure configuration management, upgrade control, reduce the risk of the software vulnerability that can be exploited (Ahmed et al., 2022).
Cloud Hardening: Enabling stronger encryption, disabling default credentials, and removing unnecessary services fortifies cloud infrastructure.
Endpoint protection for vendors Supply chain partners can become a weak links. Using Endpoint Detection and Response (EDR) tools in the vendor-managed devices would help in reducing risk which can exploit compromised endpoints (Aljoghaiman & Sundram, 2023).
Backup/Disaster recovery in case of compromise, Backup and DR solutions would help business to restore to last available safe restore points. Recovery and restore plans must be pre-build and tested validated and documented with RPO (Recovery point object) and RTO (Recovery Point object) and accepted by business.
|
Preventive Technical Control |
Mapped MITRE ATT&CK Technique |
Mapped NIST CSF Control |
|
Firewalls and Network Segmentation |
M1030 – Network Segmentation |
PR.AC-5 |
|
Role-Based Access Control (RBAC), Zero Trust, MFA |
M1036 – Multi-Factor Authentication |
PR.AC-4, PR.AC-6 |
|
Secure Software Development Lifecycle (SSDLC) |
T1190 – Exploit Public-Facing Application |
PR. IP-3 |
|
Cloud Hardening |
M1042 – Encrypt Sensitive Information |
PR.DS-1, PR.IP-1 |
|
Endpoint Protection for Vendors |
M1049 – Antivirus/Antimalware |
PR.PT-1 |
|
Backup/Disaster Recovery (DR) |
M1053 (Data Backup); M1051 (Disaster Recovery) |
PR.IP-9, PR.IP-10, RC.RP-1 |
Table 7: Technical controls
4.1.2 Procedural Controls
Vendor Risk Assessment: Structured evaluation of the vendor is performed, including security posture, compliance history, and operational maturity, which helps in identifying risks involved and prioritising these risks and systematically preventing them.
Change management controls: Uncontrolled changes lead to a major source of vulnerabilities. Proper change management control with proper approval workflows and rollback mechanisms would help in preventing unauthorised system alterations.
Secure Development Policies: Enforcing a comprehensive software deployment policy, which would be covering everything from secure code standards to test procedures, would help in new software’s not introducing systemic vulnerabilities. For example, controlling GitHub push only after validation and approval (Aljoghaiman & Sundram, 2023; Hammi et al., 2023).
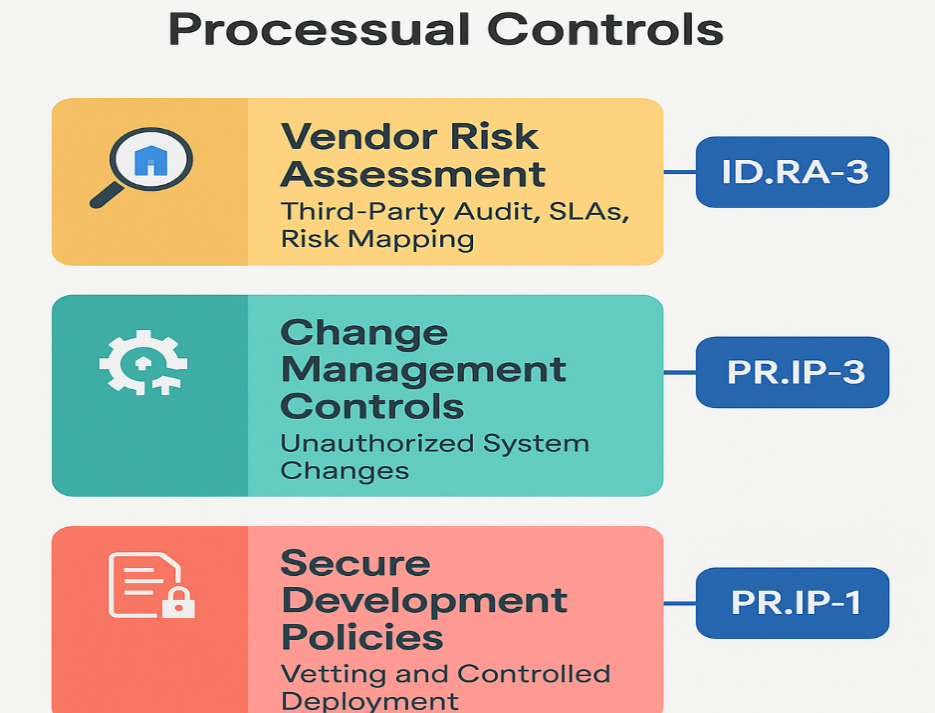
Figure 3: Processual controls
4.1.3 People controls
Contractual security requirements: Mandatory security clauses such as compliance with industry standards, breach notification timelines, audit provisions, and data protection terms.
Supply Chain Awareness: Employees and vendors should be aware of the structure and risk implications of interconnected supply chains, which would help in building a security-conscious culture.
Behavioural Norms for Software Vendors: Evaluation of the vendor culture, whether they adopt secure by default and secure by design principles.
Cybersecurity training: Continuous training on phishing, data handling, incident reporting, and simulated attacks helps reduce the human attack surface (Yeboah-Ofori et al., 2021; Robinson, Corcoran, & Waldo, 2022; Aljoghaiman & Sundram, 2023).
|
People Control |
Mapped MITRE ATT&CK |
Mapped NIST CSF Control |
|
Contractual Security Requirements |
Trusted Relationship (T1199) |
ID.GV-3 |
|
Supply Chain Awareness Training |
Spear phishing via Service (T1194) |
PR.AT-2 |
|
Behavioural Norms for Vendors |
Supply Chain Compromise (T1195) |
ID.SC-4 |
|
Cybersecurity Training |
Phishing (T1566), Valid Accounts (T1078) |
PR.AT-1 |
Table 8: People controls
4.2 Detective Measures
Prevention is ideal; however, detecting and responding to an incident as early as possible also greatly reduces the damage that a risk can cause.
Detective measures include: –
- Monitoring & Logging
- Security Information and Event Management: Aggregate and correlate security events in real-time threat detection and mitigation before explosion.
- Centralised logging: Centralised log collection is collected and analysed to reveal anomalies and enable forensic investigations (Kwon et al., 2023; Hammi et al., 2023).
- Intrusion Detection & Threat intelligence
- Network Intrusion Detection Systems: Monitoring the network for known threat patterns and identifying anomalies in network patterns aids in the detection of malicious activities.
- Threat intelligence feeds: Integration of global threat feeds helps security teams recognise indicators of compromise based on the latest TTPs (Tactics, Techniques, and Procedures), aligning detection with current threat landscapes (Kwon et al., 2023; Ahmed et al., 2022).
- Behavioural Analytics
- Monitoring user and Entity behaviour using advanced analytics monitor systems to detect deviations from established baselines, helps in detecting insider threats, vendor threats, and account misuse. The table below specifies some controls related to behavioural analytics
|
Detective Measure |
Mapped MITRE ATT&CK |
Mapped NIST CSF Control |
|
Security Information and Event Management (SIEM) |
Anomaly Detection Techniques (General mapping) |
DE.CM-1, DE.CM-7 |
|
Centralised Logging |
T1005 -Data from Local System (log tampering), T1119 – Automated Collection |
DE.CM-1, DE.CM-7 |
|
Network Intrusion Detection Systems (NIDS) |
T1046 – Network Service Scanning, T1557 – Adversary-in-the-Middle |
DE.CM-7, DE.CM-4 |
|
Threat Intelligence Feeds |
Correlates to known TTPs from adversaries like Lasarus & menuPass |
DE.CM-6, ID.RA-2 |
|
Behavioural Analytics |
T1078 – Valid Accounts |
DE.CM-8 |
Table 9: Detective controls
4.3 Corrective Actions & Incident Response
Once a supply chain threat is detected or exploited, corrective actions and responses must be done swiftly, which are mentioned below: –
- Incident response plans: Standard operating procedure (SOP) must be built with a communication plan with vendors, customers, and regulators.
- Containment: Removal or isolation of the compromised component.
- Recovery: Rollback/restoration plans to be built and swift implementation of the plan to restore to the previous safe restore points.
- Post incident reviews: Documentation of root cause, recovery timelines, and action for improvements (Hammi et al., 2023).
However, all the corrective actions & incident responses must be pre-built for various scenarios and need to be tested, validated, and approved with the business for various cases of attack. If the measures are not pre-built, the time taken for building a containment plan can allow the attack radius to exponentially grow and cause major damage.
4.4 Compliance Measures
Cyber supply chain risks intersect with legal and regulatory obligations.
- Key regulations alignment
Organisations must align with global and regional regulatory frameworks. If the organisation is compromised and this leads to compliance miss, it can lead to hefty fines and reputational loss. Organisations must take strict measures to safeguard the data, which can lead to compliance misses.
NIS2 directive (EU critical infrastructure protection): Energy, healthcare, transport, and digital services are under NIS2 Directives.
General Data Protection Regulation (GDPR): Policies on handling, collecting, storing, processing, and protecting personal data
EU AI Act for AI-based supply chain solutions: AI transparency, accountability, and risk classification.
|
Regulation |
Scope |
Key Focus Areas |
|
NIS2 Directive |
EU Critical Infrastructure Protection |
Energy, healthcare, transport, and digital services |
|
General Data Protection Regulation (GDPR) |
Data Privacy and Protection |
Collecting, storing, processing, and protecting personal data |
|
EU AI Act |
AI Governance in Supply Chains |
Transparency, accountability, and risk classification of AI |
Table 10: Regulatory controls
- Contractual & compliance clauses: Organisations must make sure to have contractual clauses with vendors that include compliance requirements.
- Awareness sessions and documentation: Awareness sessions and documentation should be there for corresponding departments (procurement, legal, and IT), outlining compliance responsibilities and escalation paths (Hammi et al., 2023; Robinson, Corcoran, & Waldo, 2022).
4.5 Residual Risk, Risk Acceptance & Transfer
Even after all the above steps, residual risks might remain, especially in a dynamic and distributed environment like the cyber supply chain.
- Risk Acceptance: High risks reduced to low-impact risks should be documented and signed off by leadership.
- Risk Transfer: Use Cyber insurance and outsource legal firms with a reputation for legal and compliance management as contractors.
- Effectiveness Review: Risk acceptance or transfer decisions should be periodically reviewed, especially after:
Security incidents
Regulatory changes
Onboarding of new vendors or services (Yeboah-Ofori et al., 2021).
Combining all the discussed measures will enable organisations to drastically reduce the likelihood of any cyber supply chain attacks. Ransomware attacks can be reduced to zero if all the measures are followed and adhered to without fail (Cartwright & Cartwright, 2023).
Applying the Risk Mitigation Framework to Maersk Supply chain: Analysing the Maersk supply chain ransomware attack shows the absence of failure of layered cybersecurity risk mitigation strategies leading to catastrophic operational, financial, and reputational losses. Below is an analysis of the Maersk’s control failures and mitigation opportunities, with reference to what was not followed and how it could have been avoided or mitigated (Greenberg, 2018).
|
Control Area |
Observed Failure |
Recommended Practice |
Impact If implemented |
|
Network Security |
Flat network: malware spread globally |
Isolate high-risk zones (e.g., Ukraine) using firewalls, VLANs, and micro-segmentation |
Malware spread would be contained; blast radius minimised |
|
Third-Party Risk |
Unvetted vendor software (M.E.Doc) used |
Conduct third-party risk assessments; mandate secure software procurement policies |
Risky software could be flagged and isolated pre-deployment |
|
User Awareness |
No staff training on cyber supply chain risks |
Enforce awareness programs and simulate supply chain attack scenarios |
Could have prevented lateral movement via compromised users |
|
Monitoring |
No SIEM or threat detection; breach unnoticed |
Implement SIEM and MITRE ATT&CK-based anomaly detection and alerting systems |
Early detection and faster containment of attack |
|
Incident Response |
No tested IR/DR plans; recovery relied on a single backup |
Establish and test recovery plans with defined RTOs/RPOs; maintain geo-redundant backups |
Quicker recovery, reduced operational downtime |
|
Compliance |
No cyber compliance framework or audit mechanism in place |
Adopt NIS2, GDPR, and DORA-aligned internal policies; schedule regular audits |
Enforced cyber hygiene and stronger legal defensibility |
Table 11: Maersk Attack, Control Failures & Mitigation Opportunities
5. Implementation And Monitoring
5.1 Implementation Plan
To implement the risk mitigation strategies identified in the section above, a detailed plan is drawn up, including timelines and task owners. The timelines are categorised into three short, middle and long-term depending on their criticality. The table below summarises the implementation plan:
|
Mitigation Strategy |
Timeline |
Task Owner |
Requirements |
|
Deploy Firewall |
Short term (0-3 months) |
IT Operations |
Firewall hardware/software, MFA tools |
|
Network Segmentation |
Short term (0-3 months) |
IT Operations |
Network architecture |
|
Implement RBAC, Zero Trust architecture, and enforce MFA |
Short term (0-3 months) |
IT Operations |
policies |
|
Vendor Risk Assessments |
Short term (0-3 months) |
Procurement & Security |
Vendor evaluation tools, compliance checklist |
|
Deploy SIEM & Logging |
Short term (0-3 months) |
IT Operations |
SIEM software |
|
Cybersecurity Training |
Continuous |
HR & IT |
Training platform, Training personnel |
|
SSDLC Implementation |
Medium-term (3-6 months) |
Development Team |
code analysis tools, secure coding policies |
|
Patch management |
Continuous |
IT Operations |
Software updates |
|
Cloud Hardening |
Medium-term (3-6 months) |
Cloud Admin |
Cloud security configurations, encryption tools |
|
EDR Deployment |
Medium-term (3-6 months) |
IT Operations & Procurement |
EDR licenses, endpoint policies |
|
Backup & Recovery Testing |
Medium to Long-term |
IT Operations |
Backup software, test environments |
|
Develop Incident Response Plan and test |
Long-term (6 – 9 months) cont. |
IT operations |
IR playbooks, simulation tools |
|
Risk Acceptance/Transfer Review |
Long-term (6 to 9 months) continuous |
Governance & Legal team |
Insurance policies, risk registers |
|
Regulatory Compliance |
Long-term (6 to 9 months) |
Governance & Legal team |
Compliance requirements |
Table 12: Implementation Plan
The Gantt chart below shows a visual representation of the implementation plan.
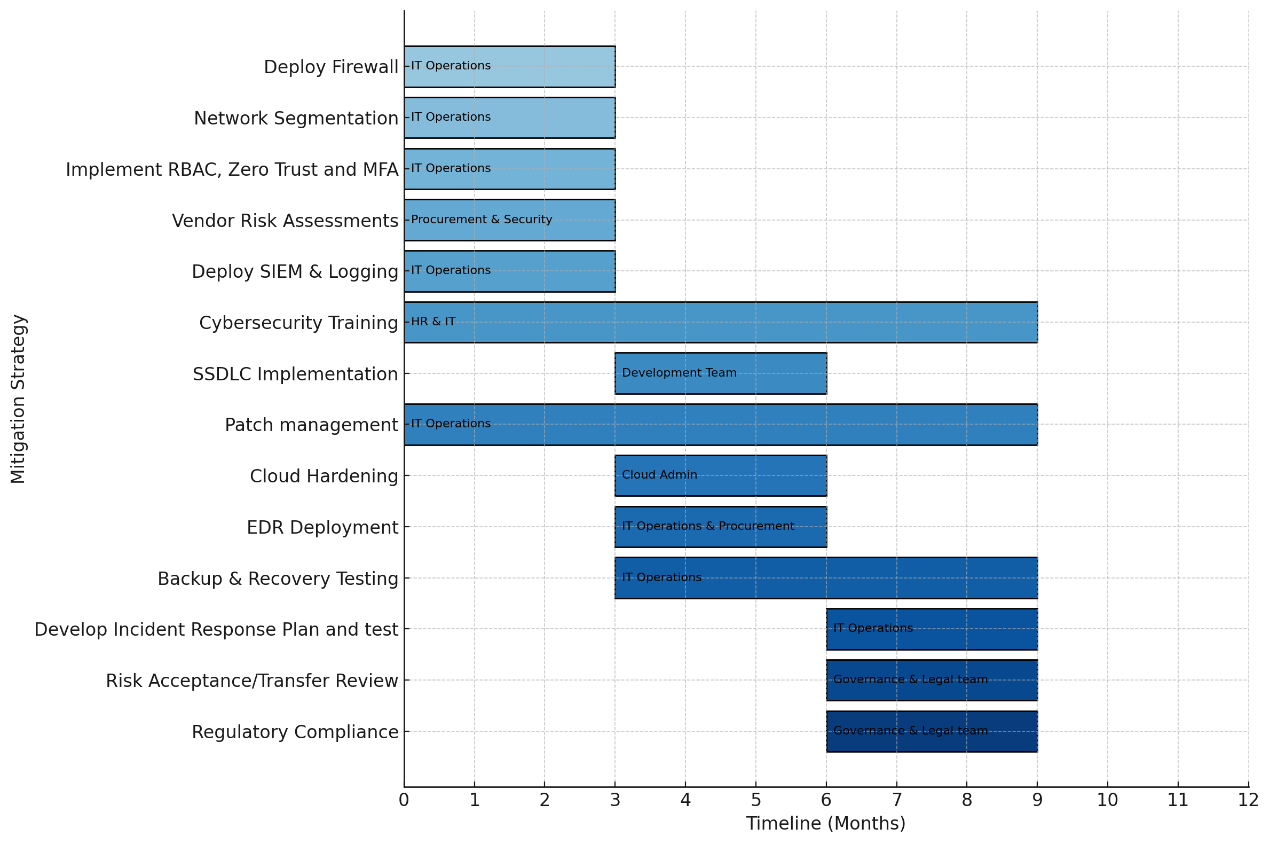
Figure 4: Implementation Gantt Chart
5.2 Monitoring and Review
To ensure that the implementation plan has the intended results, a monitoring and review process will be incorporated, which will be aligned to the Detect and Respond functions of the NIST framework.
Each mitigation strategy will be monitored based on its criticality as detailed below:
- SIEM tools will be used to track any anomalies in the network, offering insights to firewalls and EDR tools.
- Cybersecurity awareness training will be measured using employee participation rates as well as test results to assess the impact of the training.
- Patch management: Software update logs will be reviewed monthly.
- Backup and Recovery testing: Backups will be tested regularly to ensure their effectiveness, and remedies implemented in case of failure
- Incidence response plan testing: Tabletop exercises will be conducted quarterly to ensure their effectiveness.
- Vendor evaluation tools will be monitored for progress based on the number of existing vendors.
5.3 Metrics and Reporting
To effectively evaluate the impact of the mitigation strategies, a defined set of key performance indicators will be used, which will entail both quantitative and qualitative metrics. The metrics will be used to track progress, flag issues for revision, and assist in making data-driven decisions. The table below summarises these metrics
|
Category |
Metrics |
|
Detection and Monitoring |
Mean Time to Detect (MTTD) |
|
Number of SIEM alerts resolved/Total number of alerts |
|
|
% of network coverage by NIDS |
|
|
Response and Recovery |
Mean Time to Respond (MTTR) |
|
RPO success rates from recovery tests |
|
|
RTO success rates from recovery tests |
|
|
Number of IR drills conducted, lessons captured |
|
|
Compliance and Governance |
Number of compliance gaps identified |
|
Third-party compliance audit results |
|
|
%Regulatory certification achieved |
|
|
Training and Awareness |
% of staff completing security training |
|
Reported suspicious activity count |
|
|
Awareness test failure rate |
|
|
Deployment of Preventive controls |
% of systems with MFA enabled |
|
% of vendor contracts with security clauses |
|
|
% of endpoints covered by EDR solutions |
|
Table 13: Monitoring Metrics
The metrics above will be included in the reports, which will be done on two levels: operational, for review by the security operations team, and the executive level, which will be reviewed by the senior leadership and risk management committee.
The operations reports will be sent monthly, while the executive reports will be sent out on a quarterly basis by the respective task owners. In the event of significant incidents, an immediate escalation will be triggered through the predefined escalation matrix to all concerned stakeholders.
5.4 Continuous Improvement
As the threat landscape is continuously evolving, continuous improvement will be a key part of the organisation’s risk management strategy. The organisation will align to the NIST framework Respond and Recover functions by reviewing the entire risk management strategy biannually, as well as when triggered, with the objective of reviewing the performance of the implemented controls from the reports shared within the period of evaluation. In addition, utilising threat intelligence and event data collected to fine-tune the mitigation strategies to adapt to the ever-evolving threat landscape.
A feedback control mechanism will also be implemented in the various processes outlined below:
- Conduct post-incident reviews to establish root causes and update the risk mitigation strategies from the lessons learnt from the incidents.
- Surveys and tests will be sent out to participants after cybersecurity awareness training to identify areas of improvement.
- Actionable items will be expected after the tabletop exercises to ensure the incident response plan aligns with the overall business objectives and can be used for business continuity in case of incidents.
- Conduct vendor review meetings to establish progress on the controls and ensure the vendor assessment is also done for new vendors.
- The reports will be used to identify trends and gaps for improvement.
To ensure a good cybersecurity hygiene strategy, the organisation will be expected to maintain a strong policy framework that ensures every employee understands their roles and responsibilities in securing the digital assets. Some of these policies include a Cybersecurity Policy and a Remote Working Policy, amongst others.
6. Conclusion And Recommendations
6.1 Summary
In summary, this study presents a framework for mitigating ransomware attacks within supply chain environments. Drawing from Maersk’s experience during the NotPetya attack, the study highlights how threat actors exploit vulnerabilities in third-party systems and use lateral movement techniques to compromise an organisation’s internal infrastructure. High-value digital assets such as third-party platforms, cloud services, and open-source libraries can become critical vulnerabilities when inadequately secured. A lack of visibility and security oversight across vendor relationships creates blind spots that are frequently exploited during supply chain attacks. Maersk’s flat network architecture enabled the rapid spread of the malware, showing the importance of network segmentation to contain threats. Furthermore, the absence of a formal incident response plan significantly prolonged operational downtime, contributing to substantial financial losses. Key mitigation strategies identified include vendor risk management to ensure alignment with the organisation’s security posture, and the implementation of technical controls such as endpoint detection and response, firewalls, and multi-factor authentication to limit exposure. Network segmentation is essential to isolate infected systems, reduce recovery time, and minimise damage. By adopting this mitigation framework, combined with continuous improvement, organisations can enhance their resilience and better respond to the evolving threat landscape.
6.2 Recommendations
This study has shown the importance of cybersecurity in any organisation and highlights how negligence of mitigation strategies can be quite catastrophic, as evidenced from Maersk’s attack. Maersk had not anticipated becoming a victim of a cyberattack, yet the Notpetya attack crippled its global operations, temporarily disrupting nearly 20% of the global shipping capacity (Steinberg, Stepan and Neary, 2021). Unfortunately, the threat landscape is evolving rapidly, and threat actors are constantly striving to outpace technological advancements. Therefore, the framework suggested in this study is essential for every organisation regardless of its size. This study primarily recommends the adoption of a defence-in-depth (DiD) strategy, which comprises of a multilayered approach. It integrates physical, technical, personnel, and procedural controls to mitigate vulnerabilities and strengthen the organisational resilience against cyberattacks. Personnel controls limit vulnerabilities due to human actors, such as vendors and employees, and include awareness training and the use of governance policies such as the Zero Trust policy. Physical controls limit vulnerabilities by limiting physical access to digital assets and may include perimeter defence and biometrics. Procedural controls limit vulnerabilities associated with poorly managed procedures, while technical controls limit vulnerabilities caused by technological flaws and include endpoint protection and network segmentation (Datta and Acton, 2023).
Some emerging issues in cybersecurity are also rapidly changing the threat landscape in supply chains. The rise of ransomware-as-a-service (RaaS) has lowered the barrier of launching ransomware attacks even for non-skilled threat actors (Datta and Acton, 2024). Geopolitical tensions and the rise of hacktivism also introduce vulnerabilities within global supply chains, which, if exploited, can trigger cascading effects that disrupt not only individual organisations but entire industries (Bednarski et al., 2025). As supply chains often span multiple countries and jurisdictions, they are particularly susceptible to politically motivated cyberattacks and ideologically driven campaigns. Organisations must keep up with the threat intelligence to ensure their migration strategies evolve with time.
Future studies aligned with this research could explore emerging risks in the supply chain introduced by advancing technologies. One critical area is the rise of AI-driven cyberattacks, particularly as supply chain management systems increasingly integrate artificial intelligence (Akinsuli, 2024). Investigating how AI can both enhance and threaten supply chain security will be vital. Additionally, future research could examine the application of blockchain technology to secure supply chain transactions and improve traceability, particularly in verifying the origin and integrity of software components.
6.3 Future Work
To enhance the proposed risk management framework, there are several areas identified for future research work. One critical area is automation of regulatory compliance with regulatory technology solutions (RegTech) that would be essential to ensure organisation policies align with industry standards such as DORA, GDPR, and the EU AI Act (Olaiya et al., 2024).Additionally, using AI-driven behavioural analytics to monitor employees and third-party vendors can proactively detect anomalies, which could be indications of phishing and social engineering threats, and organisations can take precautions. Finally, integrating cyber risk quantification models such as the FAIR methodology could be used to convert technical risks assessments into measurable financial metrics that can be presented at the executive level to make informed decisions (Wang, Neil and Fenton, 2019).
6.3.1 Limitations
While every effort was made to ensure a thorough risk management exercise, there were several limitations encountered. Due to contractual restrictions and data privacy policies, access to the organisation and vendor data was not possible, necessitating the use of data from existing case studies done on this attack. Time constraints due to the academic deadlines also limited the depth of the study. Moreover, the dynamic nature of the cyber threat landscape poses a challenge, as the risk management framework represent only the current state. Hence, continuous improvement and updates are required.
Greenberg, A. (2018) ‘The Untold Story of NotPetya, the Most Devastating Cyberattack in History’, Wired, 22 August. Available at: https://www.wired.com/story/notpetya-cyberattack-ukraine-russia-code-crashed-the-world/
Aljoghaiman, A. & Sundram, V.P., 2023. Mitigating Ransomware Risks in Supply Chains. International Journal of Cyber Criminology.
Cartwright, A. & Cartwright, E., 2023. The Economics of Ransomware Attacks on Digital Supply Chains. Digital Threats Research.
Hammi, B., Zeadally, S. & Nebhen, J., 2023. Security Threats, Countermeasures, and Challenges of Digital Supply Chains. ACM Computing Surveys.
Robinson, A., Corcoran, C., & Waldo, J., 2022. New Risks in Ransomware: Supply Chain Attacks and Cryptocurrency. Harvard Kennedy School, Belfer Center for Science and International Affairs.
Yeboah-Ofori, A. et al., 2021. Cyber Threat Predictive Analytics for Improving Cyber Supply Chain Security. IEEE Access.
Barbosa, J.A.D.S. & Franco, D.P. (n.d.) Security in Depth: Rakshasa Hardware Backdoor Analysis. São Paulo, Brazil: Cybersecurity Researcher.
Aggarwal, M. (2023) Ransomware Attack: An Evolving Targeted Threat. Ministry of Electronics & IT, Delhi, India. IEEE 14th ICCCNT Conference.
Amin, M. (2024) ‘The Importance of Cybersecurity and Protecting of Digital Assets and Understanding the Role of Cybersecurity Laws in Safeguarding Digital Assets’, Indian journal of public administration, 70(3), pp. 493–501. Available at: https://doi.org/10.1177/00195561241271520.
Ghanbari, H., Koskinen, K. and Wei, Y. (2024) ‘From SolarWinds to Kaseya: The rise of supply chain attacks in a digital world’, Journal of information technology teaching cases [Preprint]. Available at: https://doi.org/10.1177/20438869241299823.
Maersk (2025) https://www.maersk.com/. Available at: https://www.maersk.com/about/ (Accessed: 11 March 2025).
Rose, S. et al. (2020) ‘Zero Trust Architecture’. Special Publication (NIST SP), National Institute of Standards and Technology, Gaithersburg, MD. Available at: https://doi.org/https://doi.org/10.6028/NIST.SP.800-207.
Steinberg, S., Stepan, A., and Neary, K. (2021) NotPetya: A Columbia University Case Study. New York: Columbia University School of International and Public Affairs. Available at: https://www.sipa.columbia.edu/sites/default/files/2022-11/NotPetya%20Final.pdf
Billoir, E., Laborde, R., Wazan, A.S., Rütschlé, Y., and Benzekri, A. (2024) ‘Implementing the principle of least administrative privilege on operating systems: challenges and perspectives’, Annals of Telecommunications, 79(7–8), pp. 857–880. Available at: https://doi.org/10.1007/s12243-024-01033-5 (Accessed: 11 March 2025).
Krumay, B., Bernroider, E.W.N. and Walser, R. (2018) ‘Evaluation of cybersecurity management controls and metrics of critical infrastructures: A literature review considering the NIST cybersecurity framework’, in Gruschka, N. (ed.) Secure IT Systems. NordSec 2018. Lecture Notes in Computer Science, vol. 11252. Cham: Springer, Available at: https://doi.org/10.1007/978-3-030-03638-6_23 (Accessed: 10 March 2025).
Roy, S., Panaousis, E., Noakes, C., Laszka, A., Panda, S., and Loukas, G. (2023) ‘SoK: The MITRE ATT&CK Framework in Research and Practice’. arXiv preprint.
Ahmed, M. G., Panda, S., Xenakis, C., & Panaousis, E. (2022). MITRE ATT&CK-driven cyber risk assessment. In Proceedings of the 17th International Conference on Availability, Reliability and Security (ARES 2022) (pp. 1–10). ACM. https://doi.org/10.1145/3538969.3544420
Kwon, R., Ashley, T., Castleberry, J., McKenzie, P., & Gupta, S. N. (2023). Cyber Threat Dictionary using MITRE ATT&CK Matrix and NIST Cybersecurity Framework Mapping. Pacific Northwest National Laboratory. https://doi.org/10.1109/TBD.2023.1000000
Datta, P.M. and Acton, T., 2023. Did a USB drive disrupt a nuclear program? A Defense in Depth (DiD) teaching case. Journal of Information Technology Teaching Cases, 0(0), pp.1–11. Available at: https://doi.org/10.1177/20438869231200284
Datta, P.M. and Acton, T., 2024. Ransomware and Costa Rica’s national emergency: A defense framework and teaching case. Journal of Information Technology Teaching Cases, 14(1), pp.56–67. Available at: https://doi.org/10.1177/20438869221149042
Bednarski, L., Roscoe, S., Blome, C. and Schleper, M.C., 2025. Geopolitical disruptions in global supply chains: a state-of-the-art literature review. Production Planning & Control, 36(4), pp.536–562. Available at: https://doi.org/10.1080/09537287.2023.2286283
Akinsuli, O., 2024. AI-powered supply chain attacks: A growing cybersecurity threat. IRE Journals, 8(3), p.696. Available at: https://irejournals.com/paper-details/1706490
Olaiya, O.P., Adesoga, T.O., Pieterson, K., Obani, O.Q., Adebayo, J.O. and Ajayi, O.O., 2024. RegTech solutions: Enhancing compliance and risk management in the financial industry. GSC Advanced Research and Reviews, 20(2), pp.8–15. Available at: https://doi.org/10.30574/gscarr.2024.20.2.0295
Wang, J., Neil, M. and Fenton, N., 2019. A Bayesian network approach for cybersecurity risk assessment: Implementing and extending the FAIR model. Computers & Security, [online] Available at: https://doi.org/10.1016/j.cose.2019.101659
Khan, W., 2023. Improving incident response times through efficient Security Operations Center (SOC) management: Techniques to reduce the mean time to detect and respond (MTTD/MTTR). International Journal of Core Engineering & Management, 7(6), p.115 https://ijcem.in/wp-content/uploads/IMPROVING-INCIDENT-RESPONSE-TIMES-THROUGH-EFFICIENT-SECURITY-OPERATIONS-CENTER-SOC-MANAGEMENT-TECHNIQUES-TO-REDUCE-THE-MEAN-TIME-TO-DETECT-AND-RESPOND.pdf
European Dental Group, 2022. Cyber Security Policy. [pdf] European Dental Group. Available at: https://www.europeandentalgroup.eu/wp-content/uploads/2022/05/20211208-cyber-security-policy-def.pdf