3 Chapter 3
Assessing Cybersecurity Preparedness in Distributed Public Healthcare Systems: A Focus on the Irish Health Service
Eva Holland
Darragh Mongan
David McCormack
David O Grady
Preamble
The Health Service Executive (HSE) is Ireland’s publicly funded healthcare system, responsible for delivering medical and social care services nationwide. It oversees hospitals, clinics and community health services, managing critical IT infrastructure, electronic health records (EHRs) and interconnected medical systems essential for patient care and operational efficiency.
This study focuses on HSE’s cybersecurity risk management, specifically governance, compliance, technical security controls and incident response in alignment with NIS2, GDPR and ISO 27001. It examines cyber threats such as ransomware, phishing and outdated IT systems, evaluating the effectiveness of current security measures and identifying areas for improvement.
Reasons for Choice
The HSE is a high-value target for cyberattacks due to its vast digital infrastructure and sensitive patient data. The 2021 Conti ransomware attack exposed critical vulnerabilities, causing widespread service disruptions and highlighting weaknesses in cybersecurity preparedness. Given its role in national healthcare, improving HSE’s cybersecurity resilience is vital for protecting patient data while also ensuring regulatory compliance and maintaining essential healthcare services.
By analysing the HSE’s cybersecurity posture, regulatory adherence and response strategies, this study provides valuable insights to strengthen risk management, governance frameworks and cyber resilience within Ireland’s healthcare system.
Executive Summary
The HSE faces elevated cybersecurity risks due to its complex, distributed infrastructure, reliance on outdated IT systems and the sensitive nature of its data. The 2021 Conti ransomware attack severely disrupted services, exposed patient records and highlighted serious gaps in governance, technical controls and compliance. As the healthcare sector becomes increasingly digital, the HSE remains a prime target for ransomware, phishing, insider threats and third-party attacks, demonstrating the urgent need for a robust cybersecurity risk management strategy.
This study evaluates the HSE’s cybersecurity preparedness through a mixed-methods approach, including risk identification, threat analysis, vulnerability assessment and regulatory alignment. Drawing from case studies such as the Conti and NHS ransomware attacks, the study developed a risk register and heat map informed by best practices under NIS2, GDPR and ISO 27001. A multi-phase implementation plan is proposed, including technical upgrades (e.g. multi-factor authentication, network segmentation, real-time monitoring), governance enhancements (e.g. CISO leadership, updated policies, incident response plans) and investment in staff training to reduce human-factor risks.
Addressing these risks will reduce the likelihood of future disruptions and legal penalties while restoring public trust. The study provides a strategic roadmap tailored to public healthcare, ensuring compliance with EU legislation and boosting the HSE’s long-term cyber resilience through improved detection, response and risk awareness.
Cybersecurity is critical to protecting healthcare delivery and patient data. This study shows that with coordinated investment in systems, governance and staff capabilities, the HSE can significantly reduce cyber risk and strengthen public confidence.
1.1 Background
In today’s rapidly evolving digital environment, cybersecurity is essential for organisational resilience, particularly in sectors handling sensitive data, such as healthcare. Cybersecurity refers to the protection of systems, networks and data from cyber threats (Schiliro, 2022). Organisational resilience in this context depends on security measures, technologies and best practices designed to mitigate cyber risks, including malware, phishing and ransomware attacks. The increasing sophistication of cyber threats highlights the urgent need for a robust risk management strategy.
Cybersecurity risk management involves identifying, assessing and mitigating threats to information systems. A critical aspect of this process is threat detection, which focuses on identifying potential cyberattacks before they cause harm. Vulnerability assessments play a crucial role in evaluating system weaknesses that could be exploited, while incident response ensures a structured approach to addressing security breaches effectively. Compliance with regulatory frameworks is equally important, particularly in the healthcare sector, where regulations such as the General Data Protection Regulation (GDPR) and the Network and Information Systems Directive (NIS2) impose stringent requirements for safeguarding patient data and maintaining operational continuity.
Healthcare organisations are a primary target for cybercriminals due to the high value of patient data on the black market. Clarke et al. (2024) emphasise that healthcare data is among the most valuable, making hospitals and medical institutions frequent targets. A successful cyberattack can disrupt critical operations, compromise patient privacy and lead to severe financial and reputational consequences. This growing threat underscores the necessity for healthcare organisations to implement comprehensive cybersecurity risk management strategies.
1.2 Objectives
The objective of this study is to assess cybersecurity preparedness in distributed public healthcare systems with a focus on the HSE by identifying vulnerabilities, compliance gaps and areas for improvement. Given the increasing sophistication of cyber threats due to new technologies (HSE, 2024) and the fact the healthcare sector is now the most breached sector according toKroll (2025, see figure 1 below), it is essential to evaluate the organisation’s ability to protect patient data, maintain system integrity and ensure service continuity in the face of increasing cyber risks.
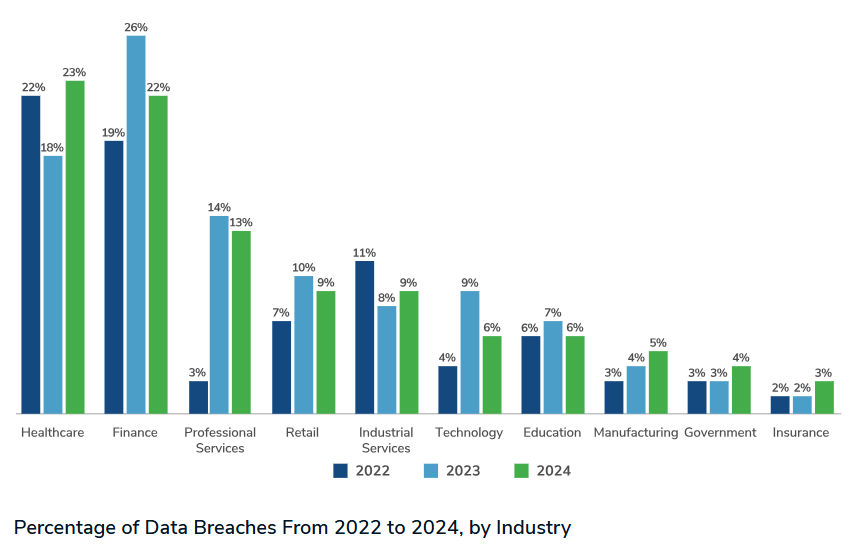
Figure 1 – Healthcare Now Most Breached (Kroll, 2025)
The study addresses the following key objectives:
Evaluate the HSE’s cybersecurity posture by conducting a gap analysis and comparing our findings to best practices to form an action plan for the HSE. Using a combination of insights from both The Conti cyber-attack report and the HSE’s statement of strategic intent 2024-2027, were possible we plan on comparing these two reports and further investigating where improvements can be made.
Assess compliance readiness, focusing on HSE’s adherence to regulatory requirements. The study examines whether the organisation effectively implements legal obligations concerning data protection, incident reporting and third-party security management.
A survey assesses cybersecurity awareness and training among healthcare students, providing a fresh perspective on how future professionals perceive and manage cyber risks. The study identifies gaps in knowledge and training that could contribute to human-related vulnerabilities.
The study provides research- and data-driven recommendations to enhance HSE’s cyber resilience, improve regulatory compliance and strengthen incident response capabilities within Ireland’s public healthcare system.
1.3 Scope
The study examines the HSE’s cybersecurity preparedness with an emphasis on risk management, vulnerabilities and NIS2 compliance. It assesses if the HSE’s governance frameworks and cybersecurity efforts are suitable to handle changing threats.
The study evaluates the effectiveness of incident response procedures while analysing cybersecurity concerns like ransomware, phishing and outdated IT systems. The study draws attention to the importance of a specialised cybersecurity department, awareness gaps in training and difficulties with NIS2 compliance and it may recommend structural and policy changes. Evaluations of the infrastructure may reveal outdated systems that need to be updated.
The study’s goal is to offer practical suggestions for enhancing the HSE’s incident response, regulatory compliance and cyber resilience to protect data and maintain essential healthcare services.
1.4 Approach
Given the complexity of the HSE’s distributed healthcare system and the lessons from the 2021 Conti ransomware attack, this study adopts established cybersecurity risk management frameworks to assess existing controls, identify vulnerabilities and highlight systemic gaps. The goal is to deliver a strategic roadmap and actionable recommendations to enhance HSE’s resilience and ensure alignment with emerging regulations, particularly the NIS2 Directive.
The research benchmarks HSE’s policies and practices against recognised best practices, including:
- Strengthening cybersecurity culture through regular employee training to reduce human error and social engineering risks.
- Enforcing third-party vendor compliance with strong cybersecurity standards.
- Ensuring rapid incident reporting to the National Cyber Security Centre (NCSC) and the Data Protection Commission (DPC) within 24 hours, with full reports completed within one month.
- Conducting regular audits, risk assessments and real-time system monitoring (NCSC, 2023).
NIS2 is the primary framework due to its direct applicability to public healthcare, with requirements for incident response, supply chain security and accountability. ISO/IEC 27001 is also considered, offering a complementary, risk-based structure for continuous improvement in security governance.
2.1 Asset Identification & Risk Register
The HSE manages a vast and complex IT ecosystem, spanning 54 acute hospitals and over 4,000 locations and supporting approximately 130,000 staff (HSE, 2024). This infrastructure includes more than 4,500 servers and 70,000 end-user devices, along with critical digital assets such as electronic health records, clinical applications, and extensive patient data repositories (PwC, 2021). In total, the HSE operates over 1,000 applications across clinical and administrative functions (PwC, 2021).
Human assets are critical to maintaining cybersecurity, yet the HSE’s IT workforce – approximately 350 personnel – is stretched thin, leaving a small, dedicated team to handle cybersecurity responsibilities (PwC, 2021). Privileged IT administrators and third-party service providers with network access represent particularly high-risk user groups.
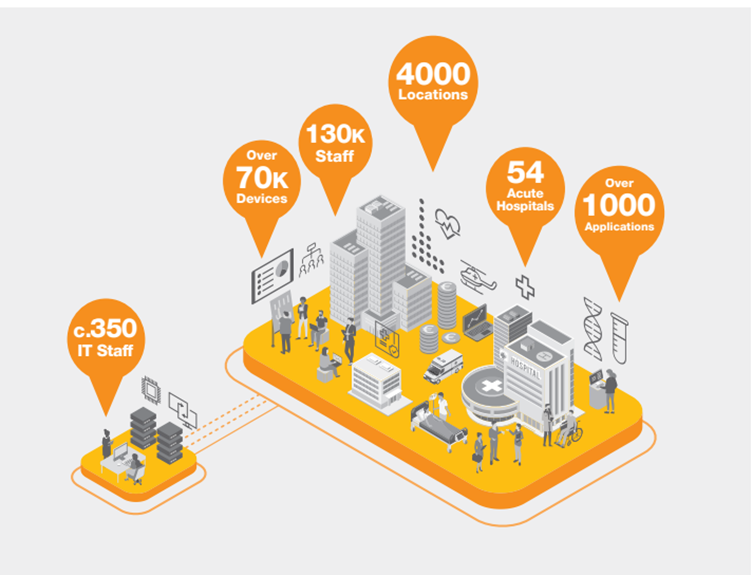
Figure 2 – Scale of the HSE (PwC, 2021)
HSE must prioritise assets vital to healthcare delivery and patient safety. Physical infrastructure (hospital networks, clinical workstations, biomedical devices) is crucial, as downtime affects patient care (Argaw et al., 2020). Digital assets, such as patient databases and clinical software, ensure confidentiality and data integrity (Argaw et al., 2020).
The lack of a centralised asset inventory hindered HSE’s 2021 cyberattack response (PwC, 2021), leading to the recommendation to develop a comprehensive asset register mapped to critical services.
Before 2021, HSE lacked dedicated security leadership, with no Chief Information Security Officer (CISO) or Security Operations Centre (SOC). Following the attack, new senior roles (CISO, Chief Technology & Transformation Officer) were established to drive reforms (PwC, 2021). Cybersecurity training is now a priority, addressing previous gaps in awareness.
The Network infrastructure, particularly the National Healthcare Network (NHN), is a vital asset. However, the NHN’s design prior to 2021 was essentially a “flat,” unsegmented network to ease staff access to systems.
2.2 Threat Identification
The HSE faces major cyber threats, including ransomware, phishing, insider threats, and third-party risks (Ponemon Institute, 2021). Ransomware remains the most severe, as demonstrated by the May 2021 Conti attack, which disabled HSE’s IT systems, delayed 80% of appointments and led to the exposure of patient data on the dark web (HSE, 2021). The attack resulted in 473 lawsuits and highlighted the severity of ransomware’s impact on patient safety and service continuity (PwC, 2021).
Phishing remains a primary attack vector. The Conti group initially gained access to HSE systems via a spear-phishing email in November 2020, with the infection persisting until ransomware was deployed in May 2021 (HSE, 2021). Attackers also used fraudulent emails and texts post-attack to exploit public uncertainty (PwC, 2021).
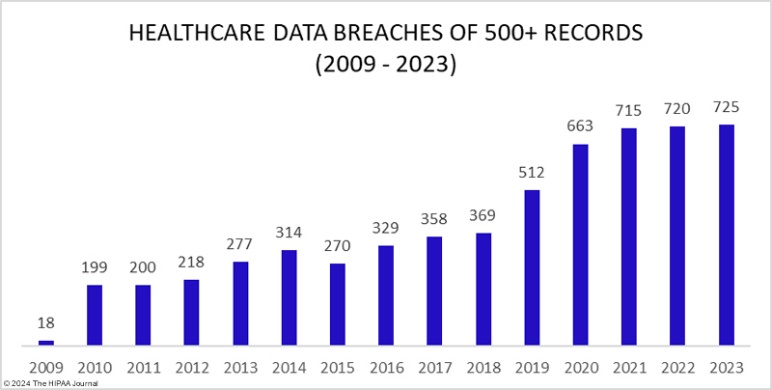
Figure 3 – Health Care Breaches 2009-2023 HIPAA Journal (2024)
Insider threats arise from negligence, such as weak passwords and misdirected emails, or from malicious actions such as data theft and privilege abuse (Verizon, 2022). Studies indicate that 81% of healthcare data breaches result from human error (Ponemon Institute, 2021). To mitigate any potential risk to its security posture, the HSE responded by banning personal email and external storage for work data (HSE, 2021).
Third-party risks stem from HSE’s interconnected IT network, including voluntary hospitals and external vendors. The Conti attack also targeted the Department of Health, highlighting cross-network risks (HSE, 2021). Mitigating these threats requires comprehensive security measures, including cyber hygiene, staff training and regular, robust supply chain oversight (PwC, 2021).
2.3 Vulnerability Assessment
The PwC Independent Post Incident Review (PwC, 2021) identified significant weaknesses in the HSE’s IT environment that left it highly susceptible to cyberattacks.
A major issue was the widespread use of legacy systems. As of 2021, around 40,000 employees were using Windows 7, despite Microsoft having discontinued support a year earlier. Legacy systems are common in healthcare due to upgrade costs and concerns over service disruption, with 73% of Irish healthcare services still relying on outdated technology (Harmony Healthcare IT, 2024).
Another critical flaw in their IT environment was the fact they operated on a flat network topology, essentially meaning anyone who successfully infiltrated the system could laterally move within the network into privileged accounts (PwC, 2021). To add further risk to this, Multi-Factor Authentication (MFA) was not enforced on all remote access methods.
The HSE had assessed their own cybersecurity maturity as low (HSE, 2024). Instead of robust security measures, they relied on basic antivirus software with no endpoint detection and response (EDR) tools and no intrusion detection system (IDS) to monitor the network. The lack of fundamental cybersecurity measures is what allowed the Conti ransomware group to remain undetected within the system for 2 months.
2.4 Risk Scenarios
The HSE is exposed to multiple cybersecurity risks affecting the confidentiality, integrity and availability (CIA) of its systems. Three core scenarios highlighted in the PwC, 2021 report, these risks are:
A ransomware attack, similar to the 2021 Conti incident could again paralyse HSE’s infrastructure. That attack led to 80% drop-in services, widespread appointment cancellations and emergency disruptions. Exfiltrated patient data raised serious confidentiality concerns and GDPR implications.
A phishing or insider threat could enable unauthorised access to electronic health records, exposing sensitive data on the dark web as seen in Conti’s aftermath. Beyond privacy breaches, attackers could tamper with patient records, posing integrity risks such as incorrect diagnoses or treatments.
HSE’s dependence on connected medical devices (e.g. MRI, infusion pumps) introduces risk if malware compromises device functionality or disrupts communication. During the Conti attack, even though devices weren’t directly targeted, many failed due to loss of IT support services.
These scenarios highlight the urgent need for improved cyber defences, particularly in system segmentation, monitoring and device security.
3.1 Risk Register & Analysis
A detailed risk register outlining the most pressing cybersecurity threats facing the HSE, including phishing, legacy system vulnerabilities and third-party risks has been developed and is presented in appendix 1. Each risk is assessed based on likelihood and impact with scores used to prioritise mitigation strategies.
3.2 Risk Evaluation
As Ireland’s national healthcare provider, the HSE must maintain service continuity, protect patient data and comply with regulations such as GDPR and NIS2. Cybersecurity risks that undermine these goals require careful evaluation in line with the organisation’s risk appetite and operational objectives:
- Ensure system availability across hospitals, clinics and emergency services.
- Maintain regulatory compliance to avoid fines and reputational damage.
- Minimise financial and operational disruption from cyber incidents.
- Preserve public confidence in the healthcare system (HSE, 2024).
Based on these risks they have been classified according to severity and tolerance:
Unacceptable Risks (Critical/High: Must Be Eliminated or Minimised)
Phishing Attacks (Risk ID: 1) This is a high-frequency attack vector and has been the entry point for major breaches (e.g., Conti ransomware in 2021).
Exploitation of Legacy/Unpatched Systems (Risk ID: 2) HSE still uses outdated technology, making it a major vulnerability. A single unpatched system can compromise the entire network.
Data Breaches (Risk ID: 3) HSE holds millions of sensitive patient records. A breach would violate GDPR, result in large fines and damage public trust.
Manageable Risks (Medium: Requires Strict Controls and Monitoring)
Supply Chain Attacks (Risk ID: 4) While not as frequent as phishing or ransomware, a third-party compromise can provide attackers an indirect path into HSE systems. Data Manipulation (Risk ID: 5) Though rare, this risk can severely impact patient safety.
3.3 Risk Matrix
The risk matrix was developed using a structured methodology aligned with best practices in cybersecurity risk management. The process began with risk identification, focusing on key scenarios such as phishing, system vulnerabilities, data breaches, third-party compromise and data manipulation. Each risk was clearly articulated, as precise definitions are essential for effective mitigation (Hopkin, 2018).
Root causes such as insufficient training, outdated systems and weak access controls were then assessed, since addressing these can reduce the likelihood of risk occurrence (Whitman & Mattord, 2021). Potential impacts, including service disruption, data loss and regulatory penalties, were also defined to inform effective response strategies (Peltier, 2016).
Risks were then rated by assigning scores (1–3) for both likelihood and impact, which were multiplied to produce an overall risk score. Risks such as phishing, system exploitation and data breaches each received a top score of 9, identifying them as high-priority threats.
The implications of this matrix are profound for risk management within healthcare systems. It highlights areas requiring urgent attention and resource allocation, such as cybersecurity awareness training, robust access controls and proactive patch management (NIST, 2018). Additionally, it shows the importance of continuous monitoring, vendor management and regulatory compliance. Ultimately, adopting this structured approach improves organizational resilience, patient safety and regulatory compliance, significantly reducing potential financial and reputational damages (Hopkin, 2018).
3.4 Professional Insight: Interview with HSE ICT Personnel
To strengthen the qualitative aspect of our risk assessment, we conducted an interview (see appendix 3 for full questions) with an experienced ICT professional currently working within the HSE. This provided invaluable firsthand insight into the operational, cultural and strategic challenges faced during and after the 2021 Conti ransomware attack.
Key Insights:
Immediate Operational Impact
The professional confirmed that the 2021 attack severely disrupted hospital operations, including appointment cancellations, diagnostic delays and internal communication breakdowns. Identifying patients manually was a key issue.
Incident Response Challenges
Although a formal Incident Response Plan existed, it was not sufficient due to the malware existing within the HSE architecture for over 60 days. The sophistication of the attack and the scale of the organisation presented challenges within the lesser-advanced hospitals for quick recovery following the attack, this meant that in some cases in order to restore some of the systems they had to go back more than 60 days on backups.
Post-Incident Improvements
Substantial changes followed the attack, including the appointment of a CISO, improved policies and more structured training programs. However, concerns were raised about the pace of implementation and funding constraints.
Outlook on Strategic Intent (2024–2027)
The professional expressed cautious optimism regarding the HSE’s Strategic Statement of Intent. The professional believes that it is achievable, but it will require a huge amount of funding.
Cybersecurity in Medical Curricula
A strong recommendation was made to integrate cybersecurity awareness training into nursing and medical education, given the frequency of accidental data exposure incidents by clinical staff.
Infrastructure Readiness
The HSE’s current ICT infrastructure was described as still heavily reliant on legacy systems, despite recent upgrades. Progress has been made as of last year (2024) that all legacy systems have been upgraded to windows 10. This coming year they plan to successfully implement windows 11 onto all legacy systems but resource limitations continue to hinder faster modernisation.
Insufficient Resources
The professional, also highlighted the lack of funding which has been invested into the cybersecurity posture of the HSE due to it being a government agency. The professional estimates that HSE spending on cybersecurity is roughly 2% when in a private organisation of the same size it would be minimum of 5% of budget.
3.5 Student Insight: Health Care Student Survey

Figure 4 – Most Common Words
The word cloud highlights that participants overwhelmingly linked improved cybersecurity awareness with training, particularly in areas such as phishing, cyber hygiene and structured courses. Common suggestions focused on making cybersecurity education mandatory, practical and tailored to healthcare staff.
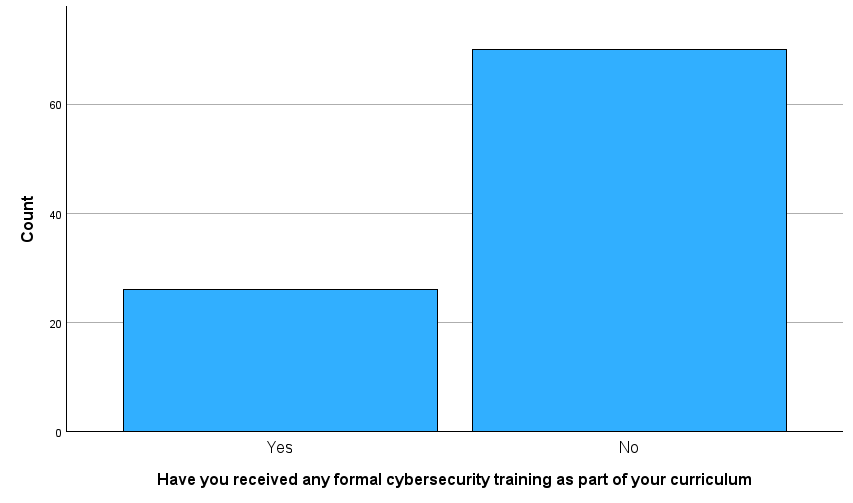
Figure 5 – Bar Chart Formal Training
Only 28% of respondents had received formal cybersecurity training as part of their academic curriculum. This figure should aim to be much closer to 100%.
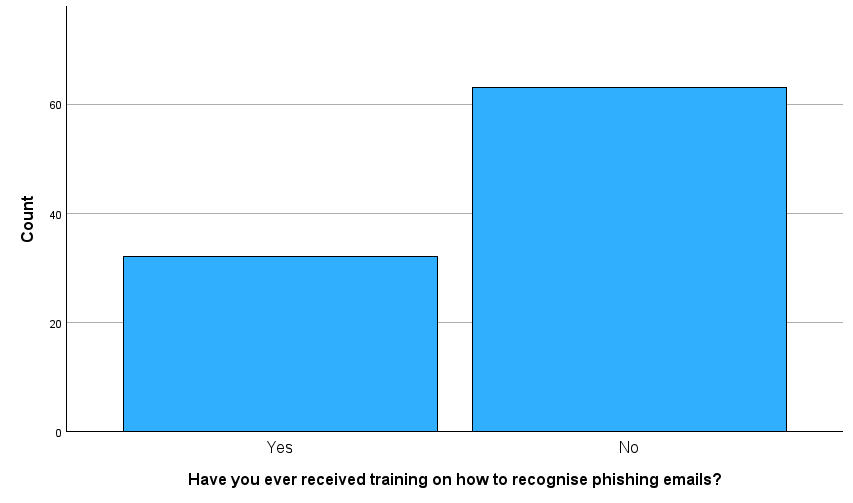
Figure 6 – Phishing Training
This chart reveals a concerning gap in cybersecurity awareness: a significant majority of respondents (over 60) reported not having received training on how to recognise phishing emails compared to just over 30 who had. Given that phishing remains one of the most common initial attack vectors for ransomware and data breaches, particularly in the healthcare sector this lack of training highlights a serious human vulnerability within the system.
Without proper awareness, staff are more likely to fall victim to phishing attempts that could compromise patient data, disrupt services, or trigger large-scale incidents like the 2021 Conti attack on the HSE. This underscores the urgent need for mandatory, role-specific training on phishing detection and secure email behaviour as part of any effective cybersecurity strategy.
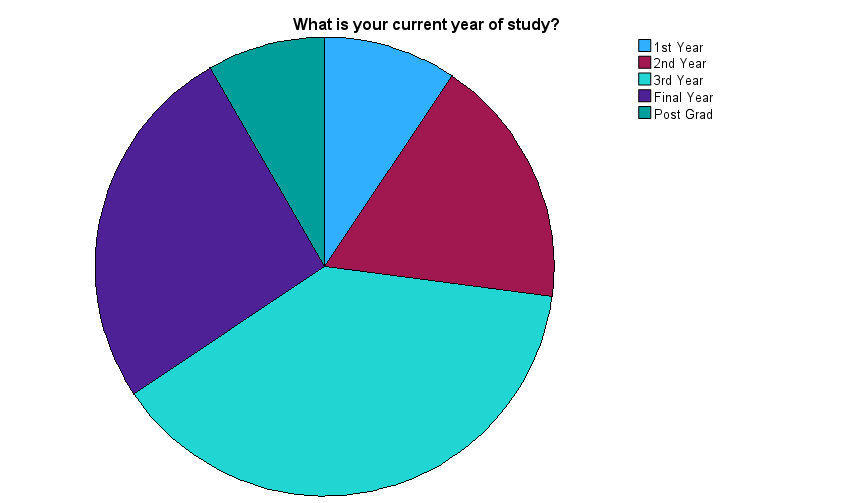
Figure 7 – Year of Study
This pie chart illustrates the academic distribution of respondents by year of study. The largest segment consists of third-year students, followed by a substantial proportion in their final year and postgraduate programmes. Smaller portions represent first and second-year students.
This spread is significant because it suggests that most participants are in the later stages of their academic journey, potentially on the verge of entering the workforce. Yet, as shown in the phishing training chart, a majority have never received basic cybersecurity training, a troubling disconnect. These findings highlight a systemic gap in security education at the undergraduate and postgraduate levels, especially given the increasing threat landscape across sectors like healthcare.
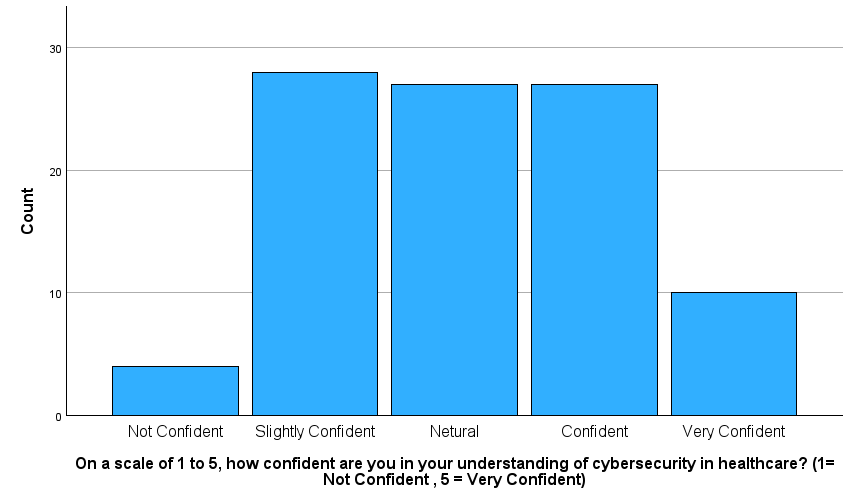
Figure 8 – Understanding Cybersecurity
This bar chart shows that while many respondents rate themselves as neutral, slightly confident, or confident in their understanding of cybersecurity in healthcare, only a small proportion feel very confident and a few openly admit they are not confident at all.
This spread indicates there is a moderate baseline awareness, deep and applied understanding is lacking which is especially concerning for a sector that manages critical and sensitive data like patient health records. Combined with the earlier finding that most respondents have never received phishing training, this suggests a potentially dangerous overestimation of personal cybersecurity readiness.
It underlines the need for structured, sector-specific training in cybersecurity for healthcare professionals and students, ideally embedded into academic programmes and supported by practical, scenario-based learning.
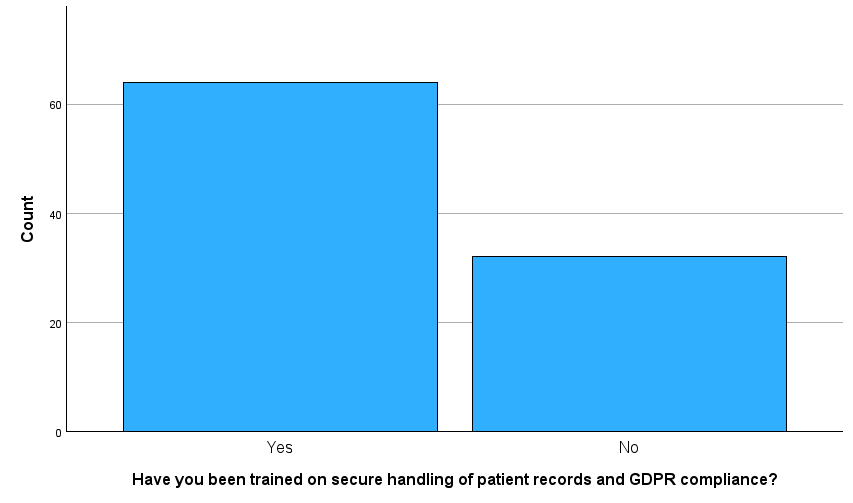
Figure 9 – Secure Handling Training
This chart shows a somewhat encouraging result: a majority of respondents reported receiving training on the secure handling of patient records and GDPR compliance. However, it also highlights that over one-third have not received such training, a significant gap considering the high legal and ethical standards expected in healthcare environments.
Given the strict requirements of GDPR for handling “special category data” like patient health records, this lack of training among a sizable minority poses a compliance and privacy risk. It also raises concerns about consistency in data protection education across healthcare and academic settings. Ideally this type of training should be universal and mandatory, especially for students and staff involved in clinical placements or digital health systems.
4. Risk Mitigation Strategies & Controls
4.1 Preventative Measures
Effective cybersecurity begins with proactive, layered defences. The HSE should implement technical, procedural and people focused controls to reduce risk exposure.
Technical Controls
A robust, defence-in-depth architecture is essential. This includes network segmentation, firewalls and endpoint protections to limit lateral movement. Sensitive data must be encrypted at rest and in transit. Patch management is vital for all systems, including medical devices, to address known vulnerabilities. Multi-Factor Authentication should be enforced for remote and privileged access. To manage mobile risks, BYOD policies and Mobile Device Management tools should be deployed. Offline, encrypted backups must be tested regularly to ensure recovery from ransomware events (ENISA, 2023).
Process & Policy Controls
Cybersecurity policies aligned with ISO/IEC 27001 and ISO 27799 should be adopted. Regular risk assessments and updates to the cyber risk register are critical. Systems should be hardened by eliminating unnecessary services and applying secure configurations. The principle of least privilege must guide access controls. Cybersecurity should also be embedded into procurement and change management processes to ensure secure adoption of new technologies.
Employee Controls
Human error remains a leading cause of breaches (Liginlal et al., 2008). All staff should receive role specific cybersecurity training, including phishing simulations, secure data handling and incident reporting. Currently, only 60% of healthcare organisations offer training to non-IT staff (ENISA, 2023). Training should be integrated into onboarding, refreshers and performance reviews. Also a “stop and think” culture should be promoted, supported by no-blame reporting protocols and basic insider threat safeguards.
Using frameworks like NIST CSF or ISO 27001 offers a structured, risk-based approach to prevention. While no system eliminates all threats, layered controls significantly reduce attack likelihood and impact.
4.2 Detective Measures
Since not all threats can be prevented, the HSE must implement robust detection mechanisms to identify malicious activity early and enable timely responses. This requires monitoring tools, data correlation and forensic capabilities across the IT environment (HHS, 2022).
Continuous monitoring of both endpoints and network traffic is essential. The HSE should deploy Intrusion Detection and Prevention Systems at network perimeters and internal segments, along with Endpoint Detection and Response tools on all servers and user devices. Modern EDR can detect behavioural anomalies (e.g. ransomware execution or privilege escalation) and automatically isolate affected endpoints (HSE, 2021).
For devices that cannot support agents like Internet of Medical Things, Network Detection and Response should be used to monitor traffic patterns. Centralised logging from critical systems must feed into a Security Information and Event Management platform. which correlates events and flags anomalies such as afterhours data transfers or repeated login failures (NIS2 Directive, 2022).
Healthcare specific machine learning based anomaly detection should be incorporated into the SIEM. Detection tools must be standardised across HSE’s fragmented infrastructure to ensure consistent monitoring.
Legacy systems should be protected with network segmentation and protocol level anomaly detection. Staff vigilance and physical safeguards further support early threat recognition (HSE, 2021).
Ultimately, comprehensive visibility covering logins, file changes and traffic is the goal. A coordinated use of IDS/IPS, EDR, SIEM and SOC dramatically enhances HSE’s threat detection capabilities and improves overall response readiness.
4.3 Corrective Actions & Incident Response
When a cyber threat is identified, the HSE must act swiftly to contain the incident, restore services and prevent recurrence, which is critical in healthcare where system downtime can directly impact patient safety (Carton et al., 2022).
Preparation is the first step in the incident response process. In accordance with established standards like ISO/IEC 27035 (Incident Management) (ISO, 2011) and NIST SP 800-61 (Computer Incident Handling Guide) (Cichonski, P et al, 2012)., the HSE should create and update a documented incident response strategy on a regular basis. Roles and responsibilities must be explicitly assigned, escalation triggers must be specified and legal reporting requirements, such as the NIS2 Directive’s 24-hour notification requirement (NIS2 2022), must be included in the plan.
Detection and analysis follow, using monitoring tools or staff reports. The Cyber Incident response team (CIRT) must validate the incident, assess its scope and determine an appropriate response.
Containment is the immediate priority. Affected systems should be isolated to prevent malware spread or data exfiltration. This may include disabling network connections or halting compromised applications.
The response team should eliminate malicious components, reimage or clean affected systems, reset compromised passwords and apply required fixes during the eradication process.
Prior to starting up again, the recovery phase focuses on verifying system integrity and restoring services using verified backups. To minimise clinical interruption, the HSE should give priority to vital systems such as diagnostic platforms and electronic health records (PwC, 2021).
A post incident review must be carried out after recovery to evaluate what happened, why it happened and how the reaction was managed.
IT professionals, clinical reps, legal counsel and communications staff should make up the incident response team, which should be a CIRT that operates around the clock.
It’s also critical to communicate incidents effectively. Relevant employees should be informed via prearranged internal alerts and where required, external communications must be sent to the public, law enforcement and regulators.
4.4 Compliance Measures
To ensure data security, service continuity and public trust the HSE must align its cybersecurity practices with evolving legal and regulatory obligations. Key frameworks include the NIS2 Directive, GDPR and emerging EU laws such as DORA and the AI Act (ENISA, 2023).
Under NIS2, the HSE must implement cybersecurity risk management, supply chain security and robust incident response. Major incidents must be reported within 24 hours, followed by a 72-hour update and a full technical report within one month (ENISA, 2023). The directive also introduces management accountability, making senior leadership legally responsible for failures.
GDPR mandates the protection of “special category” data, requiring technical and organisational measures such as encryption, access controls, breach notification within 72 hours and DPO oversight. DPIAs are needed for high-risk processing and failure to comply can lead to significant fines and reputational damage (HSE, 2024).
Though DORA applies primarily to finance, its principles on ICT resilience including disaster recovery and testing are applicable in healthcare. Likewise, the upcoming EU AI Act will govern high risk AI in clinical systems, requiring transparency, risk controls and human oversight (Future of Life Institute, 2025).
National standards from HIQA and the NCSC complement EU law, guiding areas like data retention, clinical audit and ICT security (NCSC, 2023).
Our survey (appendix 4) data underscores the need for a compliance awareness programme as shown in section 3.5. All staff must understand GDPR, NIS2 and their responsibilities in data handling and cyber hygiene.
4.5 Residual Risk, Risk Acceptance & Transfer
The HSE will continue to face residual risks, which are risks that persist after mitigation because of changing threats or innate weaknesses, even after implementing all practical cybersecurity solutions. It is impossible to completely eradicate cyber risk in the healthcare industry, where patient safety and service continuity are crucial. As a result, residual hazards need to be recognised, evaluated and controlled within the parameters of HSE’s risk appetite (ENISA, 2023).
It is necessary to record and evaluate residual risks such as insider threats, zero-day attacks and unsecured legacy systems, for their probability and potential effects on the provision of healthcare. For instance, any risk that can result in outages in vital systems, such as Electronic Health Records (EHRs), might surpass permitted limits and necessitate additional measures (HSE, 2021). On the other hand, non-essential systems, like those found in hospital cafeterias, may be permitted a greater degree of residual risk.
Network segmentation for medical equipment that cannot be patched or Internet of Things devices that cannot support a firewall are examples of compensatory controls that HSE may explicitly approve when some risks cannot be eliminated without excessive cost or technological feasibility. Clinical, IT and executive input must all be clearly included in the governance mechanism that makes these decisions (ENISA, 2023).
Contracting with Managed Security Service Providers (MSSPs) allows ongoing monitoring and aids in addressing internal skill gaps. Following the HSE ransomware incident in 2021, this strategy was advised, especially for smaller institutions with no internal resources.
The HSE can obtain emergency assistance from the Irish government because it is a national organisation. The Defence Forces and foreign allies assisted with recovery efforts during the 2021 cyberattack (HSE, 2021). The HSE must nevertheless exhibit preparedness and resilience in accordance with NIS2, even though this allows for some risk sharing (ENISA, 2023). Although outsourcing and insurance can lessen operational and financial strains, the HSE still bears final accountability.
5. Implementation and Monitoring
5.1 Implementation Plan
The HSE’s future plan from 2024 to 2030 indicates that it will adopt a structured, multi-phase rollout to implement its cybersecurity risk mitigation strategies based on current risk assessments by 2030. This approach ensures that security controls are effectively deployed while maintaining operational continuity across Ireland’s healthcare services.
Phase 1: Preparation involves establishing governance structures, securing executive buy-in, allocating budgets and updating relevant policies and procedures. The IT Security Team will lead planning efforts in coordination with HR, Information Governance and Risk & Compliance units.
Phase 2: Piloting focuses on trialling new controls in a controlled environment such as a single hospital. This phase will evaluate the effectiveness of solutions like network segmentation, identity management and threat detection systems. Pilots will also test staff training content. Cybersecurity engineers and local IT teams will deploy the tools, while Risk & Compliance monitors for policy alignment and operational disruption. A feedback report will inform any refinements before scaling (HSE, 2024).
Phase 3: Full Deployment entails the staggered rollout of technical and procedural safeguards across all regions. This includes firewall enhancements, MFA, EDR, incident reporting workflows and a centralized IT asset register. The HSE’s CISO and regional IT managers will oversee deployment and ensure compliance with post-Conti recommendations (HSE, 2024).
Phase 4: Training & Awareness ensures that all staff understand new policies and security behaviours. Mandatory training is delivered via the HSeLanD platform, which supports national staff development and compliance efforts across the HSE (HSE, 2025). Specialist modules will be delivered to IT and security personnel.
Phase 5: Audit & Validation confirms effective implementation. The Risk & Compliance unit, supported by internal audit, will assess control effectiveness. Findings will drive remediation and policy updates.
5.2 Monitoring and Review
The effectiveness of the HSE’s cybersecurity strategies must be continuously monitored to ensure they remain robust, compliant and responsive to emerging threats. Ongoing monitoring allows the HSE to validate that controls are working as intended, identify weaknesses and adjust where necessary.
Monitoring activities will involve the use of technical tools such as SIEM systems, EDR tools and Intrusion Detection Systems. These enable real-time threat detection, behavioural analysis and prompt response to suspicious activity. Regular vulnerability scans and patch management dashboards will ensure system updates are applied consistently.
In addition to automated monitoring, quarterly performance reviews should be conducted. These will assess key indicators such as:
- Number and severity of detected incidents
- Average response and recovery times
- Completion rates of cybersecurity awareness training
- Audit results and regulatory compliance levels
A formal risk management plan review should occur at least twice per year or following significant incidents or system changes. This process involves reassessing risks, updating the risk register, evaluating mitigation effectiveness and incorporating feedback from both technical and clinical staff.
All findings from monitoring and reviews must feed into a continuous improvement cycle, where outdated procedures are revised and new risks are addressed.
Responsibility for ongoing review lies with the CISO and HSE’s cybersecurity governance team. Their oversight ensures that monitoring results inform executive decisions and align with the HSE’s 2024–2027 Strategic Intent (HSE, 2024). Additionally, regular updates must be reported to the NCSC and Data Protection Commission (DPC) to maintain regulatory compliance under NIS2 and GDPR.
To ensure the effectiveness and continuous improvement of its cybersecurity programme, the HSE will adopt a structured metrics and reporting framework. Key performance indicators (KPIs) will track performance, inform strategic decisions and demonstrate compliance to internal and external stakeholders.
One of the primary indicators of organisational cybersecurity awareness is the staff training completion rate. This metric reflects the percentage of HSE personnel who have completed mandatory cybersecurity training via platforms such as HSeLanD. The HSE aims to achieve and maintain a completion rate exceeding 95% annually, significantly improving upon the 73% recorded in November 2024 (eHealth Ireland, 2024). A high completion rate supports legal obligations under data protection legislation and fosters a security aware workforce.
The vulnerability remediation rate measures the proportion of identified security issues resolved within service level agreements (SLA) timelines. A 95% remediation rate for critical vulnerabilities reflects effective risk management and responsiveness (NCSC, 2023).
Incident detection and response times measured as Mean Time to Detect (MTTD) and Mean Time to Respond or Recover (MTTR) provide insight into the efficiency of the SOC. Shorter response and containment times are indicative of a mature cybersecurity posture (Wiley, J. & Sons, 2024). These metrics, alongside others such as Mean Time to Contain (MTTC), are especially critical in healthcare settings where operational disruptions can impact patient care.
The audit compliance rate indicates alignment with internal policies and regulatory obligations. High compliance levels demonstrate governance maturity and reinforce accountability (UpGuard, 2024). To support ongoing monitoring, data will be collected through automated tools and reviewed by cybersecurity analysts. Sources include training systems, vulnerability scanners, SIEM platforms and audit records. This information will be visualised in dashboards, with summaries generated monthly for operational use and quarterly for governance reporting.
Reporting is tailored to the audience. Executive leadership and the HSE Board will receive quarterly reports highlighting trends, major incidents and strategic progress. The NCSC, as the regulatory authority under the NIS Directive, will be provided with an annual cybersecurity report and timely incident notifications where applicable. The Data Protection Officer (DPO) and internal governance committees will receive regular updates on GDPR-relevant metrics, such as staff training and breaches involving personal data. Operational teams will be issued department level reports to promote local accountability and continuous improvement.
This multi-tiered reporting will allow for real-time critical metrics, monthly for operations and quarterly for governance ensures transparency, responsiveness and sustained enhancement of the cybersecurity programme.
5.4 Continuous Improvement
At the HSE, cybersecurity risk management is a continuous and dynamic activity. The HSE is dedicated to promoting a culture of continuous improvement based on lessons learnt, stakeholder input, best practices and regulatory alignment, as risks and technology change.
Post-Incident Reviews and Lessons Learned
The HSE will carry out comprehensive post-incident reviews with IT Security and affected departments after any security issue (HSE, 2024). These will look at accomplishments, weaknesses and required steps such as updating the playbook or changing the firewall. Future policy, configuration and training upgrades will be informed by the findings, which were influenced by the independent 2021 cyberattack review. To avoid recurrence and foster an adaptable learning culture, key results will be disseminated throughout the organisation.
Staff Feedback and Engagement
Finding areas where employees want more cybersecurity assistance (such as phishing awareness) will be made easier with the use of surveys and the analysis of IT support tickets (Thomas, 2018). Training will be modified as necessary. Openness will be promoted by a no blame culture, which will enable mistakes or occurrences to serve as chances for learning for the entire company (Provera et al., 2010).
Maturity Assessments and Audits
Cybersecurity maturity will be tracked across domains by regular assessments utilising frameworks such as NIST or ISO 27001 (Identify, Protect, Detect, Respond, Recover). Such frameworks are suggested by the NCSC to help improve healthcare security. Priorities for investments and policies will be determined by independent or audited self-assessments. Progress on incident reviews, audits and assessments will be tracked via an action tracker (NCSC, 2023).
Adapting to Threats and Technology
The HSE will incorporate threat intelligence and emerging standards such as secure medical device practices and zero-trust models into its cybersecurity roadmap. Live recovery exercises will validate preparedness.
Policy and Governance Alignment:
All improvements will align with national and sectoral guidelines, including HIQA’s health IT standards and the NCSC’s Baseline Cybersecurity Standards. Governance structures, including oversight and performance goals, will ensure continuous alignment and long-term resilience.
6. Conclusion and Recommendations
6.1 Summary
Our studyidentified critical weaknesses in the HSE’s cybersecurity posture, undermining its ability to protect patient data and sustain essential healthcare services. A primary concern is the fragmented IT environment, an outcome of legacy system accumulation through decades of organisational mergers, making consistent security enforcement and oversight challenging (PwC, 2021).
Ransomware emerged as the most severe threat. The 2021 Conti attack encrypted over 80% of HSE systems and leaked 700GB of data, causing months of disruption (HSE, 2021). The absence of 24/7 monitoring tested backups and network segmentation significantly worsened the impact.
We identified concerns around data breaches and privacy. Weak access controls, limited encryption and poor audit logging which makes patient data vulnerable and a high risk, that is not in line with GDPR requirements. Also strengthening identity and access management, combined with better anomaly detection, is essential (PwC, 2021).
Insider threats, whether accidental or malicious, continue to pose risks. These account for a significant portion of healthcare breaches (Ponemon Institute, 2021). Targeted staff training, access reviews and behavioural monitoring are required.
Our research also confirmed that legacy systems continue to pose a substantial threat. At the time of the attack, over 40,000 devices were still running unsupported software like Windows 7 (PwC, 2021). While some upgrades have occurred as stated by the HSE professional, they are currently in the process of updating infrastructure to windows 11, many outdated systems remain operational across facilities.
Crucially, we found that prior to 2021 the HSE previously lacked a centralised cybersecurity leadership structure and a formal incident response plan, both of which contributed to the scale of the breach. Addressing these governance gaps is essential to achieving long-term cyber resilience.
6.2 Recommendations
To strengthen cybersecurity the HSE should implement a balanced strategy focused on technical defences, governance and organisational culture. These recommendations are informed by the 2021 Conti attack, NHS incidents and regulatory requirements.
Technical Measures
The HSE must prioritise MFA, network segmentation and EDR tools to detect and block intrusions. The absence of real time monitoring in 2021 allowed attackers to persist undetected (HSE, 2021). Strong patch management, system isolation and regularly tested offline backups are critical for resilience and recovery. Formal disaster recovery plans should ensure minimal disruption to patient care.
Governance and Compliance
Practices must align with NIS2 and GDPR, particularly in incident response, access control and vendor oversight. NIS2 requires executive accountability, making leadership engagement and cyber governance essential.
Training and Culture
Given that human error remains a leading threat, the HSE should expand role specific training, phishing simulations and incident drills. Promoting a mindset that “cybersecurity is patient safety” will help embed responsibility at all levels.
Emerging Threats and Continuous Improvement
Proactive measures must address IoMT vulnerabilities and supply chain risks. A zero-trust architecture, enhanced vendor audits and regular ethical hacking should be adopted. A cycle of performance metrics, feedback and reassessment will support long-term improvement and adaptive security posture.
6.3 Future Work
While this study provides a solid foundation for improving cybersecurity within the HSE, continuous refinement is essential to address evolving threats and operational challenges. Future work should focus on the following areas:
Evolving Threats and Risk Assessment
Cyber threats such as Ransomware-as-a-Service, AI-driven attacks and zero-day exploits are advancing rapidly. Incidents like the 2023 MOVEit supply-chain breach (McKeon, 2024) highlight the need for regular updates to the HSE’s risk register using threat intelligence and healthcare-specific incident trends (ENISA, 2023). Scenario planning e.g. simultaneous ransomware attacks on multiple hospitals can help identify preparedness gaps and refine incident response strategies (Ahmed, 2023).
Technical Audits and Testing
Future efforts should include in depth audits of infrastructure, access logs and medical devices. Penetration testing and red teaming by external experts will support more accurate vulnerability assessments and test the effectiveness of current controls (Rehberger, 2020).
Stakeholder Engagement and Human Factors
The convenience sample of students we used for our cybersecurity awareness survey restricts its generalisability. Surveys and interviews with patients as well as HSE staff from the clinical, administrative and IT domains should be a part of future research. This would give a more accurate picture of cybersecurity behaviour and knowledge. A cyber-aware culture can be successfully fostered by assessing the long-term effects of security awareness training.
Policy Alignment and Impact Assessment
Further research should monitor the HSE’s compliance with new laws like NIS2 and changes to GDPR (HSE, 2024). Assessing outcomes such as improved breach response and reduced downtime is vital. It is also critical to ensure that security-by-design and privacy-by-default are integrated into expanding systems like EHRs and HIEs (Bowman, 2013).
Ahmed, N.-B. (2023) Cybersecurity in healthcare system : Evaluation and assessment of the Cybersecurity readiness of Mobile Field Hospital’s resilience, theses. Available at: https://theses.hal.science/tel-04097342/ (Accessed: 17 April 2025).
Bowman, S. (2013) Impact of electronic health record systems on Information Integrity: Quality and Safety Implications, Perspectives in health information management. Available at: https://pmc.ncbi.nlm.nih.gov/articles/PMC3797550/ (Accessed: 17 April 2025).
Carton, Dr.M. et al. (2022) A mixed methods analysis of the effectiveness of the patient safety risk mitigation strategies following a Healthcare ICT failure, cyber-study-report.pdf. Available at: https://www.hse.ie/eng/about/who/nqpsd/qps-intelligence/qps-intelligence-reports/cyber-study-report.pdf (Accessed: 19 May 2025).
Cichonski, P., Millar, T., Grance, T. and Scarfone, K., (2012). Computer Security Incident Handling Guide (SP 800-61 Rev. 2). [online] Gaithersburg, MD: National Institute of Standards and Technology. Available at: https://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-61r2.pdf
Clarke, M. & Martin, K. (2024) ‘Managing cybersecurity risk in healthcare settings’, Healthcare Management Forum, 37(1), pp. 18. doi:10.1177/08404704231195804.
eHealth Ireland (2024) Safeguarding the HSE – The Importance of Cybersecurity Awareness. Available at: https://www.ehealthireland.ie/news-media/news/2024/safeguarding-the-hse-the-importance-of-cybersecurity-awareness/ [Accessed 17 Apr. 2025].
ENISA (2023) Health threat landscape, ENISA. Available at: https://www.enisa.europa.eu/publications/health-threat-landscape (Accessed: 17 April 2025).
Future of Life Institute. (2025) EU Artificial Intelligence Act. Available at: https://artificialintelligenceact.eu/ (Accessed: 17 April 2025).
Harmony Healthcare IT. (2024) Six Ways Legacy Systems Expose Healthcare Organizations to Security Risks. Available at: https://www.harmonyhit.com/six-ways-legacy-systems-expose-healthcare-organizations-to-security-risks/ (Accessed: 27 February 2025).
Health Service Executive (HSE) (2024) Cyber Security Statement of Strategic Intent 2024-2027. eHealth Ireland. Available at: https://www.ehealthireland.ie/media/mdyjwfgg/hse-cyber-security-statement-of-strategic-intent-2024-2027.pdf (Accessed: 20 February 2025)
Health Service Executive (HSE). (2021) Conti cyber-attack on the HSE: Full report. Available at: https://www.hse.ie/eng/services/publications/conti-cyber-attack-on-the-hse-full-report.pdf (Accessed: 27 February 2025).
HIPAA Journal (2024) Healthcare data breaches of 500+ records (2009-2023). Available at: https://www.hipaajournal.com/security-breaches-in-healthcare/ (Accessed: 27 February 2025).
Hopkin, P. (2018) Fundamentals of Risk Management: Understanding, Evaluating and Implementing Effective Risk Management, 5th edn, Kogan Page, London.
HSE, 2025. About HSeLanD. [online] Health Service Executive. Available at: https://www.hseland.ie/dash/Account/About [Accessed 17 Apr. 2025].
International Organization for Standardization (2011). ISO/IEC 27035:2011 Information technology — Security techniques — Information security incident management. [online] Geneva: ISO. Available at: https://www.iso.org/obp/ui#iso:std:iso-iec:27035:ed-1:v1:en:fn:7 [Accessed 23 May 2025].
International Organization for Standardization (2016) ISO 27799:2016 – Health informatics – Information security management in health using ISO/IEC 27002. Available at: https://www.iso.org/standard/62777.html [Accessed 3 Apr. 2025].
Klappholz, S. (2024) ‘The HSE cyber attack was a landmark event in Ireland – has it learned from the experience?’, IT Pro, 8 May. Available at: https://www.itpro.com/security/ransomware/the-hse-cyber-attack-was-a-landmark-event-in-ireland-has-it-learned-from-the-experience (Accessed: 27 February 2025).
Kroll (2025) Data Breach Outlook 2025. Available at: https://www.kroll.com/en/insights/publications/cyber/data-breach-outlook-2025 (Accessed: 20 February 2025)
Liginlal , D., Sim , I. and Khansa, L. (2008) How significant is human error as a cause of privacy breaches? an empirical study and a framework for error management, Computers & Security. Available at: https://www.sciencedirect.com/science/article/pii/S0167404808001181 (Accessed: 19 May 2025).
McKeon, J. (2024) Insider threats in healthcare remain prevalent: TechTarget, Healthtech Security. Available at: https://www.techtarget.com/healthtechsecurity/news/366594060/Insider-threats-in-healthcare-remain-prevalent#:~:text=%E2%80%9CFrom%20year%20to%20year%2C%20we,still%20remain%20successful%2C%E2%80%9D%20Verizon%20noted (Accessed: 17 April 2025).
National Cyber Security Centre (2023) Vulnerability Management Guidance. Available at: https://www.ncsc.gov.uk/collection/vulnerability-management/guidance [Accessed 17 Apr. 2025].
National Cyber Security Centre (NCSC), 2023. NIS2 Guide. [pdf] Available at: https://www.ncsc.gov.ie/pdfs/NCSC_NIS2_Guide.pdf [Accessed 20 February 2025].
NCSC (n.d.) Introduction to the cyber assessment framework, NCSC. Available at: https://www.ncsc.gov.uk/collection/cyber-assessment-framework/introduction-to-caf (Accessed: 17 April 2025).
NIS2 (2022) Directive – 2022/2555 – en – EUR-lex, EUR. Available at: https://eurlex.europa.eu/eli/dir/2022/2555/oj
NIST (2018) Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1. National Institute of Standards and Technology, Gaithersburg, MD.w
Peltier, T.R. (2016) Information Security Risk Analysis, 3rd edn, CRC Press, Boca Raton, FL.
Ponemon Institute (2021) ‘Cost of a Data Breach Report: Healthcare Edition’. Available at: https://www.ponemon.org (Accessed: 25 February 2025).
Provera, B., Montefusco, A. and Canato, A. (2010) A ‘no blame’ approach to organizational learning – provera – 2010 – british journal of management – wiley online library. Available at: https://onlinelibrary.wiley.com/doi/abs/10.1111/j.1467-8551.2008.00599.x (Accessed: 17 April 2025).
Rehberger, J. (2020) Cybersecurity attacks – red team strategies, Google Books. Available at: https://books.google.ie/books?hl=en&lr=&id=gtDaDwAAQBAJ&oi=fnd&pg=PP1&dq=Engaging%2Bexternal%2Bcybersecurity%2Bprofessionals%2Bto%2Bcarry%2Bout%2Bred-team%2Bexercises%2Band%2Bpenetration%2Btesting%2Bcould%2Bfurther%2Bexpose%2Bweaknesses%2Band%2Btest%2Bthe%2Beffectiveness%2Bof%2Brecent%2Bcontrols&ots=nhSv408SdA&sig=C5WSWVNI6uWAehry5nkcmQXQjx8&redir_esc=y#v=onepage&q&f=false (Accessed: 17 April 2025).
Schiliro, F. (2022) ‘Towards a Contemporary Definition of Cybersecurity’, arXiv. Available at: https://arxiv.org/pdf/2302.02274 (Accessed: 20 February 2025).
The European Union Agency for Cybersecurity (ENISA). (2023). Network and Information Systems Directive 2 (NIS2). [online] Available at: https://www.enisa.europa.eu/topics/awareness-and-cyber-hygiene/network-and-information-systems-directive-2-nis2 [Accessed 3 Apr. 2025].
Thomas, J. (2018) Individual cyber security: Empowering employees to resist spear phishing to prevent identity theft and ransomware attacks, SSRN. Available at: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3171727 (Accessed: 17 April 2025).
UpGuard (2024) 7 Incident Response Metrics and How to Use Them. Available at: https://securityscorecard.com/blog/how-to-use-incident-response-metrics [Accessed 17 Apr. 2025].
Verizon. (2022) 2022 Data Breach Investigations Report. Verizon. Available at: https://www.verizon.com/business/en-gb/resources/2022-data-breach-investigations-report-dbir.pdf (Accessed: 25 February 2025).
Whitman, M.E. & Mattord, H.J. (2021) Principles of Information Security, 7th edn, Cengage Learning, Boston.
Wiley, J. & Sons (2024) ‘Chapter 17: Risk Management and Privacy’, in CompTIA Security+ SY0-701, 9th Edition. Hoboken, NJ: John Wiley & Sons.
Appendices
Appendix 1 – Detailed Risk Register/Matrix
|
ID |
Risk Statement |
Risk Causes |
Risk Impacts |
Likelihood |
Impact |
Score |
|
1 |
Successful phishing attack leads to unauthorized access and installation of malware (e.g., ransomware). |
Insufficient cybersecurity awareness training; lack of robust email filtering and multi-factor authentication (MFA); inadequate monitoring and detection capabilities. |
Major disruption to healthcare delivery services; loss of patient data confidentiality; significant financial and reputational damage; potential violation of GDPR compliance leading to fines. |
3 |
3 |
9 |
|
2 |
Exploitation of vulnerabilities in legacy/unpatched systems resulting in privilege escalation or lateral movement by attackers. |
Reliance on outdated technology (Windows 7, unsupported software); inadequate patch management processes; limited internal segmentation and monitoring. |
Extensive compromise of IT systems; widespread operational downtime affecting patient care; elevated remediation costs; exposure of sensitive health information. |
3 |
3 |
9 |
|
3 |
Data breach or exfiltration of sensitive patient data through compromised credentials or unauthorized cloud services. |
Weak access controls and limited implementation of MFA; insufficient network monitoring; lack of robust data encryption; poor vendor security management and monitoring. |
Breach of patient confidentiality leading to GDPR violations; significant legal liabilities and financial penalties; severe damage to public trust; long-term reputational harm. |
3 |
3 |
9 |
|
4 |
Third-party vendor compromise introduces malware into HSE’s network (supply chain attack). |
No coordinated vendor risk management processes: inadequate cybersecurity vetting and monitoring of third-party vendors and connected services; insufficient contractual security requirements. |
Potentially severe compromise of internal systems; extended disruption of critical healthcare services; loss of sensitive information; regulatory fines due to GDPR and NIS2 violations; indirect financial losses from service interruptions. |
2 |
3 |
6 |
|
5 |
Intentional or accidental manipulation of critical healthcare data affecting patient diagnoses or treatments (Integrity attack). |
Insufficient data integrity controls and monitoring; inadequate access control for critical medical databases; limited use of audit logging and anomaly detection. |
Risk to patient safety through incorrect medical decisions; liability and regulatory implications; reduced public confidence in HSE systems; financial and reputational harm. |
1 |
3 |
3 |
Likelihood & Impact scale: (Likelihood x Impact = Score)
Likelihood:
1 (Low): Rare
2 (Medium): Possible
3 (High): Likely
Impact:
1 (Low): Minimal impact
2 (Medium): Moderate operational impact
3 (High): Significant operational disruption, major reputational or financial damage
Appendix 2 – ISO Risk Register
|
ID |
Impact |
Likelihood |
Risk Score |
Risk Level |
Risk Owner |
Risk Treatment Plan |
Status |
Justification |
|
1 |
3 (Major) |
3 (Likely) |
9 |
High |
CISO |
Conduct phishing awareness training; enforce MFA; enhance email filters and detection tools. |
Open |
Needs MFA rollout. |
|
2 |
3 (Major) |
3 (Likely) |
9 |
High |
IT Security Lead |
Upgrade legacy systems; implement patching policy; segment internal network. |
Open |
High priority system audit ongoing. |
|
3 |
3 (Major) |
3 (Likely) |
9 |
High |
Data Protection Officer |
Enforce MFA; encrypt data; monitor cloud access; audit vendors. |
Open |
Vendor compliance under review. |
|
4 |
3 (Major) |
2 (Possible) |
6 |
Medium |
Procurement Manager |
Implement third-party risk assessments; revise contracts to include cybersecurity clauses. |
Open |
Supply chain assessment planned. |
|
5 |
3 (Major) |
1 (Unlikely) |
3 |
Low |
Clinical Systems Admin |
Deploy anomaly detection; restrict access; enable audit logging. |
Open |
Log monitoring tools in evaluation phase. |
Appendix 3 – Interview Questions
Questions based on your experience at HSE for the ICT Professional
- What immediate impact did the 2021 cyber-attack have on HSE hospital operations?
- How did the hospital’s IT team respond to contain the incident?
- Did the Hospital/HSE have a formal Incident Response Plan at the time? If so, was it effective?
- In your opinion what were the key weaknesses in cybersecurity that made the attack possible?
- Did the hospital receive external support from cybersecurity agencies (e.g., NCSC, private firms, or government)?
- What long-term or significant changes were implemented in cybersecurity following the attack?
- How have the HSE cybersecurity policies and training programs changed since the attack?
- In your opinion will the HSE strategic statement for 2024-2027 protect the HSE from another attack? Will it be implemented by 2027?
- In your opinion how will NIS2 affect the HSE?
- Does the HSE receive enough funding to meet cybersecurity requirements?
- Does the HSE have frameworks in place to improve its cybersecurity? If so, what are they?
- Should Medical/Nursing student receive cybersecurity training as part of their curriculum?
- What is the current state of the HSE ICT infrastructure?
Appendix 4 – Student Survey Questions
Healthcare Cyber Security Awareness
1. What is your current year of study?
1st Year
2nd Year
3rd Year
Final Year
Postgraduate
3.Have you received any formal cybersecurity training as part of your curriculum?
Yes
No
4.How frequently do you use hospital or university systems that require login credentials?
Daily
Weekly
Monthly
Never
5.On a scale of 1 to 5, how confident are you in your understanding of cybersecurity in healthcare? (1= Not Confident, 5 = Very Confident)
|
|
1 |
2 |
3 |
4 |
5 |
|
|
|
|
|
|
|
6.Have you heard about the 2021 HSE Conti ransomware attack?
Yes
No
7.Have you ever received training on how to recognise phishing emails?
Yes
No
8.If you received an email from “IT Support” asking you to reset your password by clicking a link, what would you do?
Open the link
Report it
Ignore it
Other
9.If you suspected a phishing email, what would be your first response?
Delete it and ignore it
Click on the link to verify it
Report it to the IT team
Forward it to a friend for advice
10.Have you been trained on secure handling of patient records and GDPR compliance?
Yes
No
11.Would you be interested in cybersecurity training tailored to healthcare professionals?
Yes
No
12.In your opinion, briefly explain how you think cybersecurity awareness could be improved among healthcare professionals
13.Do you share log in credentials with other members of staff?
Yes
No
Don’t know
14.How often do you change your password?
Often
Never
Sometimes